
I the past several years, open source Linux distributions have emerged as a rock solid platform for production data centres with mission-critical IT infrastructure. This growth has prompted security hackers to try exploits to “own” Linux systems; the most serious being rootkits, which are far more dangerous than viruses and Trojans. We covered the basics in the previous article in this series — please have a read for some background information.
About Chkrootkit
chkrootkit is a collection of tools to detect the presence of rootkits, and is a gift to Linux systems administrators for two specific reasons:
- it is a free, open source utility, and available for multiple distros,
- it detects almost all the latest rootkits out there, since the open source community of contributors keeps it up to date.
Over time, the Chkrootkit scan engine has also improved, making it faster, which is especially useful in performing detailed kernel checks against a number of supported kit detections.
A few great features of chkrootkit are that it detects more than 60 old and new kits, is capable of detecting network interfaces in promiscuous mode, can efficiently detect altered lastlog and wtmp files (which in turn alerts admins about intrusions), has easy command-line access with straightforward options, and has a verbose output mode to help admins automate tasks.
chkrootkit uses C and shell scripts to perform a detailed process check, and scans systems binaries to detect kit signatures. Upon detection, in most cases, it can remove rootkits too. It also has a few algorithms that can report trends of a possible rootkit, even if it is not yet officially supported. The following lists the chkrootkit internal programs and what each of them do.
| chkrootkit Program | Purpose |
| chkrootkit | Main script to check for tampered system files |
| strings.c | Detects and performs string replacement |
| ifpromisc.c | Checks network interface for promiscuous mode |
| chklastlog.c, chkwtmp.c | Checks if lastlog and wtmp entries are deleted |
| chkproc.c, chkdirs.c | Checks for Linux kernel module-based Trojans |
Installation
Installation is straightforward on most distributions distributions. You can download the most recent tarball to a temporary folder. It is recommended that you perform an MD5 check, and then decompress the tarball using the following command: tar xfvz chkrootkit.tar.gz. Change to the extracted directory, and compile it with make sense.
In fact, installation is even simpler on Debian/Ubuntu, simply run sudo apt-get install chkrootkit.
Usage
The very first step recommended after installing chkrootkit is to run ifpromisc. This checks whether network interfaces are in promiscuous mode, which should not be the case unless the system is infected with a rootkit prior to installation.
Once this check is done, the next step is to run the tool without any commandline options. Figure 1 shows how a typical Ubuntu system is scanned and checked for various supported anomalies and rootkits.
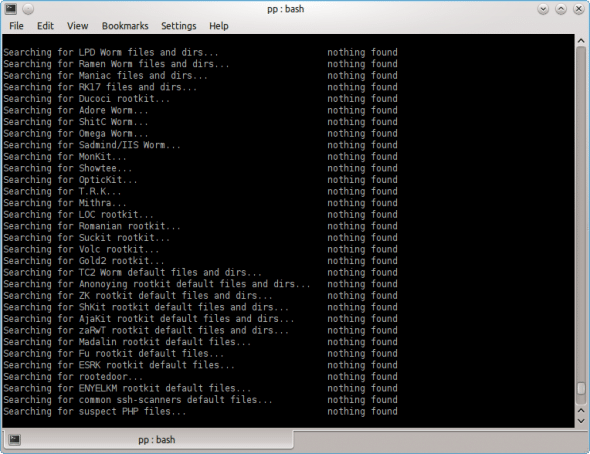
Figure 2 shows how Chkrootkit checks all kernel processes and system files, based on an internally stored checklist.
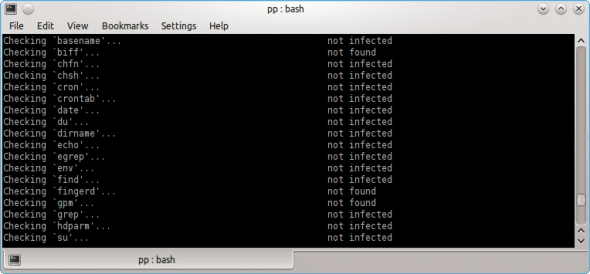
If any common OS utility (such as fingerd, as seen in Figure 2) is not detected, it reports this, so that administrative scripts can check whether a file that should normally be present has been deleted.
Though running chkrootkit without any command-line options is usually sufficient, systems administrators may want more flexibility to script it. The following table describes a few command options with examples.
| Option | Explanation | Example |
-l |
Lists the tests supported | >chkrootkit -l |
[testname] |
Scans for a specific test | Check Sniffer command for “ps” Trojan: >chkrootkit ps sniffer |
-x |
Expert mode (displays each action taken on each file scanned) | >chkrootkit -x | more |
-q |
Quiet mode. Only displays if a binary is found to be “Infected” | >chkrootkit -q |
-r |
Uses specified dir as root dir. Useful in scanning a suspicious machine from a healthy one. Also useful in scanning mounted volumes. | Scans a volume mounted under, say “mnt1”:>chkrootkit -r /mnt1 |
It is also important to understand how chkrootkit displays output. Typically, phrases such as “Not found” or “Not infected” are displayed. When a rootkit is found, or if the presence of a rootkit is suspected, the output highlights it with “INFECTED”, or “The following suspicious files or directories have been found.” Please refer to Figure 3, which shows a Python script being reported as suspicious.
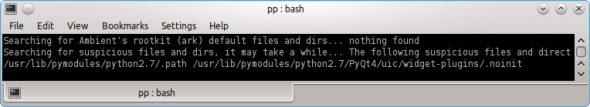
These outputs can be captured to a text file log, or parsed with a grep command to remove the clutter and only concentrate on important messages. Using –q is possible, but it can suppress suspect items, which may not be a good idea.
What if a rootkit is found?
chkrootkit detects rootkits, but does not remove those. Upon finding a rootkit on a system, the first thing to do is to remove it from the network, to avoid further spread. To remove a rootkit in the cleanest way, we need to back up and rebuild the entire system — which, however may not always be possible. Another approach is to study the detected rootkit thoroughly, and perform actions to remove it based on its way of intrusion and working.
Many rootkits can be removed manually; however there are a few which need only the cleanest approach. To improve detection accuracy, it is advised to run chkrootkit from a known healthy system, against all servers in the farm.
Integrating Chkrootkit for admin tasks
System administrators are strongly advised to use chkrootkit in their daily administrative tasks. By using an appropriate command-line option, we can create a script to have verbose output, and dump it into a log file which can be further parsed to look for anomalies.
This script can be set (using a cron job) to be run on a daily schedule. Over time, the script can be tuned further to remove false alarms generated by suspicious files and report only real problems. Another cron job can be scheduled more frequently, to have chkrootkit detect if network interfaces are in promiscuous mode. This is essential because usually a rootkit attack starts by tampering with network configuration.
Further scripting can be done to create a list of servers in the farm to be scanned, and consolidate their outputs, and alert or report administrators accordingly.
Summary
Rootkits are a serious threat to modern data centres. It is essential for IT management to have a definite means to detect them and take responsive action. chkrootkit is a fast and effective scanning tool for just this purpose. Its command line options help to automate runs on a periodic basis, which is good for administrators.













































































