Tag: intrusion-detection systems
Use the Built-in Security Features in Your FOSS Distro
When it comes to securing network infrastructure, the trend is to invest in commercial-grade appliances. Sadly, security designers tend to ignore the built-in security...
Cyber Attacks Explained: Packet Crafting
Protect your FOSS-based IT infrastructure from packet crafting by learning more about it.
In the previous articles in this series, we explored common infrastructure vulnerability...
Cyber Attacks Explained: Network Sniffing
In earlier articles in this series, we have explored denial of service attacks and packet spoofing. This month, let us focus on a wider...
Rootkits: The Enemy Within
While it was assumed in the past that viruses only targeted Windows, hackers targeting the FOSS world proved this wrong. A rootkit on a...
Best Practices in Network Security Monitoring
This article details the best practices organisations can follow to strengthen their network monitoring procedures, and also talks about a few FOSS products that...
Securing Apache, Part 8: DoS & DDoS Attacks
In this part of the series, we focus on DoS/DDoS attacks, which have been among the major threats to Web servers since the beginning...
Advanced Nmap: FIN Scan & OS Detection
Nmap is a fantastic tool, and I just can't refrain from praising it, every time I use it. The earlier articles in this series...
The Importance of Intrusion Prevention Systems
In today's fast-changing IT world, even the best available security is insufficient for the latest vulnerabilities in various products, and against malware/attacks created to...
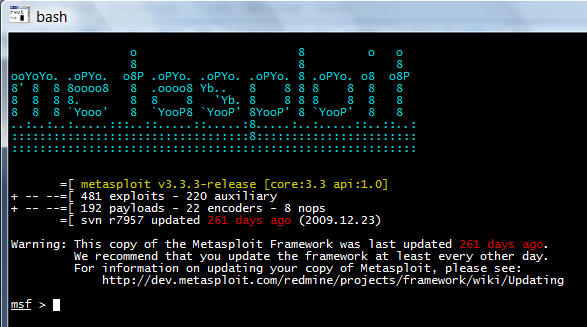
Metasploit: The Exploit Framework for Penetration Testers
Today, the Metasploit Framework is considered the single most useful auditing tool that is freely available to security professionals and penetration testers. It has...
Securing Apache, Part 1: The Basics
Targeted at readers with Web security concerns, information security experts, systems administrators and all those who want to jump-start their careers in Web security,...