WordPress remains the most popular content management platform today. However, organisations very often forget to update their websites with the latest version, putting them at a security risk.
Content is king! Content is where I expect much of the real money will be made on the internet, just as it was in broadcasting,” said Bill Gates nearly 30 years ago. Today, content is at the centre of a business’s digital transformation and the customer experience. An organisation must therefore onboard technology platforms that help manage this content, and there is a range of content management systems (CMS) that it can choose from, open source or otherwise.
There has been a lot of evolution in content management systems, be it open source or commercial software. This is one area where open source has not lost its lustre, with frameworks and platforms like WordPress, Joomla and Drupal being the most popular, among many others. Sixty-five per cent of all websites that exist today use these three platforms. That speaks for the robustness these platforms bring to all kinds of use cases across industry domains for small and large organisations. Figure 1 shows the ease of use of the open source CMS platforms that are widely adopted.
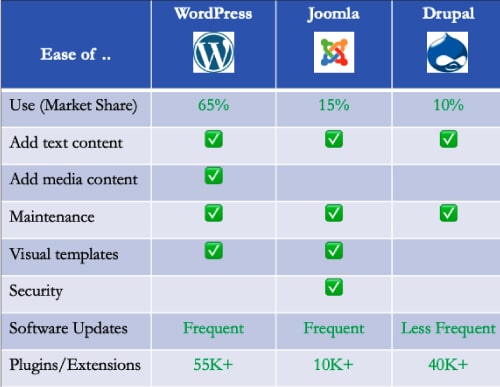
Apart from being available for about two decades, these popular platforms have many similarities. They are all based on PHP as a programming language and use MySQL for database storage. All of them use templates and themes backed by robust developer communities that offer rich plugins, modules, and extensions to complement the features in the core platform. All the platforms have feature-rich access controls that offer flexibility and protection, supporting most use cases with different user permissions and capabilities. And they have easy-to-use flexible user interfaces for quick extensibility and customisation.
WordPress, being the most adored platform, has the most plugins, and the largest developer community and market share. However, the popularity and openness of this platform, coupled with its simplicity, attracts hackers to exploit the weakness or poor security of the websites that use it. Although security is a big challenge and concern, staying ahead of the curve by understanding known vulnerabilities and addressing them with appropriate processes does help to keep hackers at bay.
It is critical to install the most up-to-date software version for the core platform along with all the plugins, extensions, and modules. The same applies to WordPress. Over 50 per cent of all sites hosted on WordPress that are hacked are on ‘outdated’ versions. It proves the point that just adopting a technology and framework is not enough; a process must be set up to ensure the platform is always up-to-date.
A common misconception is that developer self-service refers to a certain life cycle stage of a service or resource, namely, its start. People think they should focus on making it easy to clone templates or spin up a database without having to deal with Terraform. This is a part of the self-service. But I would argue it is a small part. Ask yourself this: How often do you spin up a new service or database? Not very often in the grand scheme of things. The real return on investment of self-service lies in the remaining parts of the service, app, or resource life cycle. This includes making it simple for a new developer to understand what belongs where, enabling clear and separated progression between environments, updating env variables effectively, updating resource configurations easily, ensuring security without taking freedom away; and making it super easy to debug deployments and surface error messages as well as consolidate logs. All this gets better through self-service!
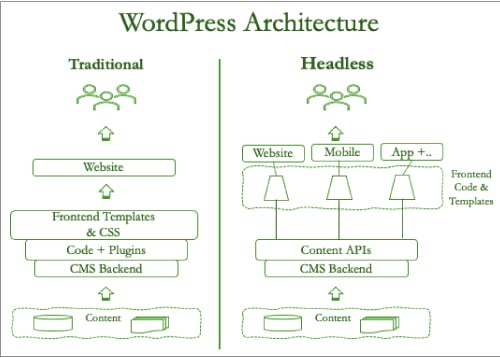
The security of any application is as good as its weakest access point. It’s important to know the architecture of the application, especially the deployment model, to ensure the infrastructure, network, and application access points are protected. WordPress architecture has two primary models — the traditional monolith, where the backend content is deeply integrated with the frontend of the website. Since WordPress is packaged this way, this is the most widely adopted model. However, many organisations, while embracing digital transformation with web, mobile, and other mediums of interfaces, deploy WordPress as a headless architecture. Here, the frontend, middle, and backend are all decoupled to provide greater flexibility of leveraging the same content across different CMSs. This architecture focuses on a seamless and effortless customer experience across multiple channels.
Simple best practices like a secure website (HTTPS), multi-factor authentication, frequent change of admin user name and password, along with proper screening and updation of the plugins in use will ensure hackers and users with malicious intent are kept at bay.
CMS software evolves rapidly. Typically, new versions are distributed more often than most other software. These updates include responses to security and vulnerability threats.
Adoption of dynamic configuration management (DCM) frameworks allows developers to separate environmental configurations from that of the platform and application. This allows for rapid deployment of new versions of software with minimal impact on the applications.
















































































