With IoT devices growing at a breakneck pace across the globe, building secure networks is of paramount importance. Open source solutions help with this, as they are backed by a vigilant community.
The Internet of Things (IoT), a network of interconnected devices, has evolved from a futuristic concept to a tangible reality. Its roots trace back to the mid-20th century. But it wasn’t until the late 20th and early 21st centuries that technological advancements, such as microprocessors, wireless communication protocols, and the internet, made IoT a practical reality. Early applications were primarily focused on industrial automation and remote monitoring.
The future of IoT holds immense potential. Open source technologies like AI, machine learning, and edge computing will further enhance IoT capabilities. 5G and beyond will provide the necessary connectivity, while blockchain can strengthen security and privacy.
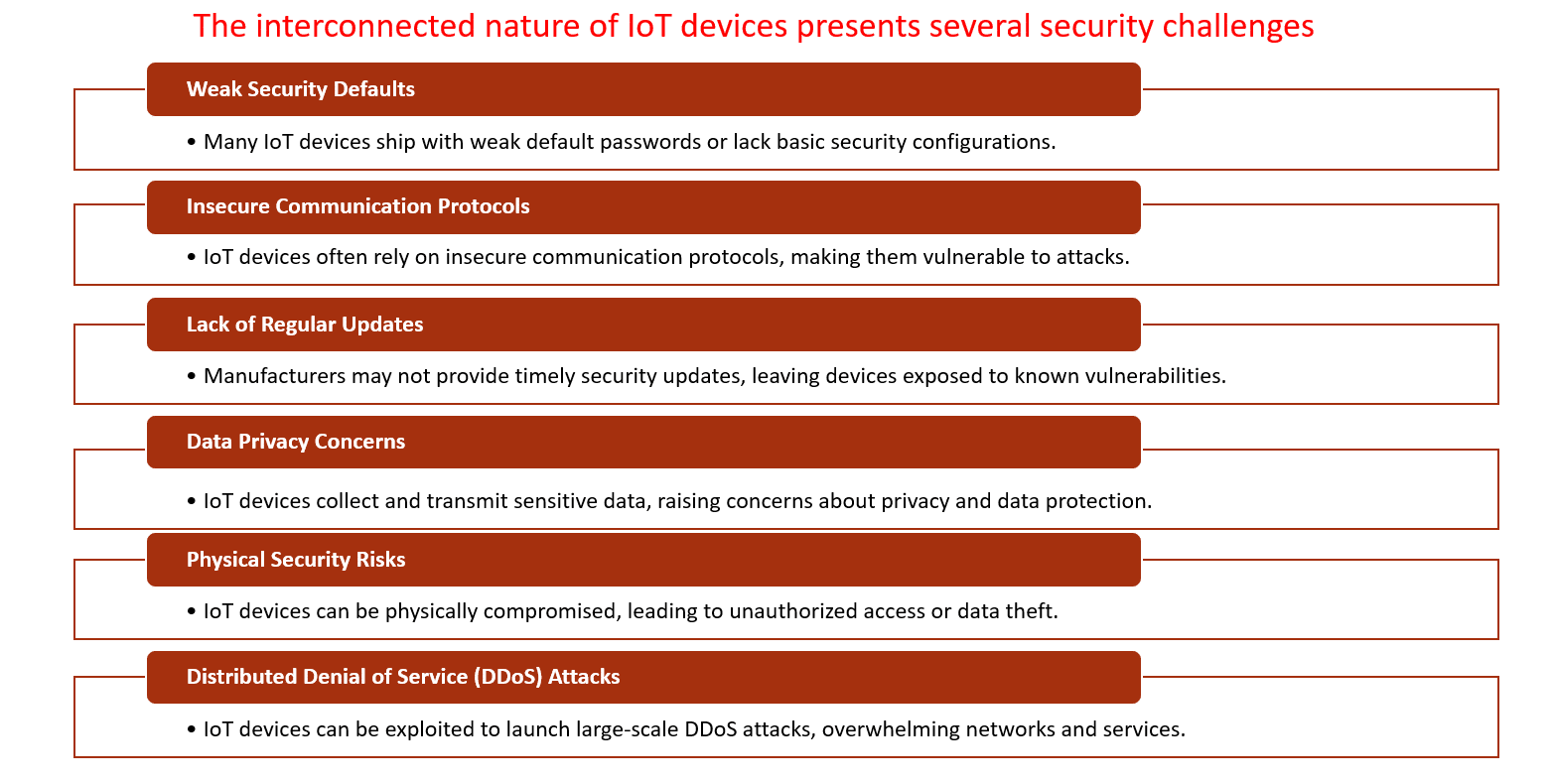
The increasing number of IoT devices also presents significant security challenges, including weak security defaults, insecure communication protocols, and a lack of regular updates. Open source software has emerged as a powerful tool for addressing these challenges. Open source solutions foster innovation, collaboration, and rapid vulnerability discovery and patching by providing transparent, community-driven development.
Understanding IoT vulnerabilities
IoT devices often suffer from common vulnerabilities that can compromise their security. Weak passwords are a frequent culprit, with many devices shipping with default, easily guessable credentials. Insecure protocols, such as outdated or poorly implemented encryption standards, can leave devices exposed to eavesdropping and attacks. Additionally, many IoT devices lack regular security updates, leaving them vulnerable to known exploits. These vulnerabilities, if exploited, can lead to unauthorised access, data breaches, and even physical harm.
In recent years, several high-profile IoT security breaches have underscored the critical importance of robust security measures. One notable example is the Mirai botnet, which exploited vulnerabilities in IoT devices to launch massive DDoS attacks, disrupting internet services worldwide. Another significant incident involved a large-scale smart home device manufacturer breach, exposing sensitive user data. These breaches highlight the far-reaching consequences of IoT security failures, emphasising the need for a proactive approach to safeguarding these interconnected devices.
Open source communities play a vital role in identifying and addressing vulnerabilities in IoT devices. By scrutinising code, conducting security audits, and sharing findings, these communities help uncover weaknesses that might go unnoticed. When vulnerabilities are discovered, open source developers collaborate to develop and deploy patches, ensuring that devices remain secure. Additionally, open source communities foster a culture of transparency and accountability, encouraging vendors to prioritise security and release timely updates.
Open source tools and frameworks for IoT security
A robust arsenal of open source tools and frameworks is available to bolster IoT security.
Cryptographic libraries
Cryptographic libraries like OpenSSL and Botan provide strong encryption algorithms and secure communication protocols. Let’s review a couple of cryptography libraries as an example.
Botan: This high-performance, cross-platform cryptography library offers many cryptographic algorithms, protocols, and formats. Its versatility and efficiency make it a popular choice for securing IoT devices. Botan supports modern cryptographic standards, including TLS, X.509 certificates, and post-quantum cryptography. By incorporating Botan into their projects, developers can enhance the security of their IoT applications and protect sensitive data.
OpenSSL: This is a powerful open source cryptographic library that provides various security functionalities, including encryption, decryption, digital signatures, and secure communication protocols like TLS/SSL. By incorporating OpenSSL into their applications, developers can ensure the confidentiality, integrity, and authenticity of data transmitted over networks. This makes it an indispensable tool for securing IoT devices and their communications
Secure bootloaders
Secure bootloaders are essential components of IoT device security. They verify the integrity of the device’s firmware before booting, ensuring that only trusted software is executed. By preventing unauthorised modifications, secure bootloaders help protect devices from malicious attacks.
U-Boot: A widely used open source bootloader, U-Boot provides flexibility and customisation options. It supports a variety of architectures and boot modes, making it suitable for diverse IoT devices.
Coreboot: A minimal BIOS replacement, Coreboot offers a secure and efficient boot process. It can be customised to meet specific security requirements and can be used to build highly secure IoT devices.
Secure operating systems
A secure operating system is the bedrock of IoT device security. It provides a controlled environment for applications to execute, minimising the risk of attacks and unauthorised access.
RIOT-OS: Designed for resource constrained devices, RIOT-OS offers a small footprint, low power consumption, and robust security features. It is ideal for IoT devices that require minimal hardware resources.
Zephyr: A scalable real-time operating system, Zephyr provides a flexible and secure platform for building IoT applications. It supports various hardware architectures and offers features like secure boot, memory protection, and cryptographic acceleration.
Security testing tools
Security testing tools play a crucial role in identifying and mitigating vulnerabilities in IoT devices. By subjecting devices to rigorous testing, developers can uncover weaknesses and take corrective actions.
The OWASP IoT Security Testing Guide: This comprehensive guide provides a structured approach to testing IoT devices, covering network security, device security, and data privacy.
IoT Inspector: A powerful tool for analysing IoT devices, IoT Inspector can identify vulnerabilities, assess risks, and provide actionable recommendations. It can scan devices for weak passwords, insecure protocols, and other security flaws.
By utilising these tools, developers can strengthen the security posture of their IoT devices and protect against potential threats.
Best practices for securing IoT devices
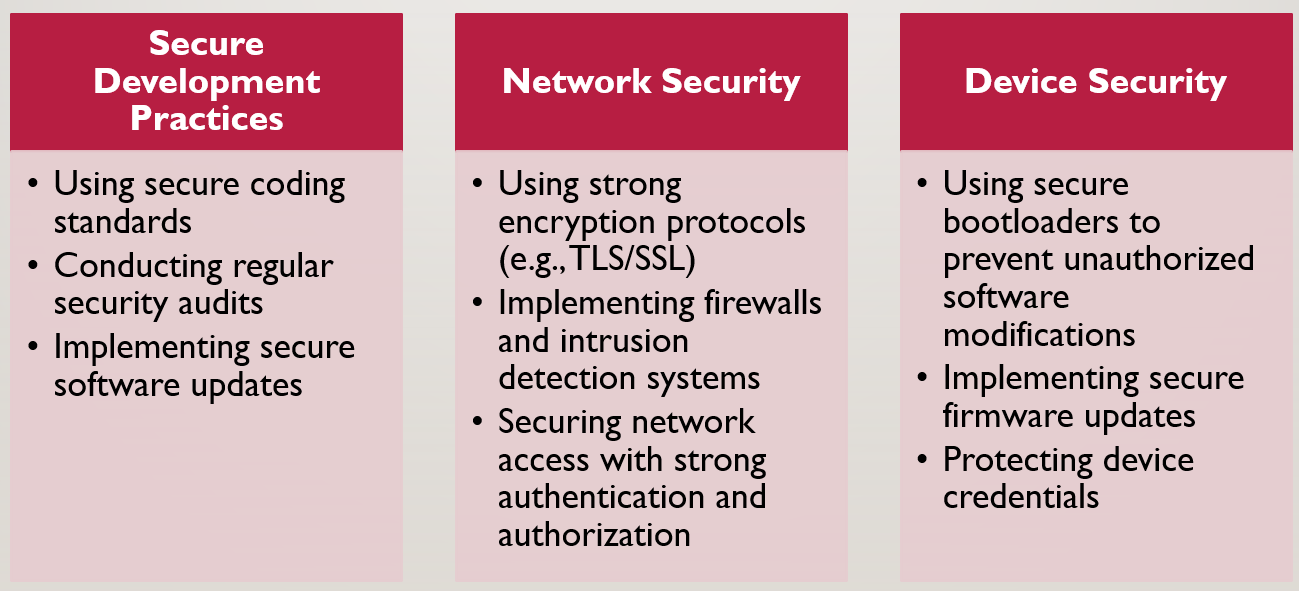
Securing IoT devices is paramount in today’s interconnected world. Several best practices should be followed to ensure these devices’ safety and privacy. Secure development practices, such as employing secure coding standards and conducting regular security audits, are crucial. Next, network security measures, including strong encryption protocols, firewalls, and intrusion detection systems, are essential to protect data transmission and prevent unauthorised access. Additionally, device-level security measures, like secure bootloaders and firmware update mechanisms, can significantly enhance the overall security posture. Lastly, educating users about security best practices, such as avoiding weak passwords and recognising phishing attacks, is crucial for maintaining a strong security posture. By adhering to these best practices, organisations can mitigate risks, protect sensitive data, and safeguard their IoT deployments.
Future trends in IoT securityBala Kalavala
The future of IoT security is evolving rapidly, driven by technological advancements and emerging threats. Artificial intelligence and machine learning will be crucial in detecting and responding to security threats in real time. Zero-trust security models will become increasingly important as they assume no user or device is inherently trustworthy. Quantum-resistant cryptography will be essential to protect against future quantum computing attacks. As IoT expands, staying ahead of emerging threats and adopting proactive security measures is imperative.
To sum up, the Internet of Things has the potential to revolutionise industries and improve our daily lives. However, there are significant security challenges. By understanding these challenges and implementing robust security measures, we can mitigate risks and ensure safe and reliable operation of IoT devices.
Open source software plays a vital role in addressing IoT security, and developers can build more secure and resilient IoT systems by leveraging open source solutions.
As the IoT landscape evolves, staying informed about the latest security threats and emerging technologies is crucial. By adopting a security-first approach, we can harness the full potential of IoT while safeguarding our digital future.
Disclaimer: This article expresses the views of the author and not of the organisation he works in.