Tag: network security
Top 5 Open Source Firewalls
Firewalls protect your system from malicious attacks and promote privacy. This article lists the best Open Source firewalls you can choose from for your...
Top 10 Open Source Network Security Tools for Web Apps
Whether you are part of a startup dipping your toes into the field of Web apps or a full blown MNC working on multiple...
Emergence of Pen Testing in Cyber Security
A penetration test is basically a simulated cyber attack against the system in order to check it for vulnerabilities. It is also called ‘ethical...
The Most Popular Security Assessment and Server Hardening Tools
Enterprises require high levels of security for their computer systems. A server attack or a malware intrusion can cause incalculable damage. Prudence, therefore, is...
What’s New in Nmap 6
Nmap is Hollywood's most famous "hacking" tool that has featured on numerous blockbusters. It was originally written to find hosts in a network thus...
Advanced Nmap: A Recap
This final article in the series consolidates information from the previous articles, looks at NMap's future possibilities, and at the new tools from the...
Nessus with Metasploit — Track and Hack
Networks play an important role in a sysadmin's life. But have you ever wondered about the security of your network, or tried to find...
Advanced Nmap: NMap Script Scanning
In previous articles, we have studied NMap in great detail, including live scanning a firewall and verifying the recommendations. Now, it's time to study...
Advanced Nmap: Scanning Firewalls Continued
The previous article detailed methods to scan an IPCop-based firewall in a test environment. The scan output revealed several open ports, which could lead...
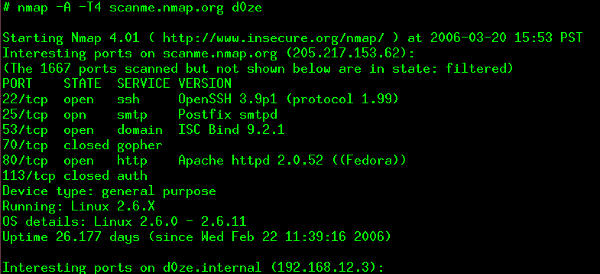
Advanced Nmap: Scanning Firewalls
After four articles on Nmap , which explained a number of command-line options for scan technique specification, target specification, port specifications, host discovery, evasion...