Is cloud security on your mind? Here are some insights into overcoming the complexity of securing cloud workloads by utilising advanced AWS cloud workload protection tools and methodologies, such as micro segmentation and zero trust network access (ZTNA).
Security of cloud computing has emerged as an indispensable cornerstone for businesses migrating their operations online. Cloud workloads, encompassing applications and services running in the cloud, are essential assets hosting sensitive information, business secrets, and intellectual property. Their protection is a matter of maintaining the integrity, confidentiality, and availability of workloads in the cloud, positioning cloud workload security as a critical element in an organisation’s cybersecurity strategy. Given the diversity of these workloads, from databases and containers to virtual and physical servers navigating through cloud environments, securing them against cyberattacks ensures organisations can leverage the cloud’s benefits without compromising on security.
As the cloud landscape continues to evolve, so do the threats and complexities associated with securing cloud workloads. It’s essential for organisations to adopt a strategy that includes continuous threat monitoring, workload segmentation for simplified traffic inspection, and security solutions that are agile and decoupled from the cloud platform itself.
A cloud workload encompasses all the computing resources and tasks necessary to run applications or services within a cloud computing environment. This broad definition includes a variety of deployment models, with Software-as-a-Service (SaaS) being the most prevalent, followed by Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS). The rapid adoption of these models is evident in the significant growth of cloud workloads.
Cloud workloads vary widely and can be classified based on several criteria.
Cloud deployment model: Determines how the cloud services are structured and delivered.
Cloud native technology: Involves technologies that are built specifically for cloud environments, enhancing scalability and performance.
Usage patterns: Refers to how the services are used, which can vary from continuous operations to intermittent use.
Resource requirements: Involves the computational power, storage, and network resources needed.
SeSecurity needs of cloud workloadscurity needs of cloud workloads
Cloud workload security involves protecting the applications, services, and capabilities that operate on cloud resources. Effective security measures are crucial not only for safeguarding cloud-based applications and data but also for maintaining the overall integrity and availability of services.
Given that cloud workloads can be accessed and managed remotely over the internet, it is essential to implement robust security frameworks that can handle the dynamic and distributed nature of cloud resources. Understanding the diversity of workloads and seamlessly integrating security measures with existing systems are key to effective cloud workload protection.
By understanding the specific needs and security requirements of different cloud workloads, organisations can better prepare and implement effective protection strategies.
Key threats to cloud workloads
Cloud workloads face a myriad of threats that can compromise their security, integrity, and availability. Understanding these threats is crucial for implementing effective security measures.
Data breaches and ransomware: These are critical threats where sensitive information is accessed or encrypted without permission, often leading to significant financial and reputational damage.
DDoS and phishing attacks: These attacks disrupt service availability or trick users into revealing sensitive information, severely impacting cloud operations.
Cyberattacks: These include ransomware, supply chain attacks, insider threats, and cryptominers, each presenting unique challenges to cloud security.
Expansion of attack surfaces
The adoption of microservices and the increasing complexity of cloud architectures can significantly expand the attack surface, making cloud workloads vulnerable to unauthorised access and attacks.
Unmanaged attack surface: Increased public exposure of microservices leads to higher risks of cyberattacks.
Misconfiguration: As cloud services evolve, the risk of misconfiguration grows, often due to varying default settings across multiple providers.
Human factor and insider threats
Human error and insider threats remain significant concerns, with potential for severe security breaches stemming from within the organisation.
Human error: Predicted to be the cause of 99% of cloud security failures.
Insider threats: These threats can arise from anyone within the organisation who has access to sensitive data and systems.
Advanced persistent threats and zero-day exploits
Sophisticated cyber threats such as APTs and zero-day exploits can bypass conventional security measures, requiring advanced detection and response strategies.
Advanced persistent threats (APTs): These are complex, long-duration attacks aimed at stealing sensitive data.
Zero-day exploits: These exploits take advantage of unpatched vulnerabilities, posing a significant risk even to well-secured cloud environments.
Challenges in identity and access management
Proper management of identities and access controls is foundational to securing cloud workloads, yet it remains a daunting task for many organisations.
Identity and access management (IAM): Critical for defining and managing roles and permissions, yet complex to administer across large enterprises.
Unauthorised access and insecure APIs: These can provide attackers easy paths to infiltrate cloud workloads if not properly secured.
Compliance and visibility issues: Ensuring compliance with regulatory standards and maintaining visibility into cloud operations are pivotal for security but are often challenging due to the cloud’s complex nature.
Cloud compliance: Organisations must continuously meet standards like PCI DSS and HIPAA, which protect sensitive data.
Lack of visibility: Traditional tools may not offer sufficient visibility in cloud environments, hindering effective monitoring and protection.
Misconfiguration and external data sharing risks
Misconfiguration of cloud settings is a leading cause of security breaches, and external data sharing introduces additional risks.
Misconfiguration: Commonly leads to data breaches, emphasising the need for robust cloud security posture management.
External sharing of data: While facilitating collaboration, it also poses risks if access controls are not properly managed.
Best practices for securing cloud workloads
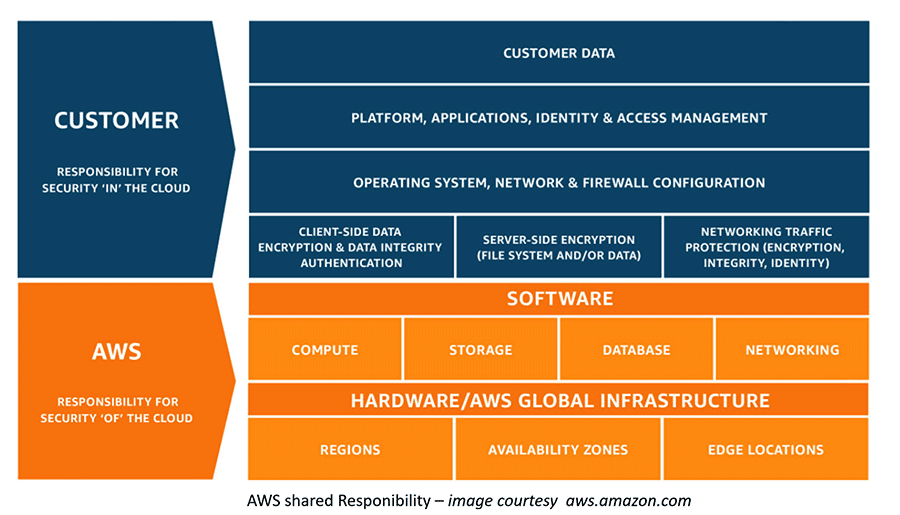
Understanding your shared responsibility
Cloud workload security is a shared responsibility between the organisation, its customer, and the cloud provider. It’s essential to understand that while the provider secures the infrastructure, the organisation is responsible for securing its data and its access. This model requires businesses to actively manage and secure several aspects of their cloud environment.
To safeguard their cloud workloads effectively, organisations must focus on the following areas.
Cloud management console and API keys: Ensure that all your cloud management tools and API SSH keys are secured against unauthorised access.
Virtual infrastructure and DevOps tools: Protect your virtual infrastructure and DevOps admin consoles and tools. This includes securing your DevOps pipeline code and SaaS applications admin accounts.
Cloud entitlements and permissions: Manage cloud entitlements carefully to prevent excessive permissions that could lead to security breaches.
Implementing multilayer security measures
Implementing multilayer security measures is crucial for robust cloud workload protection.
Perimeter security: Deploy firewalls at the network perimeter and restrict incoming traffic to applications to secure the perimeter.
Segmentation: Segment workloads between different virtual networks to control traffic flow and reduce the risk of lateral movement by attackers.
Identity and access management (IAM): Use IAM to implement role-based, fine-grained access control to your cloud resources.
Cloud security posture management (CSPM): Incorporate CSPM solutions to monitor for misconfigurations and ensure compliance with your security policies.
Advanced security technologies and practices
To further enhance cloud workload security, consider the following technologies and practices.
Encryption: Encrypt your data both in transit and at rest to protect sensitive information from unauthorised access.
Advanced threat detection: Utilise premium tier native CSPM solutions for advanced threat detection and response capabilities.
Zero trust approach: Implement a zero trust approach by assuming no trust between services and segmenting communication accordingly.
Cybersecurity training: Conduct comprehensive security training programmes for your employees to mitigate risks associated with human error.
Continuous monitoring and compliance
Maintaining visibility and compliance is vital for cloud workload security.
Log management: Enable logging capabilities within your cloud infrastructure to monitor activities and detect potential security incidents.
Penetration testing: Regularly conduct penetration tests to simulate real-world attacks and evaluate the effectiveness of your security measures.
Compliance: Ensure that your cloud workloads comply with relevant laws and regulations to avoid legal and financial penalties.
Implementing these best practices will help you secure your cloud workloads effectively, ensuring the safety and integrity of your data and applications in the cloud environment.
A cloud workload protection platform (CWPP) offers comprehensive protection for workloads of all types across multiple providers, ensuring unified cloud workload security.
The primary benefits of utilising cloud workload protection (CWP) include enhanced visibility, robust protection, and frictionless security, which are crucial for maintaining the integrity and efficiency of cloud operations. Essential requirements for an effective CWPP include runtime protection, comprehensive visibility, and a balance between simplicity and performance.
Leveraging AWS tools for enhanced security
To address security challenges, AWS offers specific tools and services designed to enhance cloud workload protection. When selecting the right AWS CWP tools, it’s essential to understand that cloud workload protection is a continuous process aimed at monitoring and eliminating threats from cloud workloads and containers.
These tools provide advanced security features that allow for detailed monitoring, automated threat detection, and proactive risk management, ensuring that cloud workloads are protected against both internal and external threats.
AWS tools are designed to complement native cloud security capabilities and provide advanced protection features, such as intrusion prevention, vulnerability management, and endpoint detection and response. By integrating these AWS-specific tools into your security strategy, you can achieve a more robust defence against the evolving landscape of cyber threats.
AWS GuardDuty, for instance, is a managed threat detection service that offers continuous monitoring and intelligent threat detection tailored for AWS accounts and workloads. This tool is instrumental in identifying unexpected and potentially unauthorised or malicious activity within your AWS environment.
Data breaches and ransomware: AWS encryption services (AWS KMS, AWS CloudHSM) enable data encryption at rest and in transit, protecting sensitive data from unauthorised access.
AWS Security Hub and Amazon GuardDuty help detect and respond to potential data breaches and malicious activities.
DDoS and phishing attacks: AWS Shield provides comprehensive DDoS protection against infrastructure layer attacks. AWS Web Application Firewall (WAF) helps mitigate web application layer DDoS attacks and protects against phishing attempts.
Cyberattacks (ransomware, supply chain attacks, insider threats, cryptominers): AWS Security Hub and Amazon Inspector help identify and remediate vulnerabilities that could be exploited by various cyberattacks. AWS CloudTrail and AWS Config enable monitoring and auditing of activities within your AWS environment, helping detect potential insider threats. AWS Artifact provides on-demand access to AWS compliance reports, enabling better visibility into the security posture of AWS services.
Expansion of attack surfaces: AWS Security Hub and AWS Config Rules help identify and correct misconfigurations that could lead to an expanded attack surface. AWS Firewall Manager simplifies the management and enforcement of security policies across multiple accounts and resources.
Human factor and insider threats: AWS Identity and Access Management (IAM) allows granular control over access to AWS resources, minimising the risk of unauthorised access. AWS CloudTrail and AWS Config enable auditing and monitoring of user activities, helping detect potential insider threats.
Advanced persistent threats (APTs) and zero-day exploits: AWS Security Hub and Amazon GuardDuty leverage advanced threat intelligence to detect and respond to sophisticated threats, including APTs and zero-day exploits. AWS Firewall Manager and AWS Network Firewall provide advanced network security controls to protect against emerging threats.
Identity and access management (IAM) challenges: AWS IAM enables centralised management of identities and access controls, simplifying administration across multiple accounts and services. AWS Single Sign-On (AWS SSO) and AWS IAM Identity Center facilitate secure access and permission management for cloud workloads.
Compliance and visibility issues: AWS Config Rules help assess and monitor resource configurations for compliance with various standards, such as PCI DSS and HIPAA. AWS CloudTrail and Amazon CloudWatch provide comprehensive logging and monitoring capabilities, enhancing visibility into cloud operations.
Misconfiguration and external data sharing risks: AWS Config Rules and AWS Security Hub help identify and correct misconfigurations that could lead to security breaches. AWS Resource Access Manager enables secure cross-account resource sharing, minimising the risks associated with external data sharing.
AWS continuously enhances its security services and provides best practice guidance to help organisations effectively secure their cloud workloads against evolving threats and vulnerabilities. By leveraging the comprehensive security capabilities of AWS, organisations can achieve robust protection, visibility, and compliance for their cloud-based applications and data.
We’ve explored the critical landscape of cloud workload security, emphasising its importance in the digital age. The adoption of AWS cloud workload protection tools stands out to be effective against cyber threats, ensuring security and compliance. Integrating these tools into their security framework enables organisations to implement a more resilient and secure cloud infrastructure.










































































