Blockchains must gear up to protect themselves from quantum computing-based attacks. Post-quantum cryptography and artificial intelligence offer some solutions.
Blockchain is a shared and distributed digital database that holds transactions in an immutable and secure way, without relying on any intermediary. It employs cryptographic mechanisms such as hashing and public-key cryptography to preserve the information unaltered and resistant to unauthorised tampering. Blockchain technology has revolutionised the digital economy by using a secure, decentralised way of recording transactions without an intermediary. However, the rapid progress of quantum computing has the potential to tear down the security of the blockchain.
Traditional blockchain security depends on cryptography such as RSA and ECC (elliptic curve cryptography), which ensures data integrity and authenticity against unauthorised access. Such cryptography is immune to conventional computers but susceptible to quantum algorithms that have the ability to decrypt cryptography by factoring massive prime numbers much quicker than current supercomputers. This implies that once quantum computers come into regular use, they can decrypt the blockchain encryption, revealing transactions, digital coins, and user identities.
Web3, the emerging next-generation web, is constructed on the potential of blockchain by unveiling decentralised applications (dApps) and smart contracts, which offer a trustless and permissionless environment. The security of blockchain networks is based on cryptographic techniques like the Elliptic Curve Digital Signature Algorithm (ECDSA) and Secure Hash Algorithm (SHA), employed to validate transactions and secure users’ resources.
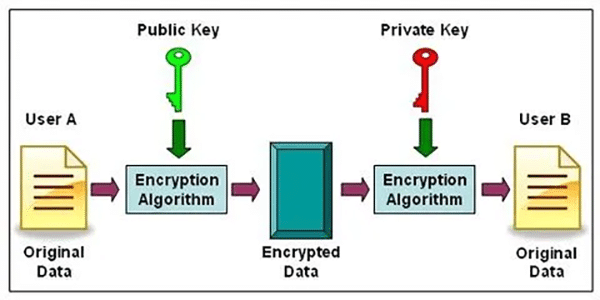
However, the emergence of quantum computers puts these cryptographic foundations at risk. Quantum computing algorithms, e.g., Shor’s and Grover’s, have the capability to disable classical encryption, making blockchain networks vulnerable to a breach. Hence, experts are currently searching for quantum-resistant cryptography solutions withstanding quantum attacks without sacrificing the decentralised aspect of blockchain.
Quantum computing’s challenge to blockchain security
Quantum computing uses the laws of quantum mechanics, like superposition and entanglement, to process information at exponentially greater speeds compared to conventional computers. This computing power, although beneficial in scientific pursuits, threatens blockchain security severely.
Shattering public-key cryptography
The greatest threat is from Shor’s algorithm, which is capable of factoring large numbers and solving discrete logarithms. Both the mathematical underpinnings support RSA (Rivest–Shamir–Adleman) and ECC (elliptic curve cryptography)—two of the prevalent encryption algorithms employed in blockchain networks. The decryption private key generated from a public key can be deciphered by a sufficiently powerful quantum computer, making traditional blockchain security systems obsolete. That is, a quantum-capable attacker can take over digital assets, generate false transactions, and even manipulate blockchain consensus processes.
Collision attacks on hashing
Grover’s algorithm also poses a serious threat. Compared to traditional brute force methods that need 2ⁿ operations to compromise an n-bit hash function, Grover’s algorithm lowers the complexity to around 2^(n/2) operations. What this implies is that cryptographic hash algorithms such as SHA-256, which are deployed in blockchain systems currently, can be susceptible to collision attacks. This means the transaction can be meddled with or cryptographic hashes can be reverse-engineered.
Key recovery attacks and digital wallet vulnerability
Another critical vulnerability is key recovery attacks. Quantum computers may extract private keys from public keys, rendering entire blockchain wallets completely compromised. Since the security of most crypto wallets depends on protection by means of asymmetric cryptographical techniques, this vulnerability can potentially expose hundreds of billions worth of digital content to unauthorised entities. Quantum technology-enabled malicious users can, in theory, steal money, impersonate valid users, and alter transaction histories.
Post-quantum cryptography (PQC) for blockchain security
Quantum computing is no longer something on the horizon — blockchain networks need to get ready for it now. If action isn’t taken, decentralised security may be jeopardised, ruining the future of Web3, DeFi, and blockchain apps.
While the use of hybrid cryptographic methods, which blend both classical and quantum-resistant algorithms, could be a transitional security measure, blockchain networks will have to adopt post-quantum cryptography (PQC) if they are to remain secure and valid. PQC algorithms are used to provide quantum attack-resistance, thereby ensuring the security of transactions, smart contracts, and dApps based on blockchain. Several PQC methods are already available for this purpose.
Lattice-based cryptography
CRYSTALS-Kyber and CRYSTALS-Dilithium are instances of lattice-based cryptographic primitives that rely on the computational intractability of lattice problems, which can withstand attacks from even Shor’s quantum computers. These schemes can potentially be used in blockchain key exchange protocols, digital signatures, and identity verification systems.
from pycryptodome.publickey import NTRU key = NTRU.generate(1024) message = b”Quantum-safe blockchain” ciphertext = key.encrypt(message) decrypted_message = key.decrypt(ciphertext) print(“Original:”, message) print(“Decrypted:”, decrypted_message)
Hash-based cryptography
Blockchain networks also depend on cryptographic hash functions in terms of consensus and immutability. Hash-based signature schemes such as XMSS (eXtended Merkle Signature Scheme) and SPHINCS+ are quantum-resistant and enable the usability of digital signatures deployed in blockchain transactions. Hash-based cryptography is particularly appropriate for transaction authentication as well as ledger protection in blockchain networks. Here is an example of a post-quantum hash-based signature (SPHINCS+) implemented in Python:
from pqcrypto.sign import sphincsplus sk, pk = sphincsplus.generate_keypair() message = b”Secure blockchain transaction” signature = sphincsplus.sign(message, sk) assert sphincsplus.verify(message, signature, pk) print(“Signature verified successfully!”)
Multivariate polynomial cryptography
This relies on factoring hard multivariate quadratic equations and is thus quantum resistant. Techniques such as Rainbow offer secure digital signatures to be used in smart contracts, transaction signing, and decentralised identity management.
Code-based cryptography
Code-based cryptography, such as Classic McEliece, employs error-correcting codes to offer a mathematically established model of security against quantum attackers. This is appropriate for long-term data encryption in blockchain, wallet security, and communication between blockchain nodes.
Super singular isogeny-based cryptography
This is a new cryptographic system that relies on isogeny computation hardness between super singular elliptic curves. While still in the research phase, SIKE (super singular isogeny key encapsulation) provides a lightweight option for low-power blockchain devices, IoT-based blockchain applications, and distributed networks.
The US-based National Institute of Standards and Technology (NIST) is currently standardising PQC algorithms for global use. Blockchain developers are also seeking ways to implement such cryptographic methods in existing and future blockchain platforms.
Integrating AI with quantum-resistant blockchains
AI and PQC integration strengthen blockchain resilience, efficiency, and quantum attack immunity. AI-based techniques improve anomaly detection, cryptographic processing, and scalability.
AI-based anomaly detection
AI models track blockchain transactions to identify anomalies and thwart quantum-driven cyberattacks.
Here is an exampIe of how AI can help identify suspicious blockchain transactions:
from sklearn.ensemble import IsolationForest import numpy as np data = np.random.rand(100, 5) model = IsolationForest (contamination=0.05).fit(data) anomalies = model.predict(data) print(“Anomalous Transactions:”, np.where(anomalies == -1))
AI for blockchain scalability
AI reduces blockchain operation latency by predicting network congestion and expanding transaction capacity. Efficient blockchains are enabled by AI-based consensus models, while PQC implementations offer robust efficiency, and secure and quick transactions.
AI-driven quantum-resistant blockchains can enable secure, efficient, and scalable cryptographic transactions in a decentralised and quantum-immune Web3 society.
The future of quantum-resistant AI blockchains
It is imperative that developers and researchers already engaged in developing blockchain technology actively adopt quantum-resistant methods. Governments and institutions are racing towards standardising and implementing quantum-resistant cryptographic protocols. In the meantime, pre-quantum and post-quantum cryptography can be hybridized as an intermediate step to ensure backward compatibility.
Quantum computing is both an opportunity and challenge for the blockchain ecosystem. By adopting quantum-resistant cryptography and AI-based security upgrades, blockchain networks can maintain their development trajectory and protect the decentralised Web3 future. Integrating these pioneering technologies will ensure secure and reliable blockchain ecosystems in a post-quantum world.