Security breaches in a computer network can have disastrous results. They may be the cause of company secrets leaking out or result in industrial espionage. A common breach is the Man in the Middle or MITM attack. This happens when malicious players insert themselves in a network and intercept all incoming and outgoing traffic, either passively or actively.
An MITM attack is when a malicious user eavesdrops on the conversation or modifies the conversation between two parties interacting in cyber space. When the malicious user is only eavesdropping on the conversation, it is a passive attack, but modifying the conversation is considered an active attack. Consider two users Alice, Bob and a malicious attacker. If an MITM attack is launched in this case, any conversation between Alice and Bob will go through the attacker.
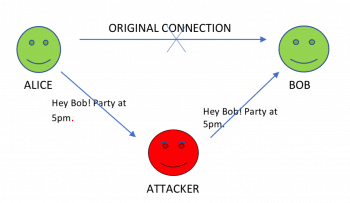
In this case, the attacker is just looking at the conversation. Therefore, this is a passive attack, which is difficult to detect as no data is modified.
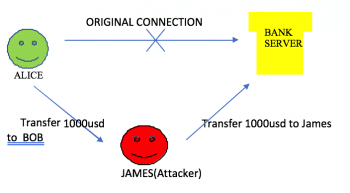
This attack can also be extended between a Web server and a client. Consider a scenario in which Alice is looking forward to transferring US$ 1000 to Bob online. A malicious user named James can launch an MITM attack and manipulate the conversation between the bank server and Alice to transfer the US$ 1000 to himself (James) instead. As the data is being modified, this is an active attack.
When comparing active and passive attacks, the latter may seem less dangerous but they are not. A passive attack might lead to the revelation of sensitive information to unauthorised (or unwanted) people. As the information is not tampered with, it is difficult to detect the information leakage. For example, consider the situation of a question paper leakage. Though no data in the question paper is tampered with, the leakage reduces the credibility and quality of the exam. Therefore, a passive attack is as dangerous as an active attack.
This article describes how a passive MITM attack is launched and some of the security measures that can be taken against the attack. We have used the following open source tools to explain MITM: EtherApe, ARPspoof, ssl-strip and Driftnet.
Each tool is used for a particular purpose:
1. Network monitoring is done using EtherApe
2. An MITM attack is launched using ARPspoof
3. The victim is monitored using Driftnet
EtherApe
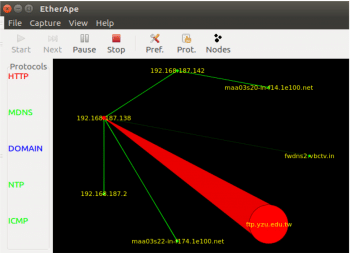
EtherApe is a network monitoring tool. It can be invoked by typing etherape in a terminal. It gives a graphical view of the communication (data exchange) between devices in the network. The graph includes the IP address or the domain name of the server or device being accessed. EtherApe also gives data about the protocols being used during the communication.
In Figure 3, the colour of the lines represents the protocol written on the left (red is for HTTP). The width of the lines represents the amount of traffic. You can see in this figure that there is heavy HTTP traffic.
Network monitoring gives attackers information on the Internet and intranet usage within a network. This makes it easy for the attacker to conclude patterns of usage, prior to planning an attack. For example, if the attackers plan to attack from another user’s computer, they can monitor the traffic of all the users in the network and discover the time slot a given user will be absent, such as the time the victim goes to lunch every day. They can use that system to run malicious programs during that particular time slot.
ARPspoof
Let us first understand how the Address Resolution Protocol (ARP) works. Every packet going out of the device consists of seven layers (the OSI model). Each layer helps the packet in reaching the destination. Therefore, information in each layer is important. ARP is a Layer 2 protocol of the OSI model (Data Link layer). In the Data Link layer, the MAC address of the next physical device in the path is filled. Every device has a table known as ARP cache that maps the IP address to the corresponding MAC address. Devices use this table to fill the MAC address. When there is no entry corresponding to the IP address, then the ARP protocol is invoked. The ARP protocol broadcasts packets to find out the MAC address to the corresponding IP address. The device replies with its MAC address.

ARP spoofing
While sending out the ARP requests, if a malicious user replies with his MAC address, a legit IP address is mapped to a malicious MAC address. In the path to the destination, only the data in the Link layer and Physical layer are modified by the transit devices. Therefore, all the data goes through the malicious user, who can modify the data or just watch it.
In a network, all the packets going outside the local network go through the gateway. Performing ARP spoofing to intercept the packets from a victim to the gateway will help the attacker watch all the work done over the Internet by the victim.
There are many tools that can perform ARP poisoning. In this article, we will use the ARPspoof tool in Kali Linux.
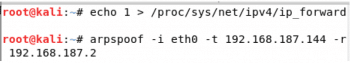
When the attackers get the packets from the victim, they can forward them to the intended destination by using the following command:
echo 1 > /proc/sys/net/ipv4/ip_forward
To perform ARP spoofing over an interface between a victim and the gateway, the following command is used:
arpspoof –i <interface-name> -t <victim IP> -r <gateway IP>
ARPspoof sends the victim machine the MAC address of the attacker as the gateway. Therefore, any traffic going outside the local network goes through the attacker.
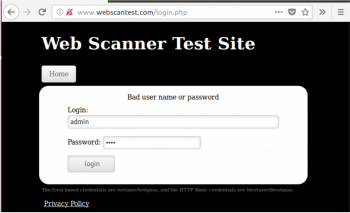
Getting the user name and password
When the victim logs in to any HTTP or HTTPS site, the credentials can be obtained using ssl-strip along with ARPspoof.
Ssl-strip looks for HTTP traffic on the network, for HTTP links that redirect to HTTPS links and redirects those links to HTTP. For example, http://domain.com/home.php redirects to https://domain.com/login.php. Ssl-strip changes this to http://domain.com/login.php.
As the attacker machine is between the victim and the gateway, all the traffic goes through it. Using ssl-strip, an attacker can get the credentials from those packets.
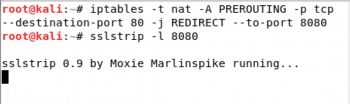
To set up ssl-strip, first forward all the packets coming on Port 80 (to the attacker machine from the victim machine) to Port 8080 for ssl-strip to analyse. Then set up ssl-strip on Port 8080.
For the purpose of this article, we have used http://www.webscantest.com/
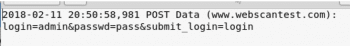
As the victim clicks on the login button, the packets are forwarded to the attacker machine (because of ARPspoof). This traffic is forwarded to Port 8080 where ssl-strip analyses it. Ssl-strip creates a log file called sslstrip.log in the home folder, which contains the user credentials.
Driftnet
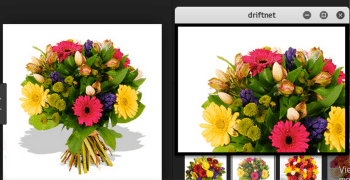
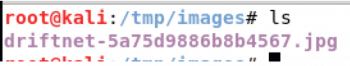
Driftnet is a network sniffing tool on Kali Linux that can be used to see the images viewed by the victim on the network. The images can be optionally saved using –d. By default, Driftnet sniffs over all the network interfaces. The sniffing can be restricted to a particular interface using the –i option.
driftnet –i <interface> -d <directory path to save the images>
The above command opens a window with a view of the images opened by the victim.
As the –d option is used, the image is also saved in the given directory.

Testing if someone is sniffing
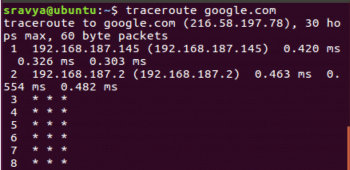
To find out if someone is sniffing the network, from the victim machine, perform traceroute (tracert in Windows) to google.com (any site hosted outside the local network will work).
We can see that the first hop is 192.168.187.145 (the attacker machine) and then it goes to 192.168.187.2 (the gateway). This type of result shows the clear possibility of network sniffing.
Security measures against attacks
The best security measure against all the above-mentioned data leaks is using full-fledged ssl websites (without any redirects or linking). As the data passing through is encrypted, the sniffer cannot make sense out of it.












































































