
Cuckoo is a leading open source malware analyser. The Cuckoo sandbox facilitates effective analysis of various types of malware by monitoring their behaviour in a secure and isolated environment with the help of virtual machines. Based on Python, it is definitely a must-have tool in the armoury of any computer security expert.
Malware is a term that refers to all types of malicious software, and is a serious threat to the IT backbone of any organisation. The impact of malware is far-reaching in both technical and economical dimensions. The wide spectrum of malware, comprising various types of attacks targeting different vulnerabilities, have made their detection and analysis a complex mission. Figure 1 illustrates a few important types of malware.
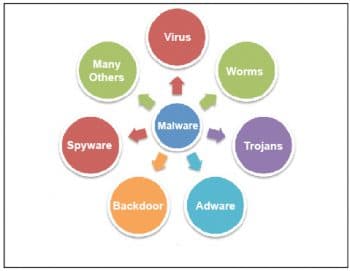
Though the mode of attack, payload, etc, of one type of malware might be different from that of another category, all of them hamper the smooth functioning of a system. Hence, it becomes mandatory to restrict their proliferation and protect systems from their negative impact. To achieve this goal, one important step is to analyse the malwares various dimensions. This article explores a leading open source malware analysis tool called Cuckoo.
Malware analysis
Malware analysis is the task of putting a malware under the scanner, and checking its structure and behaviour. This analysis is classified into two types, as follows:
- Static analysis: This analysis focuses on the different components of the malware file, and is primarily based on the structure of these files. It uses the principles of reverse engineering.
- Dynamic analysis: This works by logging the behaviour of the malware in a safeguarded environment, like a sandbox. Based on the nature of activities that the analysed malware have carried out inside the sandbox, the future sequence of actions is decided upon.
Cuckoo
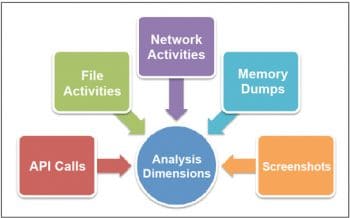
Cuckoo facilitates analysis in both static and dynamic dimensions. It analyses the malware by logging their activities, and provides a complete report containing details about the following parameters (as shown in Figure 2):
- The details regarding all the API calls initiated by the malware and chained processes
- The file-related details like creation, deletion and modification
- The network activities, which are understood through the network traces
- Memory dumps provide a clear picture about the internals of the malware activities
- The facility to snap screenshots of the system while the malware is in operation provides clear insights on the various operations carried out by the malware
The evolution of Cuckoo
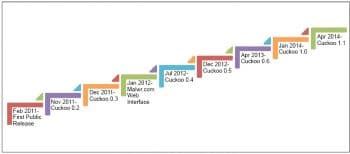
The evolution of Cuckoo began with the Google Summer of Code 2010. The Cuckoo timeline is shown in Figure 3.
- The first public release of Cuckoo was in February 2011, when it was part of the Honeynet Project (http://www.honeynet.org/project/Cuckoo).
- Cuckoo version 0.2 was released in November 2011, with improved reporting features.
- In quick succession, by December 2011, version 0.3 got released.
- In January 2012, malwr.com, the Web interface for the Cuckoo sandbox (which is open to the public), was launched. With this facility, anyone can submit their file for malware analysis and the results are sent to them.
- Cuckoo version 0.4 was launched in July 2012 and version 0.5 in December 2012.
- In April 2013, version 0.6 was launched with subsequent updates to malwr.com.
- In January 2014, the Cuckoo sandbox version 1.0 was launched, and the most recent release of Cuckoo 1.1 was in April 2014.
From this timeline, you can observe that Cuckoo has evolved from a simple project in 2010 into a professional malware analysis tool with progressively quicker updates from Cuckoos development team.
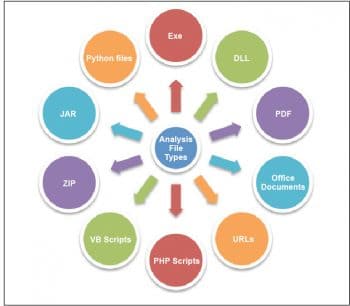
Cuckoo can be used to analyse various types of files as shown in Figure 4.
The Cuckoo methodology
The malware analysis process of Cuckoo involves two major components: the host and guest (virtual) machines.
The process is as follows:
- The Cuckoo central component runs in the host machine. This central component is the pivot around which the entire analysis process revolves. The optimal configuration for the Cuckoo host is Ubuntu.
- The malware files are analysed inside guests, which are protected virtual environments. The configuration for guests could be Windows version 7, Vista, etc. It supports Mac OS X as well.
- For each malware file submitted for analysis, a fresh virtual machine is launched and analysis is done in that protected environment.
- The host machine accesses the results of the analysis process in a safer manner.
Cuckoo installation
As of now, Cuckoo doesnt come as a simple click-and-install application. The system needs to be configured with many dependencies, libraries, etc. Though the installation is a bit lengthy, it is worth spending time on it, if you require its malware analysis capabilities for your organisation. The installation process can be divided into two major phases:
- Preparing the host
- Preparing the guest
Preparation of the host
The host preparation involves installing the following libraries and software for the effective functioning of Cuckoo:
- Python libraries
- Virtualisation software
- For network analysis, tcpdump is needed
- To enable memory analysis, Volatility (https://code.google.com/p/volatility/ ), an advanced memory forensic framework, is needed
- The Cuckoo sandbox is required for the core analysis component
- Various .conf files like cuckoo.conf, memory.conf, etc, need to be configured
As Cuckoo is developed using Python, the host machine should have Python installed on it. The recommended Python version is 2.7, which can be installed using the following command:
$ sudo apt-get install python
If the Web interface that is based on Django is required, then MongoDB needs to be installed, as follows:
$ sudo apt-get install mongodb
Cuckoo needs SQLAlchemy and BSON, which can be installed using the following command:
$ sudo apt-get install python-sqlalchemy python-bson
To analyse the network activities, Cuckoo needs tcpdump, which can be installed as follows:
$ sudo apt-get install tcpdump
The libraries listed below are not absolutely mandatory but they would make Cuckoos analysis much more effective, if installed.
- Dpkt Python packet creation/parsing library
- Jinja2 for HTML reports
- Yara for signature matching in Python
- MAEC (malware attribute enumeration and characterisation)
- Magic library for file format identification
- Volatility for memory forensic analysis which can be acquired from https://github.com/volatilityfoundation
For the virtualisation software, VirtualBox is preferred. Though Cuckoo supports other virtualisation tools as well, the association between VirtualBox and Cuckoo goes back to earlier versions, which makes it the preferable tool. VirtualBox can be acquired from https://www.virtualbox.org/wiki/Downloads. VirtualBox binaries are available for Windows, OS X, Linux and Solaris hosts.
For the seamless functioning of Cuckoo, creating a separate user is preferred in the official documentation. The latest version of Cuckoo can be downloaded from the official website (http://www.cuckoosandbox.org/download.html).
Cuckoo configuration is done using six different configuration files as listed below. The detailed information on each of these files configurations is available at http://docs.cuckoosandbox.org/en/latest/installation/host/configuration/.
- cuckoo.conf for the general analysis process
- auxiliary.conf for handling optional modules
- machinery.conf for virtualisation software options
- memory.conf for configuring Volatility
- processing.conf for the settings of processing modules
- reporting.conf for various report formats
Preparation of the guest
As the malware analysis is performed on the virtual machines, they need to be prepared properly. After preparation, they need to be configured as explained in the following instructions:
- Python needs to be installed on the guests.
- Python Image Library is also preferred for making screen snaps when the analysis is going on.
- The Windows firewall and automatic updates need to be disabled, failing which the behaviour of the malware may be affected, which would reduce the power of the analysis on the network front.
- Virtual networking should be configured for communication between host and guest. The guests should be configured with static IP addresses. (It is to be noted that DHCP is not supported.)
- Cuckoo uses an agent to establish communication between host and guest. The agent.py file needs to be copied into the guest.
The re-imaging tools like Fog, Clonezilla and Deepfreeze can be used for storing system images. Once the image of the guest machine is successfully taken, it shall be used by the Cuckoo sandbox. The official documentation clearly illustrates the installation process in detail.
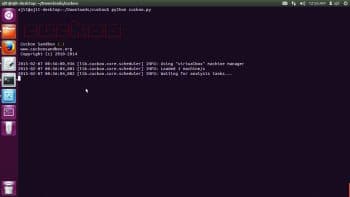
File submission
Once the configuration is successfully done, Cuckoo (see Figure 5) can be started using the following command:
$ python cuckoo.py
The malware file can be submitted using the
submit.py utility:
$ ./utils/submit.py /path/to/binary
Instead of this binary file, a URL could also be submitted for analysis.
Malware analysis results
After the successful completion of the analysis, the results are stored in the storage/analyses directory. The results of the analysis are given for various parameters as shown below:
- analysis.log: This provides information regarding the creation of processes, files and errors, if any, raised when the malware was in execution.
- dump.pcap: This is the network dump gathered by tcpdump.
- memory.dmp: This is where the complete memory dump is provided.
- The Files directory provides details on the files that the malware interacted with.
- The Logs directory provides all the log information.
- The Reports directory gives a list of all the reports prepared by Cuckoo.
- Shots lists all the screenshots made when the malware was in execution.
Malwr.com submission
If you simply require to analyse a few files and do not want to configure Cuckoo in your system, the public Web interface provided in malwr.com (as shown in Figures 6 and 7) can be used. Once the file is submitted to malwr.com, the results are provided in a clearly formatted manner through the Web interface.
Cuckoo provides an effective and efficient malware analysis mechanism. The power of Cuckoo can be understood from the testimonials provided by popular organisations like Virustotal, Threat Stream, In2Sec, etc, which use Cuckoo. Another crucial advantage of using Cuckoo is the ability to extend and customise its open source code to suit an organisations individual requirements. Hence, Cuckoo is undoubtedly a must-have tool for security experts and malware researchers.
References
[1] http://docs.cuckoosandbox.org/en/latest/
[2] https://malwr.com/
[3] http://www.cuckoosandbox.org/









































































