Prioritising web server security not only protects data but also builds trust with users, creating a safer online space for everyone. A few best practices that will help secure your web server are briefly explained here.
Web servers like Apache, Nginx and Microsoft IIS serve as the backbone of the internet, hosting websites, applications, and services that are critical to businesses and individuals alike. Ensuring the security of these servers is essential to protect against cyber threats and safeguard sensitive data.
Apache, as one of the most widely used web servers, is a prime target for attackers. However, the principles of server security outlined in this guide apply to all web servers, helping you to fortify your defences and keep your server and its contents safe from malicious actors.
What is web server security?
Web server security refers to the measures and practices taken to protect a web server from unauthorised access, data theft, and other cyber threats. It involves implementing security protocols, such as encryption, access controls, and firewalls, to safeguard the server and the data it hosts. Web server security aims to ensure the confidentiality, integrity, and availability of the server and its hosted content, protecting it from malicious attacks and vulnerabilities.
Understanding web server security is crucial for ensuring the safety and integrity of websites and data. Here are some key points to consider.
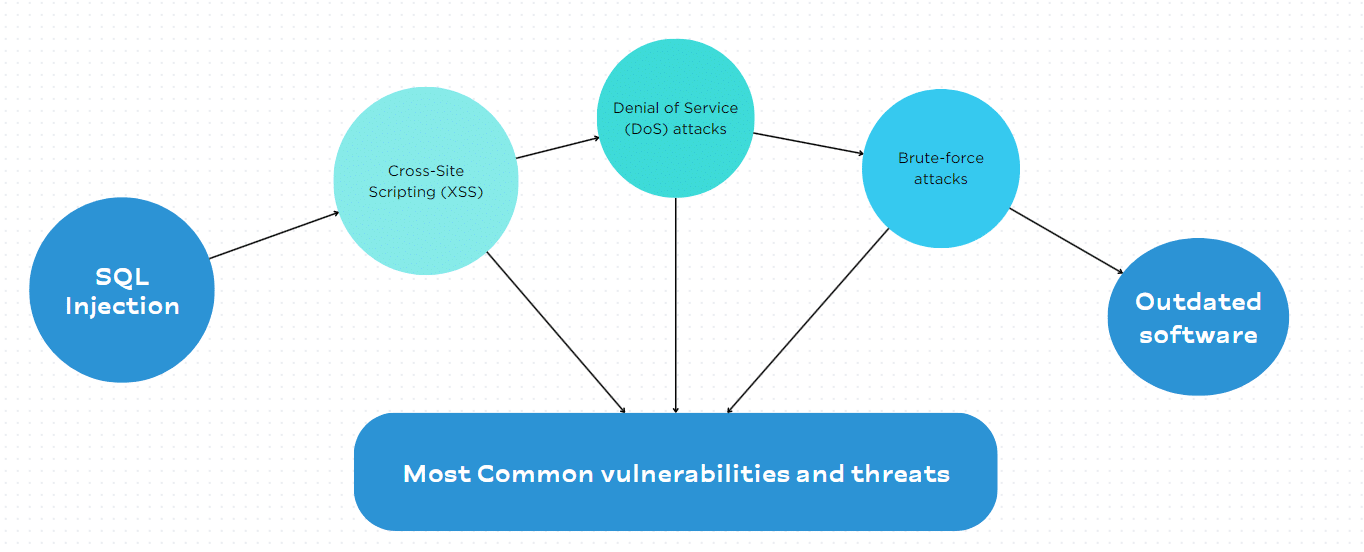
Common vulnerabilities and threats faced by web servers
Web servers are susceptible to various threats and vulnerabilities, including:
- SQL injection: Attackers exploit vulnerabilities in web applications to execute malicious SQL queries.
- Cross-site scripting (XSS): Attackers inject malicious scripts into web pages viewed by other users.
- Denial of Service (DoS) attacks: Attackers flood a web server with traffic, rendering it inaccessible to legitimate users.
- Brute-force attacks: Attackers try various combinations of user names and passwords to gain unauthorised access.
- Outdated software: Using outdated software with known vulnerabilities can compromise a web server’s security.
Impact of a compromised server on websites and data
A compromised web server can have severe consequences.
- Data breaches: Attackers can steal sensitive information such as customer data or intellectual property.
- Website defacement: Attackers can modify a website’s content, damaging its reputation.
- Loss of revenue: Downtime resulting from a compromised server can lead to financial losses.
- Legal implications: Data breaches can lead to legal issues, such as violations of data protection laws.
Tips on keeping a web server safe
To protect against threats, web server administrators should implement proactive security measures.
- Keep all software, including web server software and applications, up to date to patch known vulnerabilities.
- Use strong, unique passwords and consider implementing multi-factor authentication.
- Use firewalls to monitor and filter incoming and outgoing traffic, and IDS to detect and respond to suspicious activity.
- Follow security best practices, such as limiting access to sensitive data, encrypting data in transit and at rest, and regularly backing up data.
Best practices for securing web servers
Securing web servers is critical to protect your data and infrastructure from unauthorised access and cyberattacks. Here are the best practices for implementing authentication, authorisation, and encryption.
Authentication: Authentication is the process of verifying the identity of users or systems accessing a web server. It ensures that only authorised entities can access the server and its resources. Implement strong authentication mechanisms to verify the identity of users accessing your server such as:
- Basic authentication: Use HTTP basic authentication to prompt users for a user name and password before accessing the server. Here’s an example using Apache’s ‘.htaccess’ file:
AuthType Basic AuthName “Restricted Content” AuthUserFile /path/to/.htpasswd Require valid-user
Create the ‘.htpasswd’ file with the ‘htpasswd’ utility:
htpasswd -c /path/to/.htpasswd username
- Token-based authentication: Implement token-based authentication for API access, where clients need to include a valid token in their requests. Use libraries like ‘jsonwebtoken’ in Node.js or ‘PyJWT’ in Python to generate and verify tokens.
const jwt = require(‘jsonwebtoken’);
// Generate a token
const token = jwt.sign({ username: ‘username’ }, ‘secretKey’, { expiresIn: ‘1h’ });
// Verify a token
jwt.verify(token, ‘secretKey’, (err, decoded) => {
if (err) {
console.error(‘Token is invalid’);
} else {
console.log(‘Token is valid’);
}
});
Authorisation: Authorisation is the process of determining what actions or resources users or systems are allowed to access on a web server. It establishes permissions based on the authenticated identity of the user or system. Set up proper authorisation rules to control access to different parts of your web server. This can include:
- Role-based access control (RBAC): Assign roles to users and grant permissions based on those roles. For example, you can create roles like ‘admin’, ‘user’, and ‘guest’ with varying levels of access.
# Check if user has permission to access a resource def check_permission(user, resource): role = get_user_role(user) if role == “admin”: return True # Admin has full access elif role == “user” and resource == “restricted_resource”: return True # User has access to specific resource else: return False # Default deny access
- Directory-level access control: Use directives in your web server configuration files (e.g., Apache’s ‘<Directory>’ directive) to restrict access to specific directories based on user roles.
<Directory /var/www/html/secure> Require role admin </Directory>
Encryption: Encryption is the process of converting data into a secure format that can only be read or understood by authorised parties. It protects data in transit (e.g., over the network) and at rest (e.g., on disk) from unauthorised access or tampering. Use strong encryption protocols to protect data transmitted between the client and server.
- HTTPS: Enable HTTPS by installing an SSL/TLS certificate on your server. This encrypts data in transit, protecting it from eavesdropping and tampering. Here’s an example configuration for Apache:
<VirtualHost *:443> ServerName example.com DocumentRoot /var/www/html SSLEngine on SSLCertificateFile /path/to/certificate.crt SSLCertificateKeyFile /path/to/private.key </VirtualHost>
- End-to-end encryption: For applications handling sensitive data, consider implementing end-to-end encryption (E2EE). This ensures that data is encrypted on the client-side before transmission and can only be decrypted by the intended recipient.
const crypto = require(‘crypto’);
// Generate a key pair
const { publicKey, privateKey } = crypto.generateKeyPairSync(‘rsa’, {
modulusLength: 2048,
publicKeyEncoding: { type: ‘spki’, format: ‘pem’ },
privateKeyEncoding: { type: ‘pkcs8’, format: ‘pem’ }
});
// Encrypt data using the public key
const data = ‘Sensitive data to encrypt’;
const encryptedData = crypto.publicEncrypt(publicKey, Buffer.from(data, ‘utf8’));
// Decrypt data using the private key
const decryptedData = crypto.privateDecrypt(privateKey, encryptedData);
console.log(decryptedData.toString(‘utf8’)); // Output: Sensitive data to encrypt
|
Strategy |
How to implement |
|
Utilising firewall and intrusion detection/prevention systems |
Install firewalls and IDS/IPS to monitor and filter traffic, blocking malicious activity. |
|
Implementing a robust monitoring and logging system |
Enable logging and monitoring to detect and respond to security incidents and unusual activity. |
|
Conducting regular security audits and vulnerability assessments |
Perform audits and assessments to identify and mitigate security vulnerabilities and risks. |
|
Educating staff on security best practices |
Provide training on security best practices to ensure employees understand and follow security policies. |
|
Using security tools and services |
Utilise antivirus software, web application firewalls, and other security tools to enhance protection. |
Table 1 lists a few best strategies to enhance web server security.
Securing Apache web server
Securing an Apache web server involves implementing several best practices to protect against various security threats. Apache provides several security features that can be used to enhance the server’s security. These include:
- Access control: Apache allows you to control access to directories and files using configuration directives like Allow and Deny.
- Authentication: It supports various authentication methods, such as basic authentication and digest authentication, to control access to resources.
- Logging: Apache’s logging capabilities allow you to monitor and analyse server activity, which can help detect and respond to security incidents.
How to configure Apache securely
It’s essential to recognise that while Apache is inherently stable and secure, its level of security ultimately depends on how it’s configured. Once Apache is installed, configuring the server to be as minimal as possible is key to enhancing its security posture.
Disable unused modules: Disable any Apache modules that are not needed for your server’s operation. This reduces the attack surface and potential vulnerabilities.
# Disable modules # LoadModule example_module modules/mod_example.so
Use secure protocols: Configure Apache to use secure protocols like TLS/SSL to encrypt data in transit. Enable HTTPS by configuring SSL certificates.
# Enable SSL SSLEngine on SSLCertificateFile /path/to/certificate.crt SSLCertificateKeyFile /path/to/private.key
Limit HTTP methods: Use the Limit directive to restrict the HTTP methods that are allowed for a particular directory or URL.
<Directory /path/to/directory> <LimitExcept GET POST> Require all denied </LimitExcept> </Directory>
Additional security measures
Using additional security measures can further enhance the overall security of your server.
mod_security: mod_security is an Apache module that provides a web application firewall (WAF) to protect against various attacks, such as SQL injection and cross-site scripting (XSS).
# Enable mod_security LoadModule security2_module modules/mod_security2.so # Include mod_security configuration Include conf/modsecurity.d/*.conf
mod_evasive: mod_evasive is an Apache module that provides protection against distributed denial of service (DDoS) attacks and brute force attacks by limiting the number of requests from a single IP address.
# Enable mod_evasive LoadModule evasive20_module modules/mod_evasive20.so # Configure mod_evasive DOSHashTableSize 3097 DOSPageCount 2 DOSSiteCount 50 DOSPageInterval 1 DOSSiteInterval 1 DOSBlockingPeriod 10
Securing other web servers
Apart from Apache, other popular web servers include Nginx and Microsoft IIS (Internet Information Services). Though MS IIS is not an open source-based web server, it still needs a mention as it is a widely used web server. Table 2 gives a brief overview of each.
|
Feature |
Nginx |
Microsoft IIS |
|
Architecture |
Event-driven and asynchronous, efficient for handling large numbers of concurrent connections |
Modular architecture integrates with other Microsoft technologies |
|
Performance |
High performance and scalability |
Efficient performance, especially with Windows and ASP.NET integration |
|
Use cases |
Rate limiting, access control, SSL/TLS termination |
Request filtering, IP address and domain restrictions, integrated Windows authentication |
|
Configuration |
Regular updates required for security patches and performance enhancements |
Regular updates for security and compatibility with Windows and ASP.NET |
|
Community |
Strong community support with extensive documentation and community forums |
Strong support from Microsoft with resources, forums, and documentation |
Table 2: An overview of Nginx and Microsoft IIS web servers
Here are a few common security practices applicable to all web servers.
- Regular updates: Keep the web server software, operating system, and other components up to date with the latest security patches and updates.
- Secure configuration: Configure the web server securely, following best practices and disabling unnecessary features and services.
- Strong authentication: Use strong authentication mechanisms, such as multi-factor authentication (MFA), to protect access to the server.
- Secure communication: Use SSL/TLS certificates to encrypt data transmitted between clients and the server.
- Access control: Implement strict access control measures to ensure that only authorised users and processes have access to the server and its resources.
- Logging and monitoring: Enable logging and monitoring to detect and respond to security incidents promptly.
Securing Apache and other web servers is essential. By adopting best practices and smart strategies, organisations can shield their servers from cyber threats, ensuring their online services remain safe and reliable. Continuous improvement and vigilance are key in this ever-evolving landscape.