Traditional storage systems are centralised and prone to hacking. Use of blockchain based decentralised storage platforms can increase the overall security, integrity and privacy of data files substantially.
Many of the world’s leading corporations have experienced data leaks as a result of cyber-attacks. Ransomware, malware, phishing, Denial of Service (DoS), vampire attacks and so many other kinds of attacks are used by cyber criminals to fetch private information.
Numerous companies are developing security solutions against different types of data leakage and breaches but a lot still needs to be done. Cyber cells and forensic professionals are working on the development of new protocols and algorithms to enforce security and higher levels of encryption in confidential data.
As most companies now prefer to keep their personal data and files on the cloud, there is need to explore secured cloud platforms to thwart any attempts at hacking. With the use of secured networks or cloud storage, the overall integrity and privacy of files is elevated.
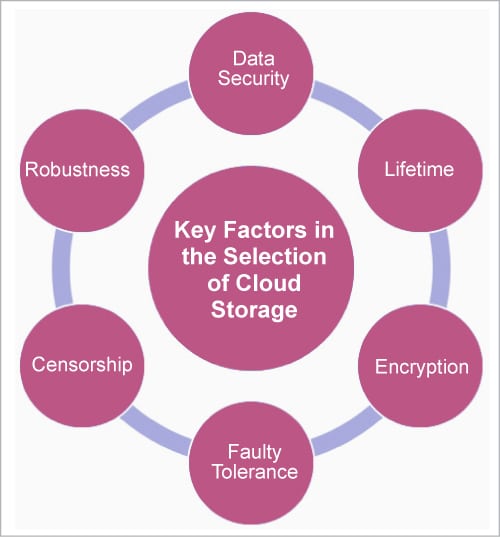
While selecting the storage platform for uploading personal, social or official records, numerous factors are considered so that these can be kept fully secure and private. The important factors include:
- Cost and paid subscriptions
- Censorship and data leakage issues
- Data mismanagement, distribution or selling to unauthorised organisations
- Security and privacy with encryption
- Longer lifetime
- Fault-tolerant
- Robustness in case of node failures
There is a need to integrate secure systems for storage with a better degree of privacy so that any sniffing or cracking may be prevented.
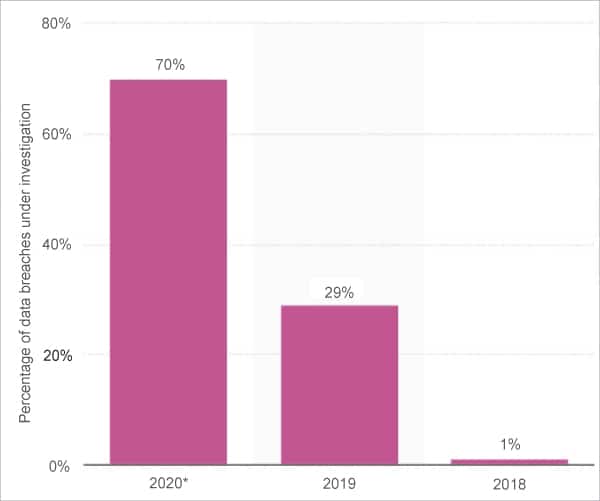
Figure 2 depicts the percentage of data breaches in the health sector in the US that are still under investigation.
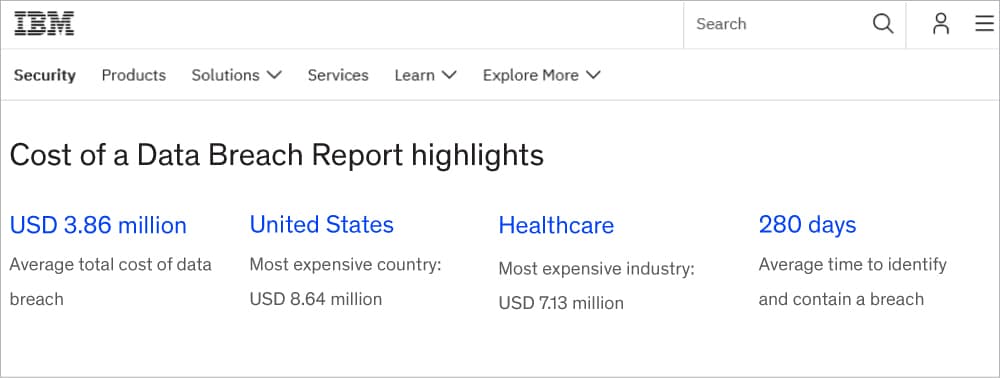
Figure 3 shows the huge cost to organisations that have data breaches, as these also affect the integrity of the enterprise.
| Cloud platform | URL |
| IceDrive | https://icedrive.net/ |
| pCloud | https://www.pcloud.com/ |
| Sync | https://www.sync.com/ |
| Mega | https://mega.io/ |
| DropBox | https://www.dropbox.com/ |
| IDrive | https://www.idrive.com/ |
| Yandex | https://disk.yandex.com/ |
| JumpShare | https://jumpshare.com/ |
Table 1: Centralised platforms
Assorted platforms for secured backup and recovery
A variety of network based systems, including cloud repositories, are available for uploading files and information, such as Google Drive, DropBox, Microsoft OneDrive, Jio Cloud, and many more. Storage repositories are divided into two categories — controlled cloud storage and decentralised cloud platforms. Anonymity is preserved in the case of decentralised storage platforms through encryption and dynamic fragmentation of data files. The InterPlanetary File System (IPFS) is one of the decentralised platforms that maintains the security, privacy and integrity of data. Such platforms integrate blockchain technologies to ensure dynamic security for the data files.
Currently, blockchain based cloud storage is used for multiple domains including education, infrastructure, mobile networks, community networks, Web hosting, supply chain management, music, medical data, electronic health records (EHR), and video streaming.
Decentralised platforms are very often associated with blockchain based environments in which complete security and privacy is given to data.
| Cloud platform | URL |
| Sia | https://sia.tech/ |
| Storj | https://www.storj.io/ |
| IPFS | https://ipfs.io/ |
| Swarm | https://www.ethswarm.org/ |
| GUN | https://gun.eco/ |
| OrbitDB | https://github.com/orbitdb/orbit-db |
| FileCoin | https://filecoin.io/ |
| BlockChainDB | https://www.bigchaindb.com/ |
Table 2: Decentralised platforms
These decentralised platforms can be programmed using various programming toolkits and frameworks including Python, JavaScript, HTTP APIs, PHP and Java. With the integration of a blockchain based environment in the storage repositories and database applications, multi-dimensional security and privacy of data can be achieved. Many open source communities and corporate giants are working towards this.
To sum up, data leakage and identity theft is on the rise due to the billions of connected devices in use today. Traditional database engines, file repositories and storage systems are not secure because of the centralised environment, which makes it easy for hackers to penetrate into the central server and fetch files. With the use of blockchain based decentralised storage platforms, the overall security, integrity and privacy of data files and credentials can be increased effectively.




