Identity access management is a field that is focused on the management of the identity, access and security of applications; customer identity and access management (CIAM) is a subset of it. The latter is designed to scale up to handle thousands of users.
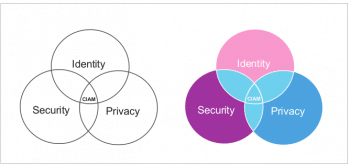
Customer identity and access management (CIAM) enables application architecture to handle customer identity and profile data in a secured and flexible solution. There are many CIAM solutions available in the market and they have much in common in terms of security, user management, profile management, policy management and more. CIAM is the integration of the identity, security and privacy of user data, as shown in Figure 1.
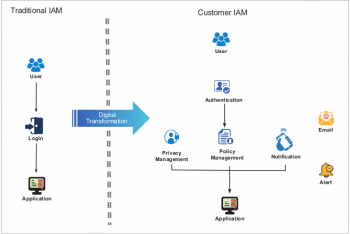
User authorisation and authentication is an integral part of most application designs, and identity and access management (IAM) is the solution that handles this. Typically, traditional IAM handles user logins with a handshake as shown in Figure 2, whereas security and user data management are not highly secured in such a solution. CIAM is the digital way of handling user management and nowadays, third party CIAM solutions provide APIs for this management. CIAM provides easy integration with any cloud based solution or enterprise application.
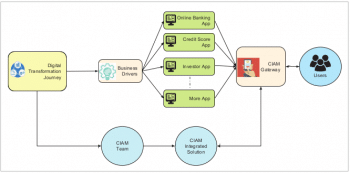
In a typical banking IT architecture, CIAM helps as a one-point solution to integrate user management (as shown in Figure 3). Here, multiple applications handle user data in a secured, robust gateway and facilities like SSL-handshake, multi-node authentication, social networking identification and linking can be implemented without much complexity.
Broadly, CIAM features are categorised as follows:
- Seamless customer experiences – This provides an easy visualisation solution during application integration and handles user access without much complexity.
- Security requirements – Provides the highest possible security for user data with a data store either integrated to the CIAM solution or connected from a CIAM application.
- Performance and scalability – Handles any number of concurrent user accesses without trouble or delay in application access.
- Privacy and regulatory compliance – With GDPR (General Data Protection Regulation) and customer personal data security in place for the regulatory restrictions of different countries, CIAM plays an important role in monitoring, reporting and notification alerts.
- Adaptability – The CIAM solution should have futuristic architecture to handle easy adoption to any architecture (e.g., cloud adoption, on-premises to cloud synchronisation, etc).
When preparing an integration architecture for an enterprise solution or cloud native adoption, one has to define the technical expectations for a CIAM solution, such as:
- User repository type
- Social ID provider
- Open IdP
- Two-way authentication (certificate, SSL handshake)
- Multi-channel access (Web, mobile, standalone)
- SaaS offering
There are many CIAM frameworks available, like Microsoft AD, IBM Federated IM, Gigya and Janrain, to name a few. Some of them are open source and some proprietary with a commercial licence model for integration. Many of them support cloud native adoption, on-premises integration and authorisation using social network accounts. In this series, I will go on to discuss the most popular CIAM frameworks — looking at how to integrate them in the application architecture, while covering their pros and cons in terms of the features supported.