This article gives you an overview of malware code obfuscation. Nowadays, malware tends to remain hidden during infection and operation, avoiding detection and analysis by security tools. Generally, code obfuscation is malwares best friend. It provides high persistence to the malware samples. Code obfuscation is a technique that uses binary and textual data in an unreadable format that cannot be reverse engineered.
A lot of malware have the capability of self-encryption and high persistence. Most malware use the XOR self-encryption/decryption routine. XOR patterns for obfuscating the malicious code are very similar in working patterns:
i) Out of a possible 255 keys ranging from 0255, the attacker picks a 1 byte key
ii) The attacker obfuscates the code by encoding it with the 1 byte key value, iteratively
iii) The attacker can pick the longer key size to obfuscate the code for better persistence
iv) The attacker protects the code (encoded string) by iteratively XORing each byte with the key
XOR is basically very simple, symmetric and easily reversible with a single functionality for both encryption and decryption. Encrypted malware is hard to detect by the traditional security solutions like anti-virus software, intrusion detection systems and intrusion prevention systems. The only pattern that can be recognised is the XOR pattern used for the encryption/decryption routine. Here, REMnux is used to analyse the malware samples for possible XOR patterns.
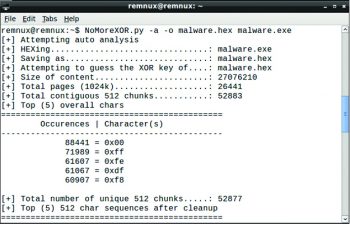
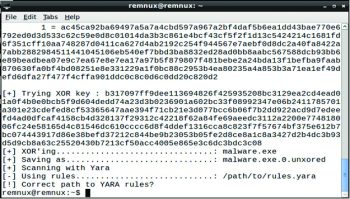
NoMoreXor
NoMoreXor is a command line utility used to analyse and guess the 256 byte XOR key using the frequency analysis technique. The utility is bundled in REMnux and is freely available on Git at https://github.com/hiddenillusion/NoMoreXOR
The syntax is:
NoMoreXor.py -a o [outputfile.extension] [malwaresample.extension] |
Heres an example:
NoMoreXor.py -a o malware.hex malware.exe |
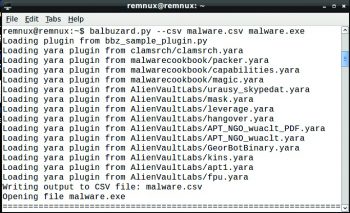
Balbuzard
Balbuzard is a malware analysis tool that is used to extract patterns from malicious files and to crack obfuscated code using XOR. It is also used to extract strings/patterns and embedded files.
The syntax is:
Balbuzard.py [option] [filename.extension] |
Heres an example:
Balbuzard.py --csv malware.csv malware.exe |
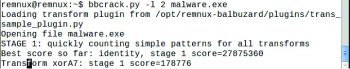
Bbcrack
Bbcrack is a supplementary tool used to brute-force XOR keys based on patterns of interest.
The syntax is:
bbcrack.py [option] [filename.extension] |
An example is:
bbcrack.py l 2 malware.exe |
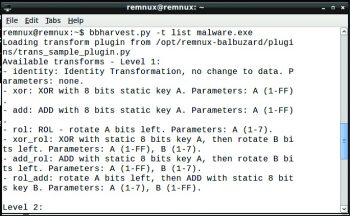
Bbharvest
Bbharvest is also a brute force tool used to extract XOR keys that are specifically targeted against single obfuscated strings/patterns in malware.
The syntax is:
Bbharvest [option] [filename.extension] |
Heres an example:
bbharvest.py l 2 malware.exe |
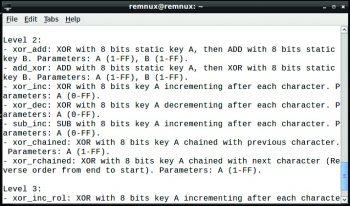
Bbtrans
Bbtrans is used to apply transforms over the malware samples.
The syntax is:
Bbtrans.py [option] [filename.extension] |
And an example is:
bbtrans.py l 2 malware.exe |
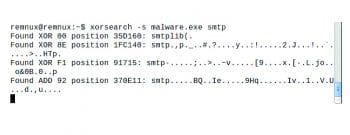
Xorsearch
Xorsearch tools help to find all possible 1 byte key values. However, the particular string that we are looking for is known and one good value is smtp, because some malware samples often send mail to the command and control server.
The syntax is:
Xorsearch [option] [filename.extension] <string> |
An example is:
Xorsearch s malware.exe smtp |
References
[1] https://en.wikipedia.org/wiki/Malware
[2] www.threattracksecurity.com/enterprise-security/malware-analysis-sandbox-software.aspx
[3] https://zeltser.com/build-malware-analysis-toolkit/
[4] https://isc.sans.edu/forums/diary/Wipe+the+drive+Stealthy+Malware+Persistence+Mechanism+Part+1/15394/
[5] http://digital-forensics.sans.org/blog/2013/05/14/tools-for-examining-xor-obfuscation-for-malware-analysis?reply-to-comment=15387
[6] http://www.decalage.info/python/balbuzard













































































