A blockchain has several built-in security features that make it attractive for purposes like land records, cryptocurrency transactions, etc. The security of personal data is a human right. A blockchain could be one of the methods of ensuring this.
Simply defined, a blockchain is, “A decentralised database containing sequential, cryptographically linked blocks of digitally signed asset transactions, governed by a consensus model.” Blockchain technology is a peer-to-peer networked database governed by a set of rules. A blockchain represents a shift away from traditional trust agents and a move towards transparency. As a technological building block, it permits applications from a broad band of industries to take advantage of sharing, tracking, and auditing digital assets.
Blockchain is a disruptive technology because of its ability to digitise, decentralise, secure and incentivise the validation of transactions. A wide swathe of industries is evaluating blockchain to determine what strategic differentiators could exist for their businesses if they leverage it.
This technology has the potential to improve security, processes and systems in the financial services domain, in government and every sphere where accurate, tamperproof record-keeping is essential.
The disrupted industries will include financial services, healthcare, aviation, global logistics and shipping, transportation, music, manufacturing, security, media, identity, automotive, land use and government.
Industry adoption of blockchain platforms
Market research predicts that, by 2024, the global blockchain market is expected to be worth over US$ 20 billion. The use and adoption of blockchain technology is expanding at a rapid pace, all over the world.
The Republic of Georgia has declared that it will use blockchain technology to validate property-related government transactions. Countries like Sweden, Honduras and others are also developing such similar blockchain based systems, for enabling secured e-governance.
Gartner projects that the business value added by blockchain will grow to US$ 176 billion by 2025.
Recently, the Dubai government announced that it will put 100 per cent of its records pertaining to land registry on blockchain. Dubai Land Department (DLD), in fact, claims to be the first such government department anywhere in the world to adopt the blockchain for such high-level tasks.
The European Union’s commercial research group, the European Innovation Council (EIC), has launched a programme to grant US$ 3.04 billion (2.7 billion Euros) to 1000 projects that are developing systems and solutions using blockchain technology.
Key characteristics of blockchain technology
Every transaction that records and stores is not labelled as a blockchain. The following are the main characteristics of blockchain.
- Digital: All the information on blockchain is digitised, thus eliminating the need for manual documentation.
- Distributed: Blockchain distributes control among all peers in the transaction chain, creating a shared infrastructure within an enterprise system. Participants independently validate information without a centralised authority. There is no single point of failure because of how a distributed system operates. Even if one node fails, the remaining nodes continue to operate, ensuring no disruption.
- Immutable: All the transactions are immutable in a blockchain technology based system. Encryption is done for every transaction covering the time, date, the participants and the hash to the previous block.
- Chronology: Each block acts like a repository that stores information pertaining to a transaction and links to the previous block in the same transaction. These connected blocks form a chronological chain providing a trail of the underlying transaction.
- Consensus based: A transaction on blockchain is executed only if all the parties on the network unanimously approve it. Also, consensus based rules can be altered to suit various circumstances.
- Digital signature: Blockchain enables the exchange of transactional value using unique digital signatures that rely on public keys (decryption code known to everyone on the network). Private keys are codes known only to the owner to create proof of ownership. This is very critical in avoiding fraud in record management.
- Consistent: Blockchain data is complete, consistent, timely, accurate, and widely available.
- Persistence: Blockchain will not create/persist invalid transactions as determined by consensus. It is nearly impossible to delete or roll back transactions once they are included in the blockchain. Cryptographically, the blocks created are sealed in the chain. It is impossible to delete, edit or copy already created blocks and put them on the network. This leads to the creation of digital assets and ensures a high level of robustness and trust.
- Anonymity: Each user can interact with the blockchain with a generated address, which does not reveal the real identity of the user.
Security features of blockchain
Blockchain helps in recording transactions of any digital assets exchanged between two unknown parties. Security aspects supported by blockchain are critical in ensuring transparency, confidentiality and protection against fraud. The following are the high-level security features of the blockchain.
Ledger: The ledger records every transaction in the blockchain. The ledger is a chain of blocks and information in the block is immutable. The distribution of the ledger is done to all the nodes.
 Chain of blocks: Blockchain is a chain of blocks. Each block has the hash value of the previous block and this forms a chain. Correction to data in a block (say, n) will change the hash value and will not validate with the hash stored in the next block (n+1). This will be a chain reaction and affect the overall chain. Therefore, this characteristic increases the protection of sensitive data or information.
Chain of blocks: Blockchain is a chain of blocks. Each block has the hash value of the previous block and this forms a chain. Correction to data in a block (say, n) will change the hash value and will not validate with the hash stored in the next block (n+1). This will be a chain reaction and affect the overall chain. Therefore, this characteristic increases the protection of sensitive data or information.
Confidentiality: Blockchain provides confidentiality by enabling users of a ledger to see authorised transactions only.
Transparency: Blockchain allows the transactions and the ledger state to be maintained and be managed transparently by sharing the ledger to all nodes and using consensus algorithms to reach consensus among all nodes. Consensus algorithms also ensure the ordering and execution of the transactions.
Cryptology: This enables secure transactions and makes blockchain immutable using hash based algorithms, which produce a fixed hash, based on the content of the block.
Smart contracts: A smart contract is a computer code running on top of a blockchain containing a set of rules, on the basis of which the parties agree to interact with each other. If the pre-defined rules are fulfilled, then the agreement is automatically executed. No contract will execute without the network consensus.
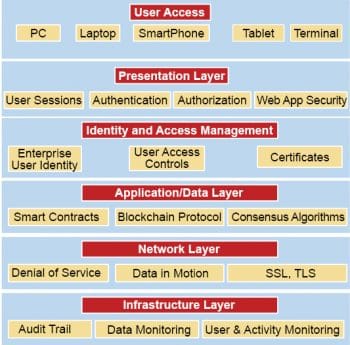
Security reference architecture in the blockchain
Blockchain security ensures that the right people, internal or external, get access to the appropriate data and information at the right time and place, within the right channel. Security prevents and safeguards against malicious attacks; it protects enterprise data assets by securing and encrypting data while it is in motion or at rest. It also enables organisations to separate roles and responsibilities, protecting sensitive data without compromising privileged user access.
The security at various layers for an enterprise application is classified as:
- User access layer security
- Presentation layer security
- Identity and access management layer security
- Application/data layer security
- Network layer security
- Infrastructure layer security
Figure 1 gives a layered view of the security approach with blockchain.
User access layer: Various stakeholders, both internal and external, are part of this layer. They are the primary users of the systems. Stakeholders use channels to interact with the enterprise. They engage with various departments or business units of the enterprise over multiple channels, both physical and digital.
Presentation layer: The front-end application security should ensure the following.
- Authentication: Authentication is the assertion by a subscriber to prove his/her identity. The authenticators and factors are:
- Something that one has to show (access card)
- Something one knows (password) and
- Something one is (biometric).
Authentication mechanisms should be commensurate with the strength of the identity model, the level of access and the sensitivity of the transaction. They must implement a combination of multiple authenticators (aka multi-factor authentication).
- Authorisation: Authorisation is a process to establish the right to perform transactions (actions), and claim access to assets and resources by a subscriber. In a blockchain application, the authorisation model should link the identity model and the authentication model. A good practice is to develop a multi-dimensional matrix of the account associated with identity, authentication and authorisation. This type of authorisation model will leave room to evolve into attribute based access control and role-based access control at the application level and, ultimately, at the organisational level, for enterprise blockchain applications. The authorisation model will typically address concepts such as separation of duties (SoD).
- Web application security: Web application security should include protection against vulnerabilities identified in OWASP (Open Web Application Security Project) Top 20.
Identity and access management layer: A digital identity is a unique representation of a person or thing engaged in a digital transaction. Identity proofing, or enrolment, is the physical or digital process of verifying a subject’s association with his/her real-world identity. An identity model and its associated identity proofing should provide reasonable assurance for the identity claimed by the subject. When the trust attributes of the blockchain application range from public to private, it is good practice to have multiple assurance levels for identity-proofing.
Application/data layer: The application security layer should ensure the following:
- Smart contracts and the blockchain processing platform are vetted to prevent things like calls to the unknown, valueless send, exception disorders, type casts, re-entrants, keeping secrets, immutable bugs, value (ether) lost in transfer and stack size limits.
- Blockchain protocols are vetted to prevent the blockchain from not converging as expected or into an unpredictable state, safeguarding the seed (genesis) block and ensuring timestamps are adequately protected.
- Consensus algorithms that enable transparency by imposing a transaction order to be correct for a new block added to the blockchain. This ensures that all the nodes in the network are in agreement on the new transactions added to the block.
Network layer: Depending on the nature of the application and the type of the network (Internet-based, leased lines, virtual private network, etc), there should be appropriate controls extracted from the system. Controls related to boundary protection (data-in-motion) and denial of service (DoS) should be considered.
Infrastructure layer: Audit trail is for all the transactions that will be maintained by the blockchain. Transactions ordering and approval will be done by the consensus service on board. This ensures that the transactions are correct and transparent to other participants/nodes in the network.
Data protection: Data protection is the process of safeguarding important information or data from corruption, compromise or loss. As blockchain is immutable, data cannot be compromised and appropriate measures like redundancy can be taken to protect it from corruption and loss.
User and activity monitoring: All valid transactions performed by users can be tracked on blockchain. User onboarding and management will be done by membership service shipped along with the blockchain.
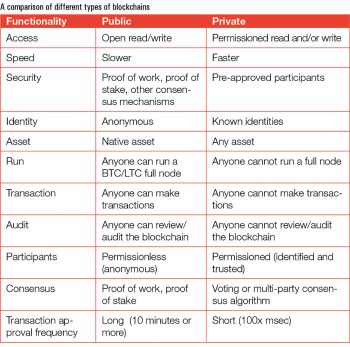
Blockchains are classified as public, private or hybrid depending on the nature of the application. Public and private blockchains share many similarities as well as differences in their functionality.
Here is a quick comparison between them, based on some recent functionality.
Public blockchain: This is completely open to the public, so anyone can join the network as a participant. A public blockchain typically uses some kind of mechanism to incentivise participating parties, which encourages a growing number of participants in the network. A public blockchain is open for everyone to read, send transactions and participate in the consensus process. The most prominent examples are the blockchains underlying Bitcoin and Ethereum.
Anyone can participate in a public blockchain, because it is open source and free to all, with no one in charge. There is no access or rights management done for a public blockchain and anyone can be a part of the consensus process. Because of this, anyone at any given point of time can join or leave, read, write or audit the public blockchain ecosystem, and the network will still be trusted.
Private blockchain: The private blockchain is the absolute opposite of the public version. The access to a private blockchain is limited to those involved in the creation of that particular network, or those granted access to it by the creators. The internal mechanics of a private blockchain can vary, from existing participants serving as types of administrators who decide on the inclusion of future entrants, to simple observers, but the public cannot access the private blockchain.
In private blockchains, the owner is a single entity or an enterprise, which can override/delete commands on a blockchain if needed. It is not exactly decentralised, and is called a distributed ledger or database that uses cryptography to secure it.
A hybrid/federated blockchain should be able to connect a public blockchain open to every single person in the world, with a private blockchain running in a fully permissioned environment, i.e., limiting the access of available information.
Conducting business over a decentralised hybrid blockchain reduces transaction costs, eliminates data redundancy and speeds up transaction times.
Whether a blockchain is private or public, the user group that has the access to the information on that blockchain needs to be determined.
Real world use cases of blockchain technology
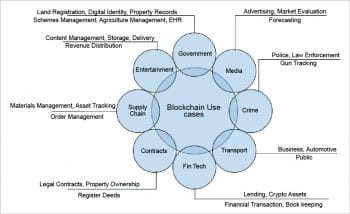
Enterprises are going to take advantage of this new technology by optimising their network and automating it without the need for human interference. The real disruption is that the trust is established through collaboration and code, rather than a central authority. For example, we no longer need a bank to make a money transfer around the world. We no longer need an escrow account to buy a home, or a real estate agent to facilitate the transaction. With the penetration and adoption of blockchain technology, almost all the industries will get impacted. Figure 2 shows the blockchain use cases across various domains.
The main benefits of blockchain technology are:
- Greater transparency — transaction histories are becoming more transparent through the use of blockchain technology.
- Enhanced security — there are several ways the blockchain is more secure than other record-keeping systems.
- Elimination of error handling through real-time tracking of transactions with no double spending.
- Improved traceability.
- Trusted record-keeping and a shared trusted process.
- Increased efficiency and speed, and a reduction in settlement time to mere seconds by removing intermediaries.
- Reduced cost and complexity, and material cost reduction through the elimination of expensive proprietary infrastructure.
- Full automation of transactional processes, from payment through settlement.
However, the blockchain is not recommended for the following:
- High performance (millisecond) transactions
- Small organisations (with no business network)
- Those looking for a database replacement
- Those looking for a messaging solution
- Those in search of transaction processing replacement
Blockchain has shown its potential for transforming traditional industries with its key characteristics — decentralisation, persistence, anonymity and auditability. Blockchain based enterprise applications increase the effectiveness of an enterprise, reduce cost of transactions and speed up interactions between the enterprises and its customers.
Blockchain provides better security during transactions of any value. It is a unique and a universal technology that helps to streamline and automate nearly all customer services or legal contracts, while increasing the transparency and effectiveness of enterprises. However, a lot of exploration is needed today in domains applying blockchain technology across various business units — on how to minimise enterprise costs, improve security in an era of cyber uncertainty and enhance customer delivery.
Acknowledgements
The authors would like to thank Hari Kishan Burle and Raju Alluri of the Global Enterprise Architecture Group of Wipro Technologies for their time and support to bring this article out as part of the Architecture Practice effort.
Disclaimer
The views expressed in this article are those of the authors and Wipro does not subscribe to the substance, veracity or truthfulness of the said opinions.










































































