eBPF, a game-changing technology that extends the capabilities of the Linux kernel, offers significant advantages for Kubernetes networking. It also greatly improves Kubernetes observability by capturing detailed telemetry data directly from the kernel. Read on to find out how its integration with Kubernetes has immense benefits.
eBPF (extended Berkeley Packet Filter) is a groundbreaking technology initially designed to enhance network packet filtering in the Linux kernel. Traditionally, BPF (Berkeley Packet Filter) could only be attached to sockets, with its first use case being network packet filtering for tools like tcpdump. In this case, BPF programs would filter packets by attaching to a raw AF_PACKET socket and displaying the filtered data.
However, eBPF has significantly evolved beyond its original scope. It now supports attaching to various kernel objects, extending its applicability far beyond socket filtering. Today, eBPF can hook into Kprobes, tracepoints, network schedulers (qdiscs) for classification and actions, and XDP (eXpress Data Path) for faster packet processing. These additions, along with newer features like in-kernel helper functions and shared data structures (maps) that allow communication with user space, have transformed eBPF into a powerful tool for networking, observability, and security.
With these enhanced capabilities, eBPF offers precise control over system behaviour and observability in real time, making it an ideal technology to integrate with Kubernetes, which manages complex, distributed cloud-native environments.
Enhancing Kubernetes networking with eBPF
Networking in Kubernetes has traditionally been managed by tools like CNI (container network interface) plugins, such as Calico, Flannel, and Weave, which define how network policies and traffic routing are handled. However, as Kubernetes deployments scale, traditional networking approaches can become inefficient or lack the deep granularity needed for performance tuning and security.
eBPF offers significant advantages for Kubernetes networking, allowing for fine-grained control and efficient packet processing without the overhead of traditional kernel-space to user-space context switches.
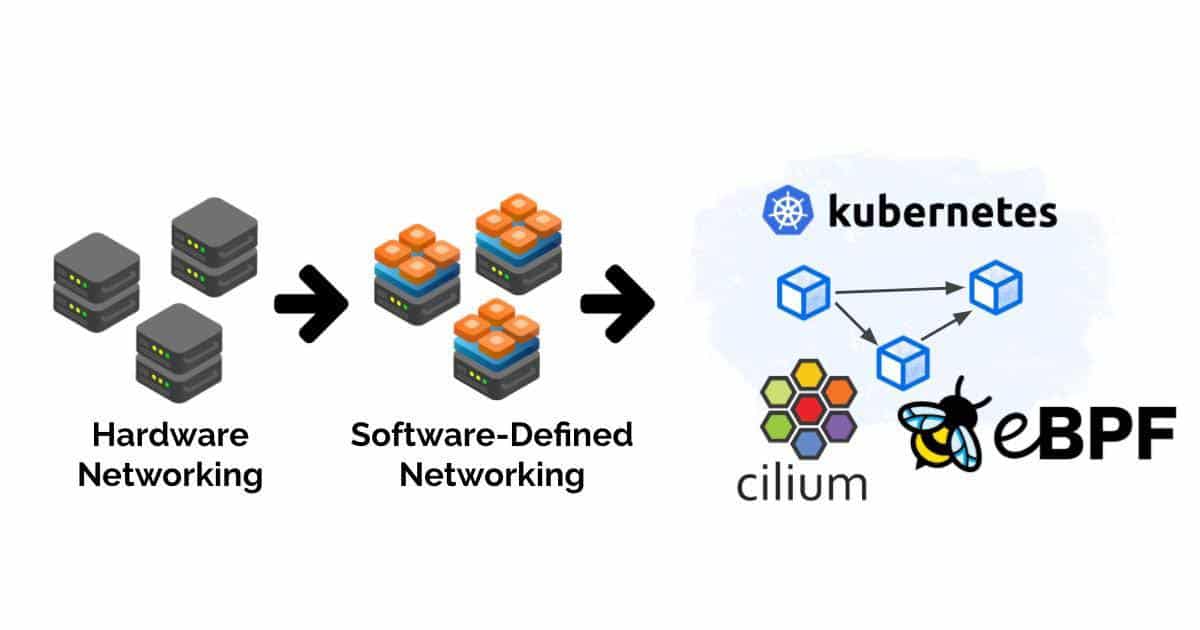
Figure 1 illustrates the evolution of networking, from hardware-based to software-defined networking (SDN), and how eBPF integrates with Kubernetes to enable advanced networking capabilities with tools like Cilium.
Efficient packet filtering and processing
eBPF enables high-performance packet filtering and processing directly in the kernel, bypassing the need for expensive user-space operations. This allows Kubernetes clusters to handle networking operations more efficiently, reducing latency and improving throughput. By filtering packets early in the pipeline, eBPF also reduces the load on the kernel, which is especially useful in large scale Kubernetes deployments.
For example, Cilium, a popular eBPF-based networking plugin for Kubernetes, replaces the traditional IP tables-based packet filtering and routing mechanism. With Cilium, you can enforce network policies and load balancing directly at the kernel level using eBPF, providing faster and more scalable network performance.
Advanced load balancing and service mesh integration
eBPF supports programmable load balancing within Kubernetes, offering a more flexible alternative to traditional approaches like IPVS or IP tables-based load balancers. eBPF’s load balancing can handle high traffic volumes while intelligently routing packets with minimal overhead, improving resource efficiency.
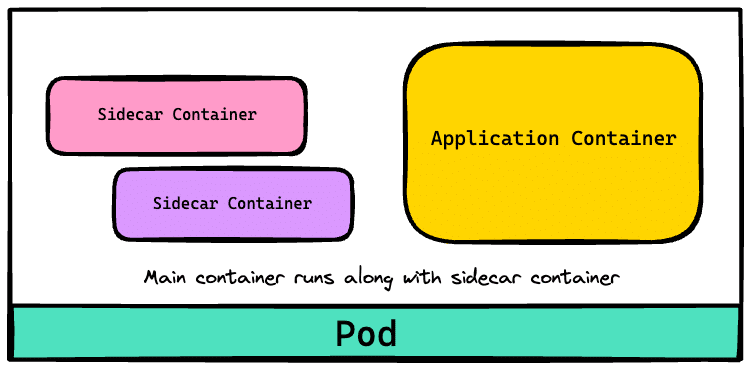
Figure 2 shows the typical sidecar container setup within a Kubernetes pod, illustrating how service meshes deploy sidecar proxies to handle network traffic for application containers.
Additionally, eBPF can complement service meshes such as Istio or Linkerd, providing enhanced observability and reducing the performance impact often associated with sidecar proxies. By using eBPF-based dataplanes, service meshes can intercept and monitor traffic more efficiently, resulting in lower latency and reduced CPU utilisation.
Network security and isolation
In Kubernetes, ensuring security across clusters and pods is paramount. eBPF enhances security through dynamic network policy enforcement. Instead of relying on static rules in the user space, eBPF can enforce network policies directly in the kernel, allowing real-time adjustments to traffic patterns, blocking unauthorised connections, and improving response time to security threats.
Figure 3 reinforces how eBPF integrates into the Kubernetes networking stack, emphasising its role in security and policy enforcement through Cilium.
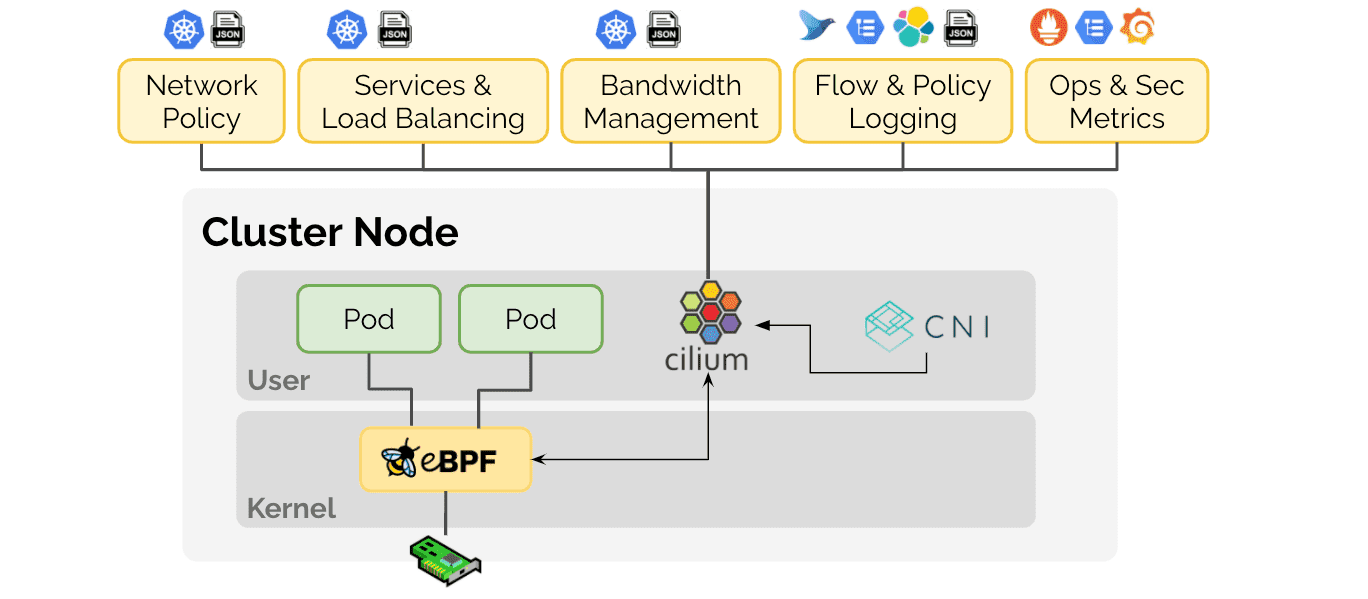
Cilium, again, uses eBPF to implement fine-grained network policies and even provides identity-based security for workloads based on Kubernetes labels. This dynamic and scalable approach to networking security is essential in distributed environments where workloads are constantly changing.
Observability with eBPF in Kubernetes
Observability in Kubernetes environments is crucial for monitoring performance, troubleshooting issues, and ensuring efficient resource utilisation. Traditional observability tools rely on kernel-level metrics and logs, which often provide limited visibility into the system’s real-time state. eBPF dramatically improves observability by capturing detailed telemetry data directly from the kernel, giving operators deep insights into the behaviour of applications and system components.
Real-time monitoring of system events
eBPF enables real-time monitoring of system calls, network packets, and process activities. By attaching eBPF programs to various kernel hooks, you can capture detailed metrics about CPU usage, disk I/O, memory usage, and network traffic in a non-intrusive way. These metrics help identify performance bottlenecks, diagnose latency issues, and troubleshoot errors in Kubernetes clusters.
In addition to traditional monitoring tools, eBPF can be integrated with modern observability platforms like Prometheus and Grafana to provide visualisations of detailed, low-level metrics captured from the kernel. This granular level of observability is essential for performance tuning in complex, multi-node Kubernetes environments.
Application tracing and debugging
eBPF allows developers to trace and debug applications in Kubernetes clusters with unprecedented precision. With eBPF-based tracing, you can follow the entire lifecycle of a request as it travels through various services and containers within the Kubernetes cluster. This allows for detailed analysis of where latency is introduced or where resource bottlenecks occur.
BPFTrace, a high-level tracing tool built on eBPF, provides a simple way to write scripts that capture system events and metrics, such as system calls, network activity, and process events. By running BPFTrace in Kubernetes clusters, developers can debug issues related to resource contention, network slowdowns, or performance degradation at the kernel level, all without modifying the underlying application code.
Security auditing and intrusion detection
With eBPF, you can also perform real-time security auditing by capturing data about suspicious activities in the system, such as unauthorised access attempts or unusual system behaviour. This provides a robust method for detecting potential security breaches, even within highly dynamic Kubernetes environments.
By integrating eBPF with security tools like Falco, an open source project for real-time threat detection, Kubernetes administrators can continuously monitor system events for anomalies and malicious behaviour. eBPF provides deep visibility into network traffic and system operations, allowing for quicker detection and response to security incidents.
Practical implementation and use cases
The integration of eBPF into Kubernetes can be implemented using various tools and frameworks, such as Cilium for networking and BPFTrace for observability. Given below are some practical steps and real-world use cases showcasing the power of eBPF in Kubernetes.
Setting up eBPF with Cilium for networking: To enhance Kubernetes networking with eBPF, you can install and configure Cilium as a CNI plugin in your cluster. Cilium leverages eBPF to provide high-performance networking, advanced security, and network policy enforcement.
Here’s a simplified guide on how to set up Cilium.
Install Cilium in your Kubernetes cluster:
helm repo add cilium https://helm.cilium.io/ helm install cilium cilium/cilium --version 1.11.0 --namespace kube-system
Enable eBPF-based load balancing and network policies:
helm upgrade cilium cilium/cilium --namespace kube-system --set global.nodePort.enabled=true --set global.ebpf.enabled=true
Apply network policies to secure communication between pods:
kubectl apply -f my-network-policy.yaml
This configuration allows for scalable, secure networking with eBPF-based load balancing and traffic filtering.
Observability with BPFTrace: For deeper observability, you can deploy BPFTrace in your Kubernetes environment to capture system events and trace application behaviour.
Install BPFTrace in your nodes:
sudo apt-get install bpftrace
Write a simple trace script to monitor system call:
pftrace -e ‘tracepoint:syscalls:sys_enter_execve { printf(“Executing %s\n”, str(args->filename)); }’
The integration of eBPF with Kubernetes brings advanced networking capabilities, security, and deep observability to containerised environments. eBPF enables fine-grained control over network traffic, improves performance through efficient packet processing, and provides real-time insights into system behaviour. By leveraging tools like Cilium for networking and BPFTrace for observability, Kubernetes administrators and developers can unlock powerful new ways to monitor, secure, and optimise their clusters.
As the cloud-native landscape continues to evolve, the role of eBPF in Kubernetes is poised to grow, making it an essential tool for modern infrastructure management. Whether you’re looking to enhance performance, secure your network, or gain deeper insights into system behaviour, eBPF’s integration with Kubernetes offers unparalleled benefits.