Tag: TCP/IP
Cyber Attacks Explained: Packet Crafting
Protect your FOSS-based IT infrastructure from packet crafting by learning more about it.
In the previous articles in this series, we explored common infrastructure vulnerability...
FreeBSD 9.0 — Fast, Safe and Completely Geeky
Yes, I know, we're kind of late in getting this article out, but that's because there was a lot of things that were added...
Guard Your Network with IPCop, Part 3: Block Outgoing Traffic
The first article in the series discussed IPCop 1.4.21, its basic installation and configuration. Though an excellent firewall distro, basic IPCop has limited functionality....
Cyber Attacks Explained: Network Sniffing
In earlier articles in this series, we have explored denial of service attacks and packet spoofing. This month, let us focus on a wider...
The Socket API, Part 5: SCTP
This article on socket programming deals with the Stream Control Transmission Protocol (SCTP).
Similar to TCP and UDP, SCTP provides some features of both. It...
Guard Your Network with IPCop, Part 1: Installation Basics
The classic version of IPCop 1.4.20, which was released on July 24, 2008, was immediately upgraded to the 1.4.21 ISO installer. The much awaited...
Cyber Attacks Explained: Packet Spoofing
Last month, we started this series to cover the important cyber attacks that impact critical IT infrastructure in organisations. The first was the denial-of-service...
Storage Management using Openfiler, Part 4
In the previous article in the series on Openfiler, we discussed configuring RAID. Here, we will proceed with the installation and configuration of iSCSI....
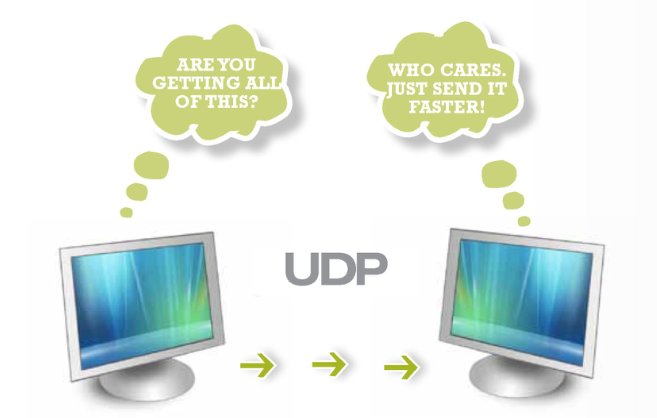
The Socket API, Part 4: Datagrams
Let's try to develop server clients using UDP, the protocol behind some important services like DNS, NFS, etc.
UDP, the User Datagram Protocol, is a...
Cyber Attacks Explained: DoS and DDoS
With this article, we begin a new series on the major kinds of cyber attacks that weaken the IT security infrastructure within organisations. With...