SaltStack or Salt is software to automate the management and configuration of any infrastructure or application at scale. All networking is planned around remote execution. This could be as basic as asking a remote Web server to show a static Web page, or as perplexing as utilising a shell session to intuitively give commands to a remote server. Salt architecture is used to execute commands remotely.
Salt allows users to unequivocally target and issue commands to several machines directly. It deploys a master which controls at least one minion. Commands are usually given from the master to a target bunch of minions, which execute the jobs sent by the master and afterwards send information back to the latter.
SaltStack is an open source, configuration management software and remote execution engine. It is a command line tool, written in Python. SaltStack configuration management is simple. Salt uses the push model for executing commands through the SSH protocol. The configuration comprises YAML and Jinja templates. Salt is on par with Puppet, Chef and Ansible. Being a feature-rich system, it provides many benefits such as robust authentication, as well as secure, fast, virtual machine automation, and infrastructure as data, not code.
SaltStack architecture
Figure 1 shows the key components of the Salt architecture.
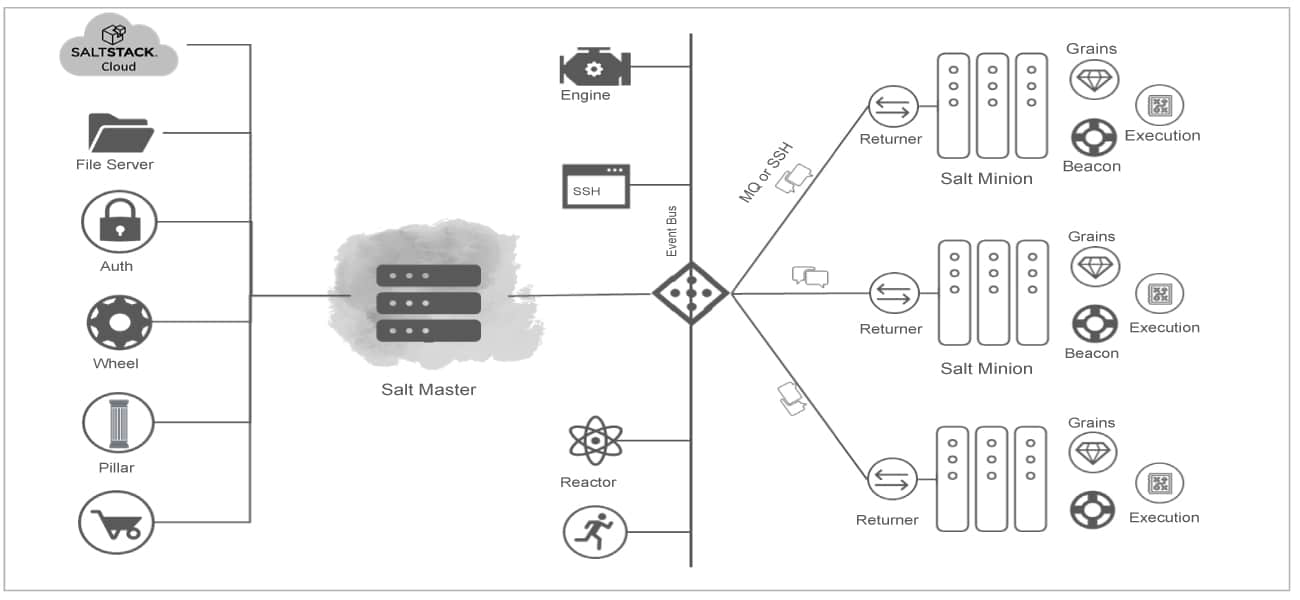
This architecture is intended to work with multiple servers — from local networks to other deployments across different data centres. It comprises a basic server/client model with the required functionality incorporated into a binary arrangement of daemons.
Some core components of SaltStack master are:
- SaltMine: SaltMine gathers the state information of the Salt minions and stores it in the master, and then makes the data accessible back to the minions. Mine data basically contains the network, firewall, and more.
- SaltPillar: This is used to put down delicate information like SSH key, credential files and passwords.
- Auth service: This service is used to authenticate the minions’ communication.
- File server: This is the ZeroMQ server. We can have ZeroMQ exchange the files from Salt master to minions. File worker requires a backend.
- Salt wheel (API): Salt wheel permits developers to programmatically get to the Salt master.
- Salt cloud: Salt cloud is a powerful interface for cloud hosts. Thus, it will give you the communication between Salt master and cloud machines.
- Salt cloud: Salt cloud is a powerful interface for cloud hosts. Thus, it will give you the communication between Salt master and cloud machines.
- Salt reactor: Salt reactor is an interface that keeps track of the Salt event bus for the particular event tag.
- Salt engine: This is the external system that uses the capacity of Salt expert’s long-running process. It controls Salt configurations, execution modules and runners. Engines are constantly associated with the event bus.
- Salt SSH: Salt SSH is an in-built service that permits the Salt master access to the Salt minions.
Components of SaltStack minions
Salt minions have the following chief components that make the configuration management system complete.
- Grain: Salt grain is an interface, which resembles a Salt mine. However, it will have static data of minions like operating system, domain name, IP address bit, OS type, memory, disk space, and numerous other system properties. In contrast to the Salt mine, you can build your own custom Salt grain to have the particular data about the Salt minion.
- Returner: Return data is the chunk of information that is returned after the execution of the command sent from the Salt master to Salt minions. Returner is an interface that permits the return information to be shipped off to any framework like the logical framework or monitoring system.
- Salt beacon: Salt beacon is the surveillance system of the Salt minions. These beacons are completely developed monitor and alert frameworks that will catch the issue or event, and permit Salt reactor to trigger accordingly.
- Salt execution module: When the Salt master gives the commands, execution modules from the Salt minions guarantee the execution and constant monitoring of these commands.
Installing SaltStack
Prior to installation, you need to have the following prerequisites:
Linux server
- Root access to the server
- The SaltStack repository
- Install all the updates by using the command given below:
sudo apt-get update |
Install SaltMaster from the repository using the apt-get command:
sudo apt-get install salt-master |
Install the Salt minion from the repository by using the following apt-get command:
sudo apt-get install salt-minion |
Install the salt syndic from the repository with the following command:
sudo apt-get install salt-syndic |
Master configuration
Salt configuration is not at all complicated. The configuration files are already installed in the /etc/salt directory and are named after their respective parts — for instance, /etc/salt/master and /etc/salt/minion:
#interface: 0.0.0.0interface: <local ip address> |
After updating the configuration file, restart the Salt master by using the command:
sudo service salt-master restart |
Minion configuration
The configuration of a Salt minion is very easy. A Salt minion attempts to connect to the DNS named salt; if the minion is able to sort out that name, no configuration is needed. Redefine the master directive in the minion config file, which is /etc/salt/minion, as shown below:
#master: saltmaster: <local ip address> |
After updating the configuration file, restart the Salt minion by using the command:
sudo service salt-minion restart |
Key management
Salt uses AES encryption for all the interactions between the master and the minion. The communication between the master and minion is authenticated and keys are accepted.
salt-key -L |
The output for the above command is given below:
Accepted Keys:Denied Keys:Unaccepted Keys:<local system name>Rejected Keys: |
Then accept all the keys by using the command:
sudo salt-key -A |
The output is:
Accepted Keys:<local system name>Denied Keys:Unaccepted Keys:Rejected Keys: |
Sending commands
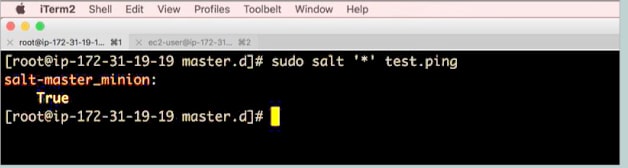
The interaction between master and minion must be confirmed by running the command:
sudo salt ‘*’ test.ping |
The result of the previous command is given in Figure 2.
Creating a simple SaltStack environment with one Salt master and two minions: To create the SaltStack environment, first install the VirtualBox environment. Download and install VirtualBox from https://www.virtualbox.org/wiki/Downloads. Now, create three virtual machines and run them using VirtualBox.
Next, install Vagrant. Vagrant provides simple to configure and portable work environments. You can download and install it from https://www.vagrantup.com. After the installation of Vagrant, we need to configure it. First, create a single file named Vagrantfile in a folder. Run Vagrant by using the following command:
vagrant up |
Now, Vagrant creates and starts the machines that are defined in the vagrantfile using VirtualBox in the background. To stop all the running machines, use the command:
vagrant halt |
Using Salt-Cli: Now, let us download the set up using the command:
cd /cd/to/pathgit clone https://github.com/UtahDave/salt-vagrant-demo |
Start the demo by using the command:
cd /cd/to/path/salt-vagrant-demovagrant up |
The response of the above command is:
resultRun the SALT MASTER |
By using the command given below, log in to the Salt master:
vagrant ssh master |
Move to the root using the command:
sudo su |
We have successfully connected to the Salt master. Now, we will experiment with some basic commands in SaltStack.
List out all the keys: The following command is used to verify the Salt minion connections and view the connection status:
salt-key —list-all |
The outcome of the previous command is:
Accepted Keys:Minion1Minion2Denied Keys:Unaccepted Keys:Rejected Keys:Verify Salt Minions |
Post receiving all the keys, you can send a command from Salt master to check if the Salt minions are listening or not:
salt ‘*’ test.ping |
It will give the following output:
Minion1:TrueMinion2:True |
From the above output, list out minion 1 and minion 2, which means minions are listening properly; otherwise, minions may not respond properly.
You now know what SaltStack is and how to install it. SaltStack makes it simple to set up servers in data centres with minimal installation time. It is an incredible resource because of its ease of use. This article should be able to help you set up SaltStack and easily create or maintain your server for any use case.












































































