The last article in the series had explored Gigya and Janrain, covering aspects like their flexible architecture that enables integrating an enterprise digital solution for CIAM requirements. In this article, we will cover ForgeRock, IBM Federated Identity Management, PingIdentity and Stormpath.
The ForgeRock solution provides interactive profile and privacy widgets as user-specific dashboards for continuous monitoring and task handling purposes. This is in compliance with EU’s Data Privacy Policy and GDPR. ForgeRock is one of the preferred partners for banking IT solutions due to its support for frictionless user experiences (UX) and real-time identity context, which optimises the Omnichannel experience throughout the user journey.
ForgeRock provides distributed policy management, which can be customised with the flexible data source schema and API design. Hence, handling policy management across different user instances of connected application sources, including social networking identities, is quite flexible with ForgeRock based implementation.
The main factors that influence people to choose ForgeRock as a CIAM (Customer Identity and Access Management Solution), solution are listed below:
- Customisable, with the flexibility to adopt at runtime
- User notifications
- Offline and online approval/rejection
- Customisation of API and data source/schema available
- Since ForgeRock is open source, any kind of customisation is possible, including API redesign
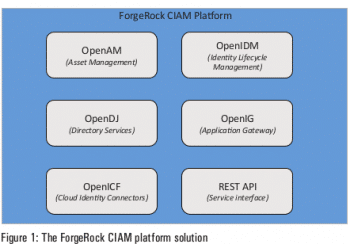
The five major components of the ForgeRock integrated architecture are listed below.
- OpenAM: An access management solution
- OpenIDM: An identity life cycle management system
- OpenDJ: This is for directory services
- OpenIG: This is an application gateway
- OpenICF: This offers cloud identity connectors
Apart from these, ForgeRock provides custom REST API interfaces to integrate with any enterprise solution to invoke any of the above connectors/handlers.
 IBM Federated Identity Management (FIM)
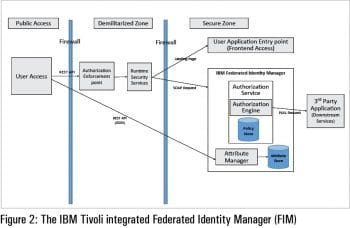
IBM Federated Identity Management (FIM)
IBM’s Cloud Identity Service and Security Access Manager has been ranked as the leader among CIAM solutions at the Leadership Compass 2017. It is a multi-tenant, fully cloud based identity service with integrated services for security, functionality, integration, interoperability and usability. It is designed to excel in business-to-consumer (B2C) use cases because it is a highly available cloud offering with a robust suite of self-service applications, and can rapidly scale in scenarios with millions of external users.
Some of the factors influencing the choice of IBM FIM as a CIAM solution are:
- Principle and rights management
- Identity access management
- Workflow of user operations
- Context based access control
- Policy based authentication
- On-premise application to access cloud based routing to IBM CIAM through REST API call
IBM Security Access Manager provides a data model for user/group based role handling with hierarchy management of policies and user access permissions. It also provides a CIAM solution for context based access control for individual user and group policies, as well as policy based authentication for user accessibility roles.
One of the disadvantages of this solution is that reporting is not available (audits) as an in-built solution. Hence the user has to rely on integrating with other audit and reporting solutions like util logger, log4j, etc.
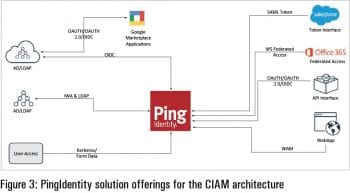
PingIdentity
If you are looking to prepare a CIAM solution with an integrated cloud offering and SaaS support for a cloud based component offering, PingIdentity would be most suitable. It provides a purpose-built customer IAM (CIAM) solution without compromising on security and flexibility to support mobile integration and cloud adoption. It is integrated with a secure, seamless CIAM solution for single sign-on, data governance, multi-factor authentication and intelligent API security.
Some factors that would influence an enterprise architect to choose PingIdentity for a CIAM solution are:
- Internal support for cloud based operation
- Data model flexibility for re-architecting/re-designing
- Suitability for cloud adoption/migration
- Mobile based offering
- Enterprise solution for cloud based SaaS provider
- Cloud based deployment model (for components)
- SaaS and hybrid cloud offering
At the same time, one has to note that with PingIdentity based solutions, a dynamic schema for File of Record is not possible.
 StormPath
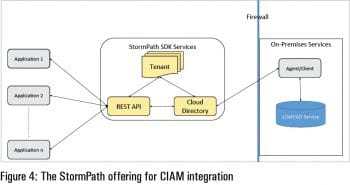
StormPath
When you are preparing a CIAM solution for a better customer experience in terms of ease of use and an integrated solution for social networking accounts, then StormPath is the ideal choice. The StormPath CIAM solution provides a digital customer experience combined with an inbuilt data store (without compromising integration with external data providers or cloud service providers) and policy driven group membership. Application integration provides solutions for ID integration with social network user accounts, and provides a consistent experience across channels for customers. This ensures a better user experience (UX) by connecting marketing, business and security teams to protect and handle customer data with ease.
Factors influencing users to choose StormPath as an integrated CIAM solution are:
- Usability of the application and flexibility of user policies
- Data model customisation and security of data handling
- Suitability for cloud adoption/migration
- Custom policy design
- Digital customer experience and flexible design of data store
- Integrated data store and policy based solution
- Group membership and policy driven
- In-built data store
Though there are many advantages of using StormPath in CIAM integration, it does come with heavyweight architecture and complex navigation in workflows.
So, a careful evaluation of the target architecture is really needed before deciding on a particular CIAM solution.
















































































