This article deals with iptables, which is a built-in firewall in Linux. The authors explain the commands to configure iptables for various situations, thus making this a must-read for newbies.
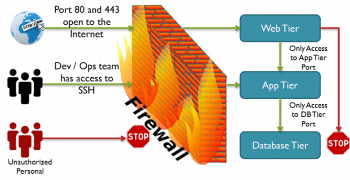
The term firewall generally refers to a barrier that is used to limit the spread of fire. In the computing world, it refers to a software or hardware based network security system, which can be used to control incoming and outgoing network traffic based on a set of rules.
A firewall basically establishes a barrier between the internal network (a group of systems or a single one), which is assumed to be secure and trusted, and the external network (usually the Internet), which is considered neither secure nor trusted. Various operating systems include software based firewalls to protect against the threats from the Internet. A router also consists of firewalls, and a firewall can also perform routing functions.
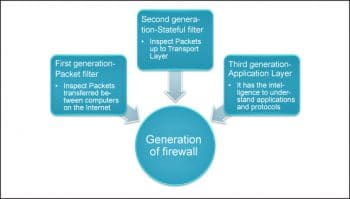
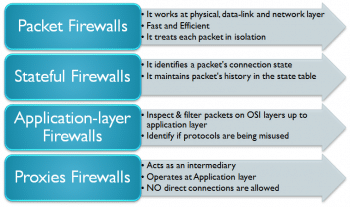
Figure 2 shows the generation of a firewall, while Figure 3 lists the types of firewalls.
iptables
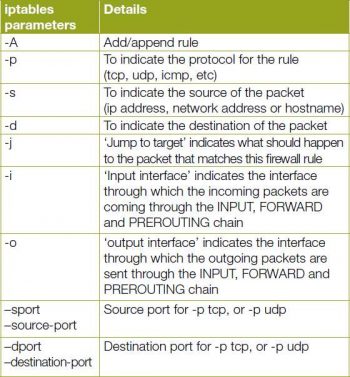
iptables is a built-in firewall in Linux. It is a user based application for configuring the tables provided by the Linux kernel firewall. iptables is the default firewall installed with Red Hat, CentOS, Fedora Linux, etc. Different modules and programs are used for different protocols such as iptables for IPv4, ip6tables for IPv6 and so on. It uses the concept of IP addresses, protocols (tcp, udp, icmp, etc) and ports.
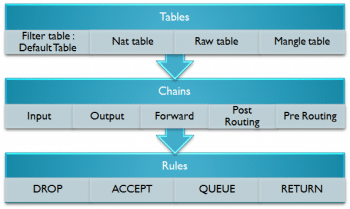
iptables is a command line firewall that uses the concept of chains to handle the network traffic. It places the rules into chains, i.e., INPUT, OUTPUT and FORWARD, which are checked against the network traffic. Decisions are made as to what to do with the packets based on these rules, i.e., whether the packet should be accepted or dropped. These actions are referred to as targets. DROP and ACCEPT are commonly used predefined targets used for dropping and accepting the packets, respectively.
The three predefined chains in the filter table to which rules are added for processing IP packets are:
INPUT: These are packets destined for the host computer.
OUTPUT: These are packets originating from the
host computer.
FORWARD: These packets are neither destined for nor originate from the host computer, but pass through (routed by) the host computer. This chain is used if you are using your computer as a router.
iptable architecture comprises groups of network packets, processing rules into tables and chains for processing the rules. Rules consist of matches to determine which packet the rule will apply to and the targets. They operate at the OSI layer, i.e., the network layer.
For more details, you can visit https://www.youtube.com/watch?v=fQF2vEvqHgU
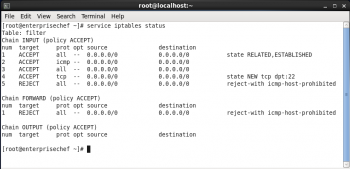
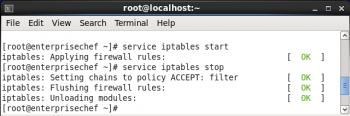
To verify the status of iptables, execute the following command:
service iptables status |
To start and stop the iptables service, use the following command:
service iptables start / stop |
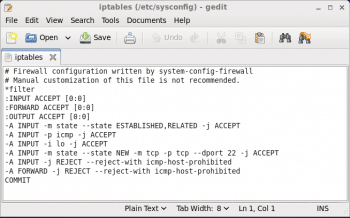
To open the iptables file, execute the following command is:
gedit /etc/sysconfig/iptables |
Syntax for executing iptable command:
iptables -A chain firewall-rule |
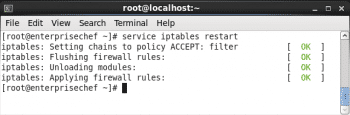
To restart iptables use the following command:
service iptables restart |
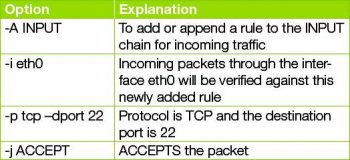
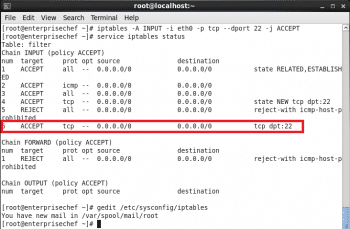
To add rules to the existing iptables to allow ssh, use the following command:
iptables -A INPUT -i eth0 -p tcp --dport 22 -j ACCEPT |
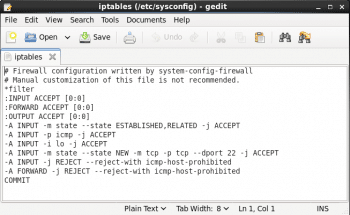
You can verify modified set of rules by seeing /etc/sysconfig/iptables file (as shown in Figure 10).
A few examples to make you comfortable with iptables
1. To allow HTTP traffic, use the following command:
iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT |
2. To allow HTTPS traffic, use the following command:
iptables -A INPUT -s 9.9.9.9 -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT |
3. To allow SSH traffic, use the following command:
iptables -A INPUT -i eth0 -p tcp --dport 22 -m state --state NEW,ESTABLISHED -j ACCEPTiptables -A OUTPUT -o eth0 -p tcp --sport 22 -m state --state ESTABLISHED -j ACCEPT |
4. To allow SNMP traffic, use the following command:
iptables -A INPUT -p udp -m state --state NEW -m udp --dport 161 -j ACCEPT |
5. To change the default chain policies, use these commands:
iptables -P INPUT DROPiptables -P FORWARD DROPiptables -P OUTPUT DROP |
6. To block 9.9.9.9, use:
iptables -A INPUT s 9.9.9.9 -j DROP |
7. To allow a ping from outside to inside/inside to outside, type:
iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPTiptables -A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPTiptables -A OUTPUT -p icmp --icmp-type echo-request -j ACCEPTiptables -A INPUT -p icmp --icmp-type echo-reply -j ACCEPT |
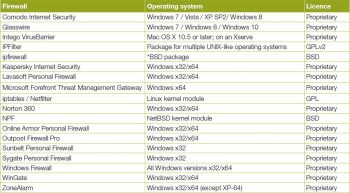
(Reference: http://en.wikipedia.org/wiki/Comparison_of_firewalls)
References
[1] http://en.wikipedia.org/wiki/Firewall_(computing)
[2] http://searchsecurity.techtarget.com/definition/firewall
[3] http://en.wikipedia.org/wiki/Iptables
[4] http://wiki.centos.org/HowTos/Network/IPTables
[5] http://www.thegeekstuff.com/2011/02/iptables-add-rule/
[6] http://geekpeek.net/configure-iptables-centos-6/
[7] https://help.ubuntu.com/community/IptablesHowTo
[8] http://wiki.centos.org/HowTos/Network/IPTables