
Heres an introduction to Netcat, the powerful computer networking utility that performs numerous network related tasks. It is designed to be a dependable back-end, which can be run independently or in conjunction with other programs and scripts.
If you are worried about whether Netcat is software or a knife, as the headline states, let me clear your doubts – it is an open source tool that has a lot of functionalities, just like the Swiss army knife.
Netcat is an open source UNIX utility written in C. The name Netcat is derived from ‘Net’ (for networking) and ‘cat’ for concatenating data to a file. So, Netcat can be described as a tool for performing network related tasks and storing the output of the operations into a file, if required. This tool has been developed by someone who uses the pseudonym Hobbits. The beauty of the tool is that it can be either used directly from the terminal or be controlled by a user written program. You can use Netcat for creating a simple chat server, to scan the network for open ports, and more. It has the ability to send data packets over the network using the TCP and UDP protocols; however, TCP is used by default.
Versions of Netcat
i. Netcat-traditional: The original version of Netcat
ii.Netcat-OpenBSD: Developed Netcat with some more options
iii. Ncat: The Netcat version developed by the Nmap community
In this article, I will be using Netcat-OpenBSD.
Terms used
Listener: A computer in which Netcat is listening on a port.
Client: A computer that tries to connect and/or give commands to another computer on which Netcat is running.
Installation
To install Netcat, run the following code:
sudo apt-get install netcat-openbsd
Technical details
There are two systems (VMs) set up on the network with the following IP addresses:
a) Ubuntu-Mate: 192.168.56.102 (client)
b) Ubuntu: 192.168.56.103 (listener)
Uses of Netcat
Creating a chat server: A chat server is a system used for the purpose of chatting. Using Netcat, creating a simple chat server for two people to chat is very easy. You just need to type the following commands.
For the listener, type:
nc -lp <PORT>
For the client, type:
nc <IP ADDRESS> <PORT>
Where <IP ADDRESS> is the IP address of the listener and <PORT> is the port of the listener.
Here is an example.
chandu@ubuntu:~$ nc -lp 1234 Hello OSFY readers !!! chandu@ubuntu:~$ nc 192.168.56.103 1234 Hello OSFY readers !!!
The server stops if either of the users stops chatting. To make the chat server permanent, you can add a -k tag in the listener terminal.
An example is given below.
Listener : nc -k -lp 1234
Web server: A simple static Web page can be hosted on a specific port on a system using the following commands:
nc lp <PORT> -q 1 < index.html
where index.html is an HTML page on the hosted system as below.
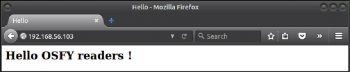
chandu@ubuntu:~$ cat index.html <html> <head> <title>Hello</title> </head> <body> <h2> Hello OSFY readers !</h2> </body> </html>
If you wish to open the Web page using a browser, you could set the port to be 80.
nc -lp 80 -q 1< index.html
When you open a browser and enter the IP address of the computer as the URL, you will get the contents of your HTML page [Figure 1]. When you see the terminal, you will find a lot of text, which is actually implemented at the background when browsing. But if you reload the page, you cannot find the page, because Netcat stops successfully after sending the contents of the HTML file.
To make a permanent Web server on a port 80, use a while loop:
while true; do nc -l 8888 -q 1 < index.html; done
Note: You should do this as a root user because starting a service requires root privileges.
Port scanning: Port scanning is very important for sys admins and pentesters. To use Netcat for port scanning use the following command:
nc -v -z -w <SEC> <IP ADDRESS> < PORT RANGE: 1-1000>
where,
-v: verbose mode
-w: wait for
SEC: number of seconds to wait
-z: operate in zero IO mode, i.e., display without information and without analysing the response.
For example:
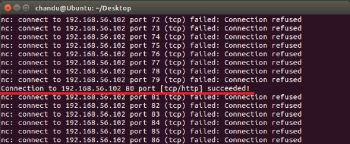
nc -v -z -w 1 192.168.56.102 1-100
You could scroll up to view which ports are open [Figure 2]. You could also scan one port at a time using the exact port.
nc -v -z -w 1 192.168.56.102 80
By default, Netcat uses a TCP connection. You can also scan domain names in a UDP connection. You have to use -u, as follows:
nc -v -z -w <SEC> -u <IP ADDRESS> <PORT RANGE: 1-1000>
where -u is the UDP connection.
Note: If the Netcat-traditional version is used for port scanning, ‘-v’ should be replaced by ‘-vv’. The output will show only the open ports. It hides the ‘Connection refused’ information, thus making the output easy to read.
File transfer: Using the same logic of the chat server, one could send and receive the contents of a file. You could do this in two ways.
1. If you want to send a single file, you could directly send it using the following commands.
For the sender, type:
nc -lp 1234 < testfile.txt
where 1234 is the port number and textfile.txt is the file to be transferred.
For the receiver, type:
nc 192.168.56.103 1234 > received.txt
2. If you have a lot of files, you can zip them into a single file and then send the zipped file over the network using Netcat. To transfer all the HTML files in a folder, use the following commands.
For the sender, type:
tar zc *.html | nc lp 1234
For the receiver, type:
nc 192.168.56.103 1234 | tar zx
Note: Sender and receiver commands can be used interchangeably. If you have to copy files from one computer to other computers on a network, you could use the above method in a loop.
For the sender, type:
while true; tar zc * | nc -lp 1234 ; done
Netcat overwrites a file with the same name as mentioned. Make sure that you save the receiving file with a temporary name and then try renaming it to avoid unexpected overwrites.
Banner grabbing: Banner grabbing is a technique to get information about a service running in an open port.
For example, if you know a service is running on a specific port on a specific machine, you could try giving commands (which may not be correct). The machine at the other end will send you a response stating that your request is either good or bad. In this response, you can actually find out the name of the service running on the port. This functionality of Netcat is more useful to network administrators who are monitoring the entire network for malicious activities.
nc <IP ADDRESS> <PORT>
You can give any command to get the response.
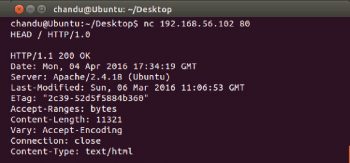
If you are trying to get the service name running on port 80 (http service), try giving the command HEAD HTTP/1.0 and you will get the response with the name of the service utilising port 80 [Figure 3].
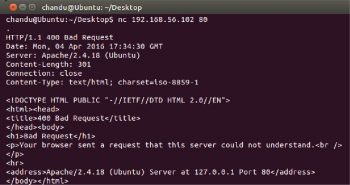
You can also give a random command, and you will get a ‘BAD REQUEST’ response with the banner of the service.
From Figures 3 and 4 one can find that the service running on port 80 is Apache/2.4.18 and the base system OS is Ubuntu.
Getting remote shell: Netcat has made it so easy for network admins to access the terminal of various systems, remotely. To access the remote terminal, the listener (system whose terminal should be remotely accessed) should use the following command:
nc -lp <port> -e /bin/bash
Note: This functionality is not present in OpenBSD. The above command works only with the Netcat-traditional version.
Then, to access the remote shell, just connect to the listener using the following command:
nc <IP ADDRESS> <PORT>
Netcat can be used for a lot of other purposes such as transferring images or data files. For Windows users the above commands get slightly changed. You can even try to code your own program which can automate your daily network management tasks.








































































