DevSecOps incorporates security practices into DevOps to help ensure secure software development and delivery. The use of open source tools and a structured approach are crucial in achieving this objective.
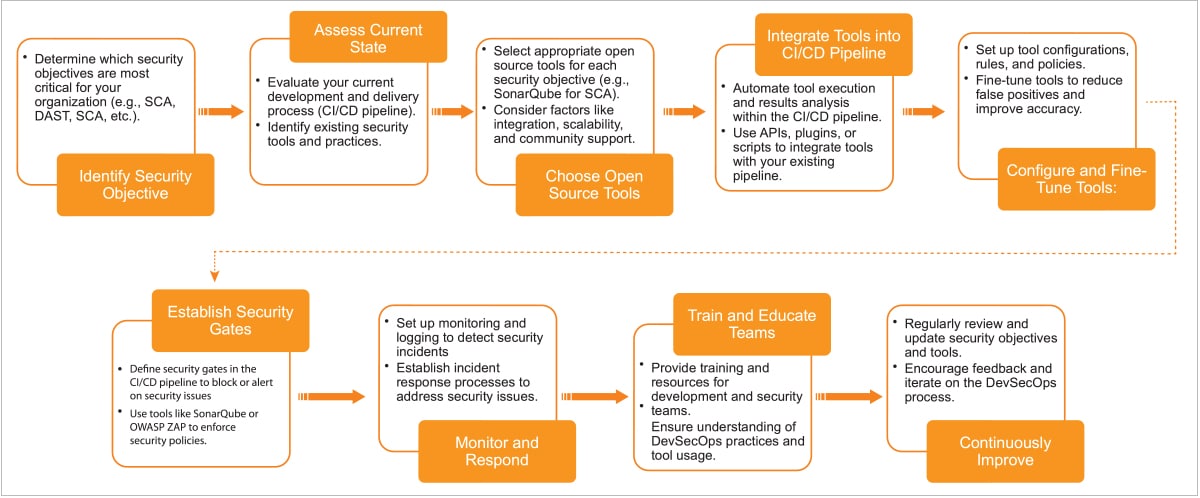
Businesses can start their DevSecOps journey by carefully identifying security objectives and assessing the current state of security. Then, they must select the best open source tools for their needs and integrate these into the CI/CD pipeline, configuring and fine-tuning them to their preferences. Establishing security gates is essential, as is monitoring and responding to security incidents. By training teams and continuously improving the process, they can stay ahead of the curve. But they must always remember to prioritise security, automate everything possible, collaborate openly, use infrastructure as code, implement security as code, manage vulnerabilities effectively, maintain compliance, monitor regularly, and continuously improve. With these guiding principles in mind, they will be well on their way to DevSecOps success.
Figure 1 and Table 1 list various security objectives in software development and delivery, along with the open source tools that can be used to achieve them.

Table 1: Open source tools that can be used for automating CI/CD in DevSecOps
| Category | Objective | Open source tools |
| Static code analysis (SCA) | Identify vulnerabilities and weaknesses in code | SonarQube, CodeCoverage, CodeHeat |
| Dynamic application security testing (DAST) | Detect runtime vulnerabilities and weaknesses | OWASP ZAP, Burp Suite, BeEF |
| Software composition analysis (SCA) | Identify open source component vulnerabilities | Black Duck Hub, Sonatype Nexus, Dependency-Track |
| Infrastructure as code (IAC) | Secure cloud and infrastructure configurations | Terraform, AWS CloudFormation, Azure ARM |
| Containerisation | Secure container images and runtime | Docker, Kubernetes, Anchore |
| Identity and access management (IAM) | Manage access and authentication | LDAP, Active Directory, Okta |
| Monitoring and logging | Detect and respond to security incidents | ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, Grafana |
| Compliance and governance | Ensure regulatory compliance and security policies | OpenVAS, Nessus, Compliance Scanner |
By implementing an automated CI/CD pipeline with security integration, organisations can ensure that software is always secure. It’s important to note that this is not an exhaustive list of security tools, and there may be some overlap between security objectives. The reference architecture in Figure 1 is meant to provide a starting point for implementing DevSecOps practices with open source tools. With DevSecOps, organisations can ensure that software is always secure, allowing them to focus on their core business.
Best practices for enabling DevSecOps with open source tools
Implementing DevSecOps with open source tools can be complex, but following a few best practices can make the process easier and more effective.
- Automate everything: Automate tool execution, results analysis, and security gates in the CI/CD pipeline to shorten development cycles and reduce errors caused by manual processes.
- Integrate with existing tools: Integrate open source tools with existing development and security tools to improve collaboration and streamline workflows.
- Use APIs and plugins: Utilise APIs and plugins to integrate tools with the CI/CD pipeline and automate the entire software development process.
- Configure and fine-tune tools: Set up tool configurations, rules, and policies to reduce false positives and improve accuracy, ensuring maximum effectiveness.
- Establish security gates: Define security gates in the CI/CD pipeline to block or alert on security issues and prevent security breaches.
- Monitor and respond: Set up monitoring and logging to detect security incidents and establish incident response processes, ensuring that potential threats are addressed quickly and effectively.
- Train and educate teams: Provide training and resources for development and security teams on DevSecOps practices and tool usage, ensuring that everyone is on the same page and working towards the same goals.
- Continuously improve: Regularly review and update security objectives and tools to address evolving threats and stay ahead of emerging risks.
- Use open standards: Use open standards like OWASP and NIST to ensure consistency and interoperability, promoting transparency and collaboration across the team.
- Collaborate with communities: Engage with open source communities to stay updated on tool developments and best practices, and leverage collective knowledge to enhance your organisation’s security practices.
- Implement security as code: Store security configurations and policies as code to version and manage them, ensuring that everything is consistent and properly documented.
- Use infrastructure as code: Manage infrastructure configurations through code to ensure consistency and security, making it easier to manage complex systems and reduce errors.
- Prioritise vulnerability management: Focus on identifying and remediating vulnerabilities early in the development cycle, minimising the risk of security breaches.
- Use compliance scanning: Integrate compliance scanning tools to ensure adherence to regulatory requirements.
- Embed security in culture: Foster a security-first culture across development, security, and operations teams, making security a top priority throughout the development process.
Organisations must regularly review and update security objectives and tools to address evolving threats. Figure 2 illustrates a few principles that should guide your DevSecOps implementation journey. By embracing these principles, your organisation can ensure a robust and effective implementation of DevSecOps that integrates security at every stage of the software development and delivery process. This approach not only minimises risks but also enhances the overall quality and reliability of the product.
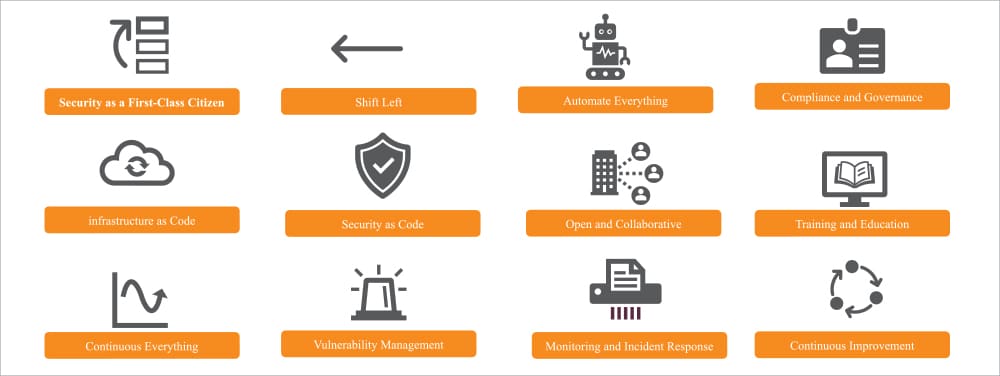
Things to consider when implementing DevSecOps
To ensure successful execution of DevSecOps, there are a few things you should keep in mind.
- Integration: It’s essential to ensure that the open source tools you choose can be seamlessly integrated with your existing development tools and workflows. This will help to minimise disruptions and improve productivity.
- Scalability: As your organisation grows, your open source tools should be able to scale with it. Choose tools that can handle increasing workloads without compromising on performance or security.
- Community support: Tools with active communities and extensive documentation are more likely to receive regular updates and bug fixes, making them a more secure and reliable choice.
- Compatibility: Make sure that the open source tools you select are compatible with the operating systems, platforms, and environments that your organisation uses.
- Customisation: Look for open source tools that offer flexibility and customisation options, allowing your teams to tailor them to their specific needs.
- Cost: Don’t forget to evaluate the total cost of ownership, including support, maintenance, and upgrades, when selecting open source tools for your DevSecOps process.
- Security: Assess the security posture and vulnerability management of the open source tools you’re considering to ensure they meet your organisation’s security requirements.
- Compliance: Make sure that the open source tools you choose meet the relevant regulatory and compliance requirements.
- Training and support: Providing adequate training and support for your teams is essential for utilising the open source tools you’ve selected effectively.
- Continuous monitoring: Regularly monitoring and updating your open source tools is necessary to address evolving threats and vulnerabilities.
- Vendor lock-in: Be aware of the risk of vendor lock-in and choose open source tools with open standards and interoperability.
- Data privacy: Ensure that the open source tools you choose comply with data privacy regulations and protect sensitive data.
- Incident response: Establishing incident response plans and procedures for security breaches is essential to minimise the impact of any potential threats.
- Collaboration: Foster collaboration between development, security, and operations teams to improve communication and enhance the overall security posture of your organisation.
- Continuous improvement: Regularly reviewing and refining your DevSecOps process is necessary to address emerging threats.
The importance of DevSecOps in today’s fast-paced digital landscape cannot be overstated. Embracing DevSecOps with open source tools is essential for building secure and reliable software systems that can withstand the ever-changing threat landscape. Don’t fall behind the competition — get ahead of the game with DevSecOps.
















































































