Computer vulnerabilities can be very vexing and unnerving, especially when computer systems are used for production. Sysadmins can fall back on Open VAS or Open Vulnerability Assessment System to locate and understand these vulnerabilities. Open VAS is free and open source, and is a one stop solution for vulnerability assessment.
OpenVAS is a vulnerability scanner. It is a framework of several services and tools offering a comprehensive and powerful vulnerability scanning/management solution. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet and industrial protocols, performance tuning for large scale scans, and a powerful internal programming language to implement any type of vulnerability test. It is open source and free. The scanner is developed by Greenbone Networks and has been maintained by it since 2009. The work has been open sourced to the community under the GNU General Public License (GNU GPL).
OpenVAS comprises a number of services and clients. By understanding the role of the different mechanisms you will be able to effectively administer OpenVAS servers.
What is an NVT?
NVT refers to network vulnerability tests. These are conducted using plugins that are developed in NASL code. The scripting language is a legacy of its original Nessus code base. NASL or Nessus Attack Scripting Language is used for the testing of vulnerabilities first developed in 1998. With inspiration from the C programming language, non-coders wishing to quickly develop a vulnerability test may be better served by Nmap and its LUA based NSE (Nmap Scripting Engine) scripts.
Installing OpenVAS on Kali
The most famous of the Linux penetration testing distributions, Kali Linux is a popular choice for swiftly getting tools up and running as many are pre-installed and pre-configured. Installing OpenVAS is very clear-cut. Simply run apt install and then run the configure script, as shown below:
root@kali:~# apt-get update root@kali:~# apt-get dist-upgrade root@kali:~# apt-get install openvas root@kali:~# openvas-setup /var/lib/openvas/private/CA created /var/lib/openvas/CA created
[i] This script synchronises an NVT collection with the ‘OpenVAS NVT Feed’.
[i] Online information about this feed is at http://www.openvas.org/openvas-nvt-feed.
... sent 1052 bytes received 64342138 bytes 99231.26 bytes/sec total size is 64342138 speedup is 1.00 [i] Initializing scap database [i] Updating CPEs [i] Updating /var/lib/openvas/scap-data/nvdcve-2.0-2002.xml [i] Updating /var/lib/openvas/scap-data/nvdcve-2.0-2003.xml ... Write out database with 1 new entries Data Base Updated Restarting Greenbone Security Assistant: gsad. User created with password ‘* password that looks like uuid *’.
Allowing OpenVAS through the system firewall
By default, OpenVAS runs on Port 443, so you will need to allow this port through the UFW firewall, by using the following command:
sudo ufw allow https
Accessing the OpenVAS Web interface
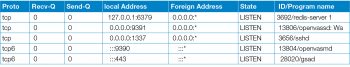
The OpenVAS Web interface (gsad) runs on TCP Port 9392. However, depending on your installation, it could also be listening on TCP 443. After installation, this can be confirmed by checking the listening ports on your system using the following commands (see Table 1):
root@localhost:/# netstat -alnp | grep LISTEN
From the ports shown in Table 1, we can see in our installation that gsad is running on Port 443. The OpenVAS Scanner (openvassd) is running on TCP Port 9391 and the OpenVAS Manager (openvasmd) is running on TCP Port 9390. Last is the redis-server on TCP 6379. This database is used to store temporary metadata during active scanning.
Opening https://server-ip/ in a browser shows the login screen for the Greenbone security assistant.
Key file locations of an OpenVAS install
It is important to know the locations of your OpenVAS log files and configurations. This will allow for quicker troubleshooting and management of your server.
The prefix of the path will usually depend on how OpenVAS was installed. A default source installation will put all the files under /usr/local/ while most packages will put the files in the expected locations: /etc/openvas/, /var/lib/openvas and /var/log/openvas/.
OpenVAS log files
The most common location will be /usr/local/var/log/openvas/ or /var/log/openvas/. In here, you will find the key log files, where you should look if things are not behaving as expected.
root@localhost:~# ls /usr/local/var/log/openvas/ gsad.log openvasmd.log openvassd.dump openvassd.messages













































































Onion is Better.