Tag: Ethernet
Easy and Secure File Transferring with WinSCP
Easy and Secure File Transferring with WinSCP
Working in a multi-OS environment often requires transferring files between two machines running entirely different operating systems. Even...
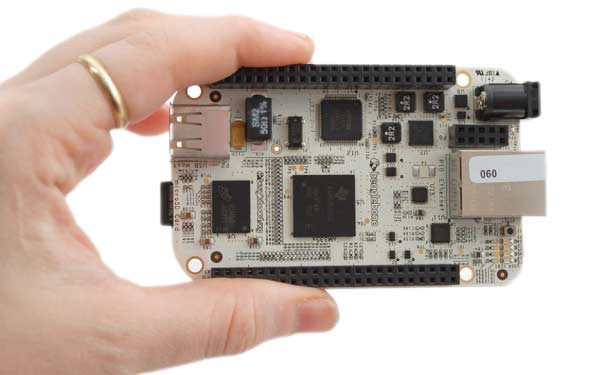
Getting Started with the Beaglebone
The article aims to make a novice well-versed with the Beaglebone. The article gives a brief overview of the Beaglebone and how to toggle...
Going Virtual With OpenVZ
This article is an introduction to OpenVZ, an open source container-based virtualisation solution for Linux.
In computing, virtualisation is the creation of a virtual version...
Bandwidth Throttling with NetEM Network Emulation
NetEM (Network Emulation) provides functionality for testing protocols, by emulating the network properties of wide-area networks. This article describes the use of NetEM in...
Virtualisation Face-off: Qemu, VirtualBox, VMware Player and Parallels Workstation
In this article, we take a look at four of the most well known and commonly used virtualisation software for Linux.
When it comes to...
Cyber Attacks Explained: Packet Crafting
Protect your FOSS-based IT infrastructure from packet crafting by learning more about it.
In the previous articles in this series, we explored common infrastructure vulnerability...
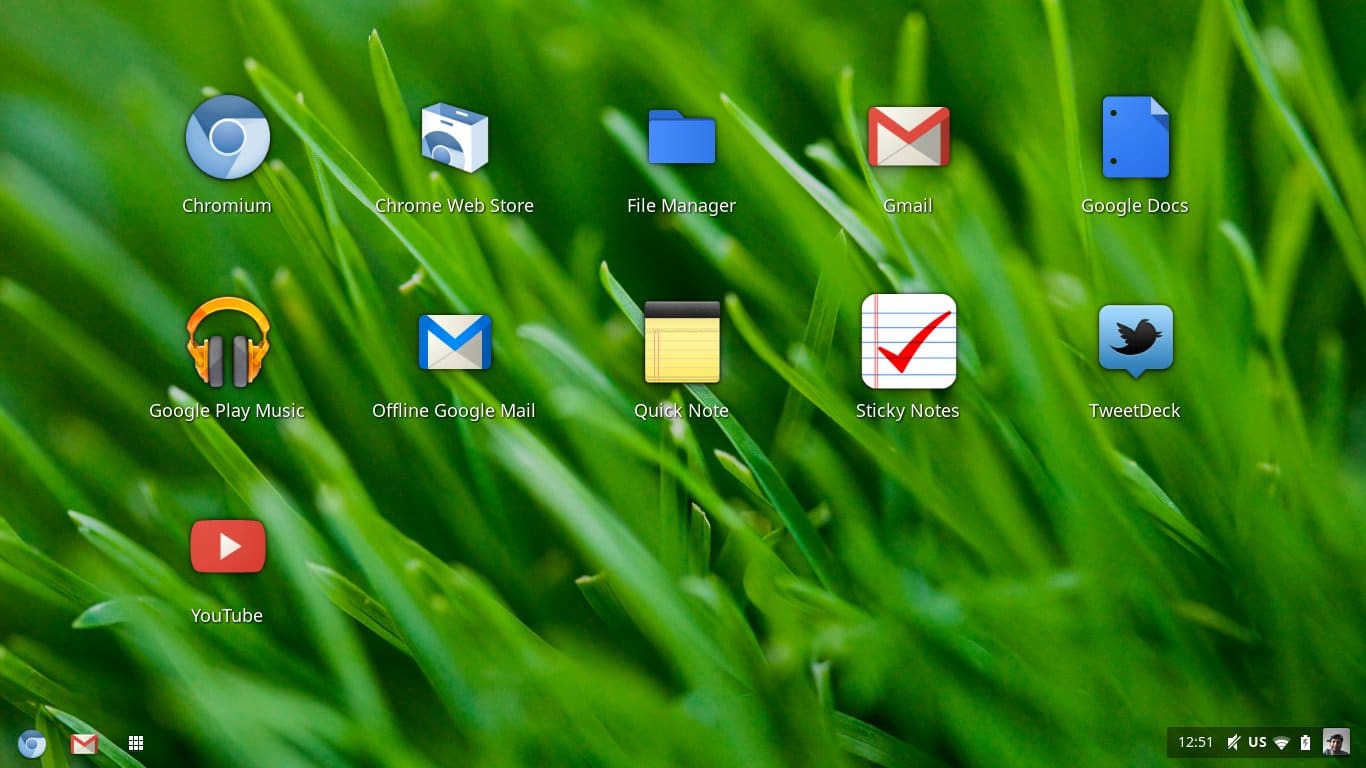
Chrome OS: Good Gimmicks, But What Else?
I don't own a Chomebook; and it's been a couple of years since I've tried the Chrome OS -- a pre-alpha release or something....
Cyber Attacks Explained: Network Sniffing
In earlier articles in this series, we have explored denial of service attacks and packet spoofing. This month, let us focus on a wider...
Guard Your Network with IPCop, Part 1: Installation Basics
The classic version of IPCop 1.4.20, which was released on July 24, 2008, was immediately upgraded to the 1.4.21 ISO installer. The much awaited...
Cyber Attacks Explained: Packet Spoofing
Last month, we started this series to cover the important cyber attacks that impact critical IT infrastructure in organisations. The first was the denial-of-service...