Wireless sniffing involves the capture of all the packets that pass through a given wireless network interface. Sniffing is one of the most effective techniques used when attacking a network. Active sniffing involves injecting packets into the network, which leads to traffic. This article deals with active sniffing and ARP spoofing.
In a local area network or LAN, the term sniffing refers to capturing packets transmitted over the network. An attacker may use either the passive or active method of sniffing. Passive sniffing is done on a HUB environment, using promiscuous mode.
ARP spoofing is used for active sniffing. But before discussing ARP spoofing, lets be clear about the ARP protocol.
Address resolution protocol (ARP)
ARP refers to the process of finding the MAC address of a computer in a network. There are two types of ARP messages that can be sent:
- ARP request
- ARP reply
In an ARP request message, the sender broadcasts the ARP request to all computers in a subnet to know the MAC address of the desired IP address.
In an ARP reply, the target system sends the reply to the sender, giving the MAC address. The ARP reply is a unicast response.

An ARP cache
To reduce the number of ARP requests, the system maintains a finite ARP cache for a short period of time. This contains the IP-to-MAC address mapping. When one system wants to send a message to another, it first checks its ARP cache. You can view the ARP cache of your computer using the following command:
arp -a |
ARP spoofing
ARP spoofing, also known as ARP cache poisoning, is a type of attack in which the MAC address of the victim machine in the ARP cache of the gateway, along with the MAC address of the gateway in the ARP cache of the victim machine, is changed by the attacker.

How to perform ARP spoofing
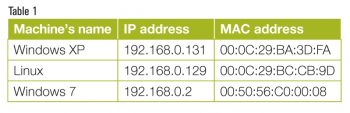
In order to demonstrate ARP spoofing we need three machinesa gateway, an attacker and a victim. All experiments are performed in VMware 8.0, taking a Windows 7 system as the gateway, a Windows XP system as the victim and a Linux (Backtrack) system as the attacking machine.
The IP address and MAC address of each machine is given in Table 1.
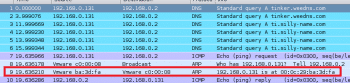
Step 1: On the attacker side, start passive sniffing by launching the Wireshark tool. Sniff for any ARP reply packets, but first select the interface eth0.
Step 2: Capture the ARP reply packet as shown in Figure 3.
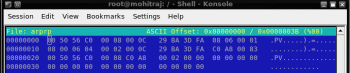
Step 3: Select Export Selected Packet Bytes after right-clicking on the frame of the ARP reply. Save the file named arprp and open it in the hex editor using the following command:
# hexedit b arprp |
The file will appear as shown in Figure 3.
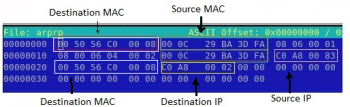
Our aim is to send a spoofed packet to the victim. In order to create a spoofed packet, some changes will have to be made to certain fields, as shown in Figure 4.
Change the following fields:
Destination MAC = Victim machines MAC (00:0C:29:BA:3D:FA)Source MAC = Attacker MAC (00:0C:29:BC:CB:9D)Source IP = Gateways IP (192.168.0.2 in Hex code C0 A8 00 02)Destination IP = Victim Machines IP (192.168.0.131 in Hex C0 A8 00 83) |
Step 4: Save this file with a new name, like arprpnew. Then place this file on the LAN with the help of the following command:
# file2cable -i eth0 f arprpnew |
Step 5: See the effect on the victim machine, before spoofing and after spoofing, as shown in Figure 5.
Use the following command:
>arp -a |
The victim machines ARP cache has the same MAC address for different IP addresses. In this way, the attacker makes a new spoofed packet for the gateway and places this on the LAN.
Note: Attackers can only update the cache, which means they cant insert the entries into the cache.
After some time, entries are deleted automatically. So there is a need to send packets again and again, for which you need to create a shell script named arpp:
#/bin/bashfor((i=0;i<100;i++)dofile2cable -i eth0 f arprpnewsleep 1000doneGive permission 770 to this file# chmod 770 arppRun the script# ./arpp |
This is the manual method to do ARP spoofing. We can perform this with the help of some tools like Cain and Abel and Ettercap.


ARP spoofing with the help of Ettercap
Install Ettercap in Linux and launch it. Press the Sniff tab and select Unified sniffing. A small window appears for you to select the network card. Select interface card (eth0) and press OK; the interface will be changed. Start sniffing (press Ctrl+W). The next task is scanning, so press the Hosts tab and click Scan for hosts.
After scanning, click on Hosts list, which will give online hosts on the LAN. Select the victim as Add to Target1 and the gateway as Add to Target 2 as shown in Figure 6.
Press the Mitm tab, and then click Arp poisoning. Press the Plugins tab and then select repoison_arp, in order to send packets continuously.
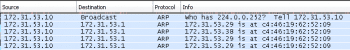
Analyse the network by using Wireshark, which is running on another host. Figure 7 shows the attacker sending the same MAC address to both IP addresses.
Cain and Abel enables you to send spoofed packets to more than one victim. Figure 8 shows the attack on the LAN. Attacker (172.31.53.10) sends a fake ARP reply packet to the gateway (172.31.53.1).
Prevention
One of the ways of prevention is to enter static MAC address entries so that your computer doesnt broadcast ARP requests. Yet, other routers can still be poisoned and you could be in trouble.
You can add a static entry as follows:
>arp -s IP address MAC address |
Detecting ARP spoofing using open source tools
There is no particular algorithm or tool that can tell you that spoofing is being done. ARP spoofing can be avoided by a static entry in the ARP cache but this is not a good enough solution.
Detection in Linux
ARP spoofing can be detected by some free software. In the Linux environment, Arpwatch can detect ARP spoofing. Arpwatch can be started by using the following command:
Service arpwatch restart |
Arpwatch can be bound with the interface eth0, by using the command below:
arpwatch -i eth0 |
By default, Arpwatch sends its log details to /var/log/messages.
To monitor all Arpwatch log messages, use the following command:
# tail -f /var/log/messages jgrep arpwatch# cat /var/log/messages jgrep arpwatch |
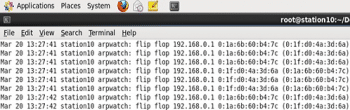
If ARP spoofing happens, then there is a flip flop in the file as shown in Figure 9.
Detection in Windows
In the Windows environment, the free software DecaffeinatID acts as an ARP watcher. It maintains a log file, and gives a special alert whenever it sees the MAC address of the gateway change.