A firewall isolates a trusted, secure internal network from another network like the Internet, which is not regarded as either trusted or secure. Firewall Builder is an open source product that makes it easy to configure firewalls.
In computing, hardening is the process of securing a system by reducing its areas of vulnerability. This is done by removing needless software, unnecessary logins and unnecessary services. There are various other methods of hardening, which may involve applying a patch to the kernel, closing network ports, setting up intrusion-detection/prevention systems and firewalls.
A firewall protects the resources of a private network from users of other networks. Organisations that allow their employees to access the Internet install a firewall to prevent unauthorised entities from accessing their own core services and core data, which is often confidential. Policy is the term often used in relation to firewalls. A policy can be described as a set of business rules or restrictions that are implemented with the use of a firewall.
One of the firewall’s methods is to screen requests to make sure that they come from acceptable sources (domain names and IP addresses). Many companies make firewall products that include features such as automatic alarms at given thresholds of attack, logging, reporting, and a graphical user interface to manage the firewall.
Firewall Builder has features such as a drag-and-drop GUI, shared objects and search-and-replace. It is available under GPL; its GUI is based on QT, and hence requires the QT runtime libraries and development packages if you wish to build from source.
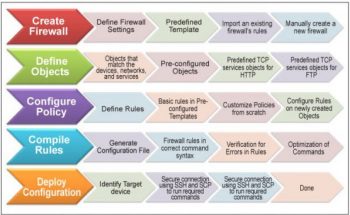
Firewall Builder is based on the concept of objects. With this concept, users create objects such as IP networks and IP addresses to represent entities that will be used in firewall rules. Objects are stored in libraries. There are two object libraries that come with Firewall Builder. The User library stores objects that the user creates while the Standard library, which is a read-only library, contains hundreds of pre-defined objects such as common TCP and UDP services. Once you create a policy with firewall rules in Firewall Builder, the very next thing you need to do is to compile the policy. This converts your rules from the Firewall Builder syntax to the command syntax used by the target firewall platform. You need to recompile the policy in case you change the rules of a firewall.
Features
- It generates platform-specific firewall commands.
- Typing firewall commands is an old school approach; Firewall Builder allows you to create objects such as an IP address to represent your HR server.
- Groups of objects can be created and can be used to create a firewall rule.
- Easy search facility to find where objects have been used.
- Configuration versioning-this is a facility to automatically roll back on the previous firewall configuration.
Pre-defined templates for firewall rules and familiar deployment scenarios. - Start-up scripts – pre- and post-firewall scripts.
Supported platforms
Firewall Builder supports policy configuration and management on Linux iptables, Cisco ASA/PIX, Cisco Firewall Service Module (FWSM), Cisco router access control lists (ACL), OpenBSD pf, HP ProCurve ACL, FreeBSD ipfw and ipfilter.
Firewall and Cloud Computing
Scenario: For an e-commerce application, secure one or multiple public-facing Web servers. Regardless of whether that server is situated in DMZ, Amazon’s Cloud, Rackspace Cloud, or in Private Cloud, it requires the same level of risk management. Considering this factor, it may not be important where the Web server is hosted. A single firewall policy for Web Server and Database Server can be enforced. Hierarchical policies can be made and enforced as per your convenience to make the application more secure.
In this situation, the easiest implementation is to leverage the firewall built into each operating system. If we define the organisation’s rules within the host-based firewall as per policies, the risk mitigation policy is not dependent on the logical location, and hence it can scale as required. All we need is a good tool for managing the built-in firewall without complexities.
How to install Firewall Builder in a Cloud environment
In Private Cloud, Firewall Builder can be installed in various operating systems and be used according to the environment or the access to the virtual machine that cloud service providers allow.
For Red Hat, Fedora, OpenSUSE, and others, download and install the Firewall Builder RPM, e.g., fwbuilder-5.1.0.3599-1.el5.i386.rpm
You need to install libxml2 v2.4.10 or newer, libxslt v1.0.7 or newer, ucd-snmp or net-snmp, and QT 4.3.x, 4.4.x, 4.5.x, 4.6.x to satisfy dependencies.
Navigate to your download directory and execute the following:
rpm -i fwbuilder-5.1.0.3599-1.el5.i386.rpm |
For Ubuntu, download and install the Firewall Builder package, e.g., fwbuilder_5.1.0.3599-ubuntu-precise-1_i386.deb
You need to install QT 4.3.x, 4.4.x, 4.5.x, and 4.6.x to satisfy dependencies.
Navigate to your download directory and execute the following:
dpkg i fwbuilder_5.1.0.3599-ubuntu-precise-1_i386.deb |
For a Windows installation, double-click the Download fwbuilder-5.1.0.3599.exe (18.0 MB) link, then follow the step-by-step instructions in the installation wizard.
Figure 3 shows how Firewall Builder works.
Now that you know what Firewall Builder is all about, go ahead and use it to protect yourself and your organisation from unwanted intrusions.













































































Howdy, Your comparison table has the version numbers for FWbuilder and UFW swapped.