ZeroTier describes itself as a global Ethernet switch to connect any number of devices. The subscribers connect to this imaginary switch and then communicate as if they were in the same local network. Let’s look into how this actually works.
zeroTier’s Ethernet switch is figurative and symbolic; subscribers actually connect via a virtual private network (VPN) to a predefined VPN server operated by ZeroTier. The VPN server connects clients’ devices so that they can talk directly to each other. The result is an encrypted peer-to-peer network.
The transport network is responsible for securing participants’ communication and authentication. This network also achieves another important task by finding the best path between clients. Above this network layer, ZeroTier emulates the well-proven Ethernet to provide applications with a known protocol. For the participants, the VPN appears as an Ethernet switch. The technology behind this design is similar to IPsec and VXLAN.
The data packets between ZeroTier clients are encrypted and only understood by other clients, but not by the ZeroTier servers. The used algorithm originates from the toolbox of elliptic curves and offers a key length of 256 bits. The client software automatically handles the key exchange and certificate management.
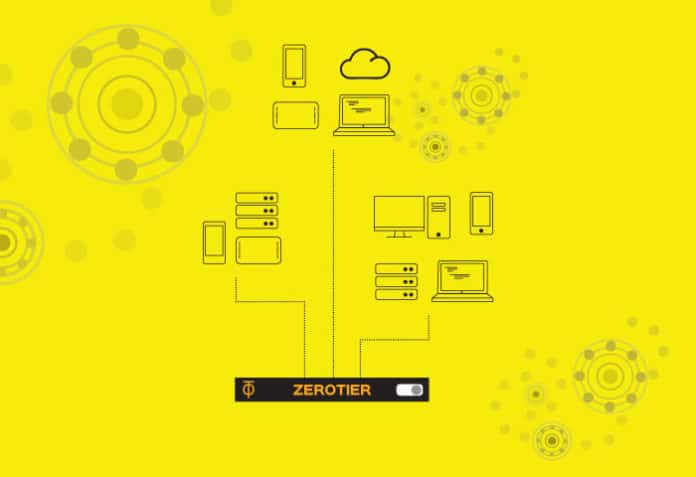
In Figure 1, the clients use the ZeroTier cloud as a fully meshed backbone network that independently finds the shortest connections between all sites.
Access
The computer uses the client software ‘ZeroTier One’ to access the ZeroTier network, which is offered as source code and as a precompiled binary for many operating systems and smartphones. On a laptop, the ZeroTier switch is another network adapter with IP address, routes, and firewall rules. It can be used to connect remote sites, dial in clients, or create out-of-band management access.
To begin, the Web service ‘ZeroTier Central’ expects a registered user. The registration process creates a new Ethernet switch. In return, ZeroTier provides a network identifier that the clients use to access the network. This network identifier distinguishes the clients from each other and prevents client A from reaching the devices in client B’s network. Keep in mind that ZeroTier is a free commercial service provider for up to 50 devices.You can use ZeroTier’s Web portal to register a new account. Afterwards, create a network for your devices by clicking on the button ‘Create A Network’ in the Web UI of ‘ZeroTier Central’. The network immediately appears in the right-hand area with a randomly generated ID and an exemplary name. In this example, the new network has chosen the ID 1d7193940486c4c6, which is required later for the ZeroTier One client setup. Click on the network ID to configure the properties. The preset values are suitable for the initial setup.
Installation
On the client-side, the device needs the software ‘ZeroTier One’, which is available for all major operating systems. The installer script for Linux recognises the distribution and uses the appropriate package from the repository:
curl -s https://install.zerotier.com | bash |
Use the command line to set up a connection between your computer and ZeroTier. The command requires the network ID from the previous section and then connects to the ZeroTier server.
zerotier-cli join 1d7193940486c4c6 |
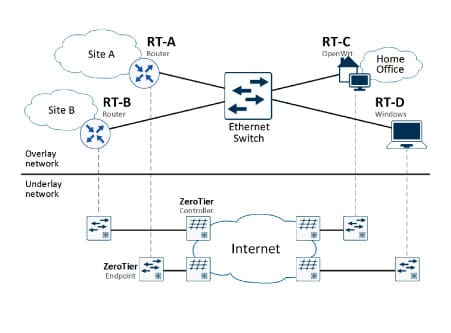
The Web view of ZeroTier and Figure 2 show the newly connected client. Since the default settings define the network as ‘private’, the client can only use the ZeroTier network once the admin has confirmed this in the ‘Auth’ column. It is also helpful to label the new device to easily distinguish it from future clients.
| Note: The ZeroTier client assigns the interface a cryptic name that begins with the letters ‘zt’. This name may differ from your own experiments in the following command outputs. |
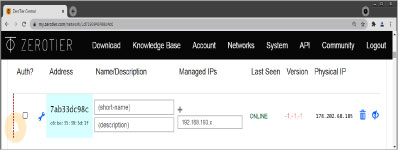
As soon as all devices are connected, the list in ZeroTier extends and becomes similar to Figure 3. For validation purposes, the clients can ping each other using their ZeroTier IPv4 address from the assigned range (here: 192.168.193.0/24). The setup under Windows, macOS, and on smartphones is similar, except for a graphical interface.
ZeroTier as a switch
ZeroTier compares itself to a global Ethernet switch, allowing clients to use the ZeroTier connection as a network bridge. The result truly feels like an Ethernet connection to the subscribers.
By default, clients do not operate as a network bridge. To enable bridge mode, go to the ZeroTier Web UI and enable ‘Allow Ethernet Bridging’ for each device individually (Figure 4).
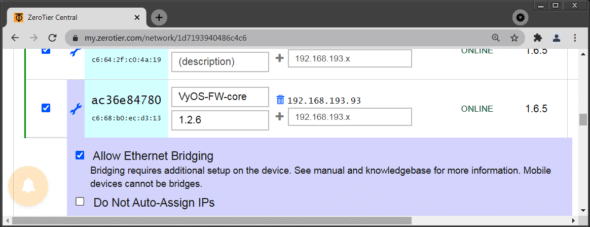
On the client-side, Linux requires a network bridge that joins the interfaces eth0 and zt7nnn53ro. The result is a genuine Ethernet connection; the connected devices share a broadcast domain and can use the same IP network. There is also no need to manage and distribute routes.
Firewall
Linux and Windows come with a robust packet filter that can block unwanted IP connections. The use of this local firewall is made possible because ZeroTier is treated as a regular interface and can belong to a firewall zone.
ZeroTier Central comes with ‘Flow Rules’, which is an effective way to control the data streams from a central point. The configuration is less convenient; the firewall rules are created as text, similar to iptables rules. The resulting security policy applies to all ZeroTier clients connected to this network ID. As soon as the rule set is ready, the clients fetch the new policy and apply it locally.
The use of the firewall is recommended if incoming traffic originates from an untrusted location or if the ZeroTier switch is classified as insecure. In this case, the ZeroTier interface will receive a firewall policy that uses restrictive rules to block anything that is not explicitly allowed. The firewall policy can filter at both the IP layer and the Ethernet layer.
Self-hosting ZeroTier
The makers of ZeroTier maintain several root servers for all subscribers so that the client software can get in touch with the network and reach other nodes. It is possible to run one (better: two) root server and a network controller to independently build a ZeroTier cloud without outside dependencies. The required software is already installed because the ‘ZeroTier One’ client also functions as a network controller or root server.
Network controller
The first step to independence is to have your own network controller. ZeroTier uses the network controller as a configuration manager and certification authority. The configuration of the controller uses ZeroTier’s API, which is well documented but inconvenient for daily use. Those who do not like to set up their new infrastructure with curl, wget, or httpie can use the Web interface from the third-party provider ‘Key Networks’. The installation of the ZeroTier software and the Web UI is described in Listing 1 for a server running Debian Linux.
Listing 1: This script turns a Debian Linux host into a ZeroTier controllerwget http://download.zerotier.com/debian/buster/pool/main/z/zerotier-one/zerotier-one_1.8.1_amd64.debdpkg --install zerotier-one_1.8.1_amd64.debsystemctl restart zerotier-onewget https://s3-us-west-1.amazonaws.com/key-networks/deb/ztncui/1/x86_64/ztncui_0.7.1_amd64.debdpkg --install ./ztncui_0.7.1_amd64.debecho ‘HTTPS_PORT=8443’ > /opt/key-networks/ztncui/.envsystemctl restart ztncui |
After the installation is complete, the Web interface is available at the URL https://ipaddress:8443/. The first login uses the credential admin/password. Subsequently, the Web UI forces a password change to boost security.
The configuration is very similar to the procedure from the previous section, although the Web UI of ‘Key Networks’ offers a smaller functionality than ZeroTier Central. The setup starts with the button ‘Add network’, which immediately creates a new network and presents the network ID. A client can directly join this network without knowing the network controller. The required command is no different from a regular ‘join’:
zerotier-cli join a0a9c4de8a520e4d |
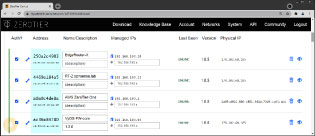
In the network controller’s Web interface, the new members need authorisation and an IP address. In Figure 5, the participants have registered with the controller and received their IP addresses. In the background, the ZeroTier clients communicate with the ZeroTier root servers to find the new controller. The next step to independence is to have your own root server.
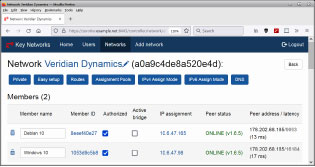
Root server
ZeroTier implements the functionality of the root server again in its ‘ZeroTier One’ application. The documentation refers to a self-hosted root server as a ‘moon’. The provider recommends using two moons that have a stable network connection and static IP addresses. The hardware requirement is minimal, so any virtual machine at a cloud provider can become a root server. Furthermore, the provider recommends that the root server does not simultaneously work as a network controller.
In Listing 2, a Debian server becomes the moon of the ZeroTier universe. Line 2 creates a world definition as well as crypto material. Line 4 lists the new root server’s IP address (here: 18.192.207.139) as the ‘stable endpoint’. If a second moon is added, it needs another entry under ‘roots’.
Listing 2: The Debian machine becomes a root servercd /var/lib/zerotier-one/zerotier-idtool initmoon identity.public >> moon.jsonsed -i -e ‘s!stableEndpoints”:.*!stableEndpoints”: [ “18.192.207.139/9993” ]!‘ moon.jsonzerotier-idtool genmoon moon.jsonmkdir -p moons.d/mv 000000a0a9c4de8a.moon moons.d/systemctl restart zerotier-one |
The resulting moon file is signed in line 6 and stored in the subdirectory moons.d. The file name is inspired by the world identifier, which is created in line 2. The clients will need this identifier later to find the moon. The root server is ready to use only after restarting ZeroTier One.
Finally, it is time to point the ZeroTier clients to the new universe. In the technical language of ZeroTier, the client ‘orbits’ the moon. Specify the world ID to guide the client to the new moon from Listing 2, whereby the leading zeros of the ID may be omitted:
root@client:~# zerotier-cli orbit a0a9c4de8a a0a9c4de8a200 orbit OK |
The command ‘zerotier-cli peers’ shows if the client and moon meet. Executed on the moon, the command output should include the IP addresses of the other clients and show the role LEAF. Executed on the client, the list of planets should contain the self-hosted moon in the role MOON (Listing 3).
Listing 3: The client has made contact with the new moonroot@CentOS8 ~> zerotier-cli peers200 peers<ztaddr> <ver> <role> <lat> <link> <lastTX> <lastRX> <path>1d71939404 1.8.0 LEAF -1 DIRECT 17771 17625 34.70.132.9/2857561d294b9cb - PLANET 181 DIRECT 2658 2476 50.7.73.34/999362f865ae71 - PLANET 245 DIRECT 2658 2415 50.7.252.138/9993778cde7190 - PLANET 137 DIRECT 7671 2510 103.195.103.66/9993992fcf1db7 - PLANET 30 DIRECT 12680 2617 195.181.173.159/9993a0a9c4de8a 1.8.1 MOON 30 DIRECT 2623 2623 18.192.207.139/9993 |
The ZeroTier clients and the new moon still have connections to other nodes in the ZeroTier universe. As soon as these are no longer accessible, the remaining infrastructure continues to operate autonomously and is thus independent of external services or an Internet connection.
Technical background
ZeroTier hides its complexity behind a fancy Web interface and the ‘ZeroTier One’ software. In the background, a distributed network hypervisor operates over an encrypted peer-to-peer network. ZeroTier divides its complexity into an overlay network, which emulates an Ethernet switch for its subscribers; and an underlay network, which uses the shortest path to deliver the packets to the end devices (Figure 1).
The transport network consists of several root servers, which link the ZeroTier clients to each other and provide hints for short end-to-end connections. If the clients cannot find a suitable connection to each other, the root servers forward the packets. The root servers are operated by ZeroTier and thus make up the backbone network.
Above the transport underlay network, the Ethernet virtualisation layer serves as the overlay network. It presents the ZeroTier network as an Ethernet adapter to the operating system and the applications. For this to be successful, the overlay network must handle the typical tasks and protocols of Ethernet — ARP, NDP, broadcast, and multicast.
The network controller is responsible for the configuration and also acts as a certification authority, issuing certificates for the endpoints. The ZeroTier One software can be used as a client, network controller, or root server.
Routing
ZeroTier can not only connect individual clients, but also entire networks. The ZeroTier software then runs on a router that announces its connected IP networks to the other ZeroTier routers. The outcome resembles a multipoint VPN that connects all locations and is managed from a central location. The advantage of this solution is that it eliminates the manual configuration that is typical for OpenVPN and IPsec.
The best operating system for the new ZeroTier router is a Linux/UNIX distribution that focuses on routing and firewalls, such as OpenWrt, VyOS, and OPNsense. The ZeroTier software is installed via a package manager and requires the well-known network ID from the previous sections. After authorisation in ZeroTier Central, the new routers are regular members of the ZeroTier group.
The routers now recognise each other, but they do not yet know all the attached local networks. There are several possibilities for exchanging routing information:
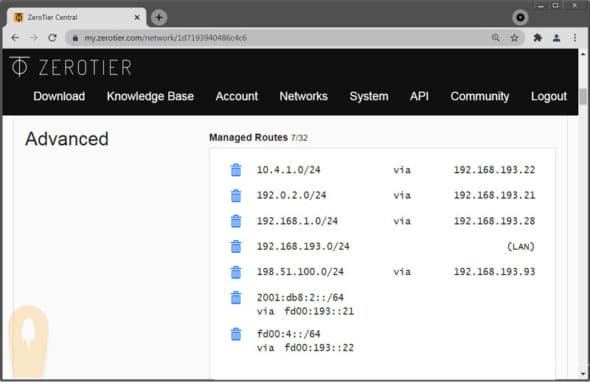
- The routers learn the path information to the other locations from the ZeroTier server. For this to work, enter the IP network in the field ‘Managed Routes’ of ZeroTier’s Web interface (Figure 6). The ZeroTier clients will learn from this central routing table upon connection. This method is suitable for all environments as long as all routers have a connection to ZeroTier. In the free version of ZeroTier, the maximum number of routes is 32.
- Alternatively, the routers use a dynamic routing protocol, such as OSPF. The routers establish neighbourships through the ZeroTier network and use them to exchange IP information. This method is suitable for large environments or if some routers do not have a connection to ZeroTier.
Outlook
The design of ZeroTier’s VPN is similar to a software-defined wide-area network (SD-WAN). In fact, ZeroTier with its central routing table, flow rules, and multipath has many similarities to SD-WAN. However, ZeroTier’s VPN is missing a zero-touch deployment of routers and granular control over which traffic streams should flow over which VPN connection.
Name resolution of ZeroTier devices was a weak point for a long time, so users mostly had to work with static IP addresses. As a workaround, there are community projects, like ZeroDNS, and finally, ZeroTier provided the official DNS service ‘ZeroNSD’ — but only in the beta stage.
Those who find the ‘Key Networks’ Web interface lacking functionality, can switch to the full-blown software ZeroUI. The software has a large number of dependencies and only runs in a Docker container. After a rather complex installation, a full-fledged Web UI is available that implements virtually all of ZeroTier’s functions.
Summary
ZeroTier is a VPN solution that is easy to configure and is usable on all major operating systems and smartphones. The ‘ZeroTier One’ client automatically negotiates the tunnels, algorithms, and keys. To access the global network, the client only needs a network ID, which the administrator generates after registering in ZeroTier’s Web portal. As soon as all the clients are registered, they can reach each other and find the shortest paths between them.
The initial contact of the ZeroTier client is always against the provider’s root servers. An Internet connection is mandatory, even if the devices are located in the same network segment. This dependency is compensated by simple configuration, great flexibility, and high security.