The increasing use of Internet enabled devices has led to a higher incidence of cyber threats, through various forms of malware. Python is used a lot in cyber security and digital forensics. To cite a common use case, today, videos and images go viral very easily and can be security threats. Python tools can not only identify the location of the image, the camera which first took the video but also the exact smartphone used. Criminals beware! Python is watching you.
Nowadays, most people depend on smartphones and technology based devices for routine work, whether official communication or social media. The prolific use of smart devices and Internet connected gadgets invites cyber attacks and the entire world is affected by it. In India too, cyber attacks are very common.
The Annual Threat Report 2019 by Quick Heal states that the metro cities of India – Delhi, Bengaluru, Mumbai and Kolkata – are the most affected by cyber attacks. The reports underlines that there were more than 950 million attack instances registered last year. Another report from inc42.com states that India is the second most affected country, in terms of cyber attacks of different types. The report calculates average cost per cyber attack to be around Rs 4,552. These figures are scary and, hence, awareness about cyber security and digital forensics should be increased.
The Internet of Things (IoT) is also affected by cyber attacks. Millions of smart devices are connected with each other. These include smart watches, webcams, e-health gadgets and many others. The Economic Times reports that there has been 22 per cent growth in cyber attacks on IoT deployments in India. The research analytics shows that there were more than 2500 unique malware impressions that affected the IoT environment and deployments.
 An urgent need for awareness about vulnerabilities and security
An urgent need for awareness about vulnerabilities and security
These figures and research reports are frightening and must be addressed by law enforcement and forensic investigation agencies. The cyber investigation teams and government officials are required to be equipped with advanced tools and knowledge about programming languages so that any malicious attack can be identified and the root cause traced.
There are a number of software libraries, frameworks, tools and programming languages available for cyber security and digital forensics, which every citizen should be aware of. Awareness is the first line of defence against cyber attacks.
Python tools for cyber security and digital forensics
There are a number of programming languages and tools available for cyber security and digital forensic applications, but Python is the most widely used. Python has hundreds of thousands of modules on its official repository PyPi.org. These cover assorted domains including cyber security, grid computing, information security, cloud applications, Web scraping, image forensics and many others. Python is one of the most used programming languages by cyber security professionals since it has numerous free and open source tools and packages.
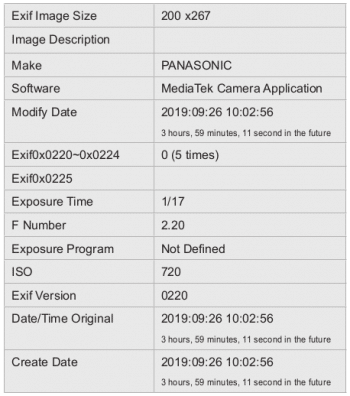
Image EXIF and Python programming
Every digital image has exchange information (EXIF) data that can be used to identify the actual camera or device that captured the image. Python provides many libraries and packages for EXIF metadata to recognise the root of a viral image.
Python integrates the package Python Image Library (PIL) for image analytics and forensic applications. It is also used for the extraction of EXIF metadata to recognise the camera information as well as the location at which the image was taken. The PIL package is available in the new version as Pillow. It can be installed using the PIP installer as follows:
$ pip install Pillow |
In addition to image forensics, the following features are available in PIL:
- Pixel based manipulations and forensics
- Image masking
- Image transparency
- Image filtering
- Edge detection
- Image smoothing
- Blurring
- Enhancements
- Steganography
The Python library PIL provides a few lines using which deep information about the image can be extracted in real-time. The following is an example of fetching the image’s location using exchange information (EXIF).
import PILimg=PIL.Image.open('viralimage.jpg')exifdata=img._getexif()print (exifdata) |
Nowadays, the location and camera information associated with viral images can be extracted using EXIF data. If a specific image or video is going viral, the first person who took that image from the camera can be identified using EXIF.
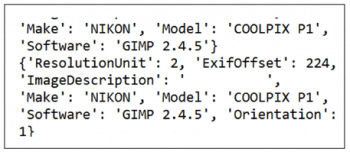
As shown in Figure 1, the camera information of the image is recognised using the EXIF code of Python.
After formatting and advanced manipulations in the EXIF, the information about the actual smartphone that captured a particular photograph can be fetched (Figure 2).
The deep analytics using EXIF shows the exact name and model of the smartphone that was used to take the image. By this methodology, the forensics associated with the image is very easy when using Python programming.
Web server fingerprinting
Web server fingerprinting refers to the identification of internal information about a remote server or IP address used for the specific assault. If a specific attack is mounted using a particular system, it can be identified. On attempting any cyber attack, the source system can be deeply investigated using socket programming in Python. Socket programming is used to connect to the remote system in order to analyse the root attacker system.
>>> import socket>>> socket.gethostbyname(‘URL')>>> socket.gethostbyaddr(‘IP Address') |
Using these inbuilt functions of Python, the URL or IP address can be tracked. In addition, there are assorted libraries in Python that are used to extract deep information about the devices or remote systems.
Security aspects of webcams and CCTVs
Nowadays, there are umpteen smart gadgets and webcams which are connected on IoT environments with IP addresses. These IP based webcams are indexed by specialised search engines. Shodan (shodan.io) is one of the famous search engines that indexes and saves the information of IP based webcams. By simply installing the webcams, the security and integrity cannot be ensured unless the security of the IP addresses is ensured. Shodan is able to fetch information about webcams and IoT devices that are vulnerable.
On creating an account on Shodan, an API key is generated from the URL https://account.shodan.io, and it can be used for fingerprinting and deep information about IoT based devices.
The official portal of Shodan provides the API key that can be integrated with Python code and the fingerprinting of a webcam or IoT device can be done; however, this is quite unsafe if the IoT device is not secured with a strong password.
import shodanSHODAN_API_KEY = "**************************"shodanapi = shodan.Shodan(SHODAN_API_KEY)thishost = shodanapi.host('Target IP Address')print("""Extracted IP: {}Extracted Organization: {}Extracted Operating System: {}""".format(thishost['ip_str'], host.get('org', 'n/a'), thishost.get('os', 'n/a')))for item in thishost['mydata']:print("""Extracted Port: {}Extracted Banner: {}""".format(item['port'], item[my'data'])) |
If the script is executed, port scanning and deep information of the IP webcam can be extracted using a Python Script which is available as free and open source. Therefore, the immense vulnerability of webcams and IoT gadgets must be secured.
Key tools for cyber security and digital forensics
- Steganography and hidden information extraction
- E-mail fingerprinting
- Image and video forensics
- Remote access denial
- Web scraping
- Internet of Things (IoT) security
- Web applications security
- Vulnerability analytics
- Anti-exploitation tools
- Anti-sniffing and anti-spoofing attacks
To ensure the security and privacy of the webcams and IoT gadgets, strong passwords should be used, otherwise anybody can access them.
With the adoption and integration of advanced devices on the Web environment, there is need to ensure the security and integrity to Internet connected infrastructure. Apart from Python programming, blockchain technology, quantum cryptography and multi-factor authentication are the other secured approaches that are very important for real world applications.