Unmanaged reliance on open source software may result in a support crisis over a project’s life span, as well as financial loss for the organisation. Planned and regular upgrades of open source software components are a must.
Open source components are critical to large projects for a variety of reasons. They provide cost-effective solutions by removing licensing costs and encouraging community-based innovation. Furthermore, open source encourages cooperation, providing access to a wide reservoir of knowledge and various viewpoints. These components frequently have active communities that provide rapid updates, bug fixes, and security patches. Big projects can use open source components to expedite development, minimise time to market, and retain scalability.
When integrating open source components, however, use caution. To begin with, confirming licensing compliance is critical to avoiding legal problems. Second, reliance on other projects may present security vulnerabilities or compatibility difficulties, needing ongoing monitoring and upgrades. Third, because of the reliance on community assistance, replies to issues or bugs may be delayed and ineffective. Finally, due diligence is required in assessing the long-term maintenance of open source projects to reduce the risks associated with project abandonment or obsolescence.
In this article, we will look at the many issues of keeping open source components updated. Teams must be prepared to handle updates to diverse open source components without creating any downtime.
Everything starts from proof-of-concepts
In large-scale initiatives, proof-of-concept (PoC) is an important first stage in determining the feasibility and viability of suggested solutions. It facilitates decision-making by offering concrete proof of a concept’s potential success. PoCs frequently include a prototype to test certain functionality or technologies. They enable technical feasibility testing prior to full-scale deployment.
While it is simple to leverage these open source components to create an initial proof-of-concept solution, disciplined execution and a thorough grasp of the open source components’ release cycles are essential. Otherwise, having a working solution will not be useful.
Many developers make the error of not keeping track of the numerous open source components utilised, or even pinning the open source component version and continuing to use the solution, which is not a good practice and might have major effects if this system is put in production.
Functionality-based dependencies
A typical large-scale project may have certain dependencies on other open source software. These are summarised in Figure 1.
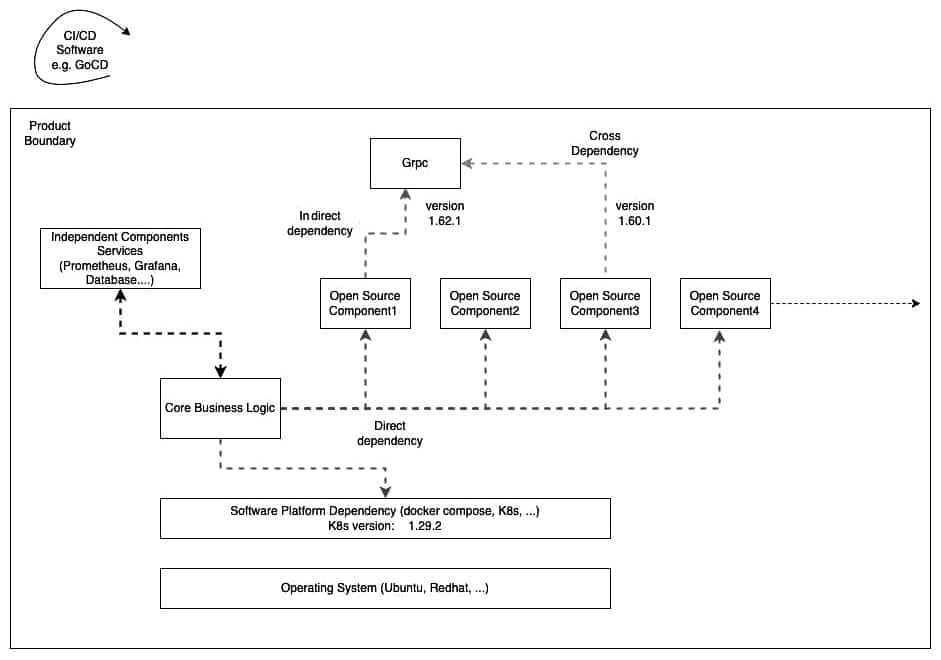
Operating system: Projects are designed and developed with a specific OS/distribution in mind. This could be the operating system and a specific distribution of it, e.g., Ubuntu Linux.
Software platform: This is a core dependency for any application. For example, some applications are delivered as containerised and may have platform dependency on Docker Compose or Kubernetes (K8), or any other container orchestration platform.
Library/modules: Each programming language provides a way to import or reuse modules developed by other developers.
Complete subsystem: Some projects may include some subsystems. Classic examples of this could be external subsystems like monitoring solutions (Prometheus, Grafana) or a database service.
Deployment subsystem: Many times, complex projects are deployed using the CI/CD solution. Though CI/CD does not use the code directly, it controls the way the project is deployed. Project Flux is a simple example of how a project could be deployed.
Except for the core business logic, all the blocks in Figure 1 are open source. Imagine that each block has its own release cycle and life span. Now we need to ensure that our product can be reliably serviced and upgraded while not failing to meet any of our client SLAs. Remember, this is not a one-time operation.
Reasons for open source component upgrades
After completing a project, an organisation should keep it in good working order. As time passes, the project must accept upgrades from the open source components. This is always necessary for a variety of reasons, and if not completed, the project becomes insecure from a security standpoint and unmaintainable from a functional standpoint. It is vital to understand that updates are ongoing activities. This is a significant task for a company wishing to employ open source projects. The following are some reasons why open source components should be upgraded.
Upgrades required due to end of life (EoL)
Sometimes project module version changes are necessary simply because some components have reached the end of their support life cycle. This must be arranged correctly and depends on the sort of component that must be updated. The work necessary to update one library may be far less than that required to change a whole software platform. It is crucial to highlight that most well-governed projects have a clear release schedule and support requirements.
The website https://endoflife.date/ offers timetables for numerous software projects’ end of life dates. This is a useful resource for many product managers. Some projects have a well-defined release cycle and end of support. For example, Kubernetes, a leading container orchestration technology, has released information on their release cycles and how long software is maintained at https://kubernetes.io/releases/release/.
It can be seen in Figure 1 that a Kubernetes update is critical and cannot be completed without first determining whether all containers operating on the platform are compatible with newer versions. To ensure that all apps function properly, the product team must meticulously organise upgrade tasks. When we employ open source components that are backed/managed by a third party organisation, the support life can be prolonged, as is the case when we use AWS’s managed Kubernetes service (Elastic Kubernetes Service).
Upgrades required due to new features
Sometimes we need to upgrade open source components since new features are launched in the projects and we want to integrate them into our product design. This includes optimisation, which is typically associated with improved performance.
Because open source products/components are utilised by a wide range of consumers, most new improvements offer value and address long-standing concerns reported by open source project participants.
There is an excellent blog post at https://layer5.io/blog/kubernetes/kubernetes-129-highlights-features-and-deprecations that discusses the many features that will be included in Kubernetes version 1.29. Assuming your project intends to use the Gateway API, you’ll want to update to the most recent Kubernetes version. Refer to https://gateway-api.sigs.k8s.io/ for further information about the Gateway API.
Upgrades required due to software bugs
Open source components are utilised by a diverse range of community members and become more stable as the user base grows. However, it is probable that you will encounter problems in the open source software, causing production troubles. If you’re lucky, the same issues will be handled in subsequent versions of components, and you’ll need to upgrade the component to address production difficulties. The speed with which you wish to upgrade the component to a newer release is entirely dependent on the sort of issue and its frequency.
Upgrades required due to security bugs
Security flaws represent substantial threats to systems and data, potentially resulting in unauthorised access, data breaches, or system compromise. Patching security issues as soon as possible helps to reduce vulnerabilities and improves the overall security posture of the program or system. Failure to fix security flaws exposes systems to exploitation by unscrupulous actors, potentially resulting in financial losses and reputational harm. Patching security flaws on a regular basis is critical for ensuring system and data integrity, confidentiality, and availability.
Security is an important feature of any production quality program, and if a problem is reported in an open source component used in the product, its reason enough to upgrade the software. Snyk is open source software that automates vulnerability repairs with a one-click pull request containing the necessary updates and patches.
Well planned upgrades
Ideally, every project and module owner should plan for frequent component updates without waiting for any of the reasons listed above. Because each upgrade necessitates a significant amount of product testing, these events must be carefully planned. Unplanned incidents may not receive adequate testing coverage. There are certain tools that might help you plan your module updates.
Dependabot is a program that automates the process of updating software dependencies. It scans your repository for obsolete dependencies and creates pull requests to update them to the newest version. This is an excellent indicator for product owners as to what fresh modifications are being made in the open source components.
Based on the alerts received from Dependabot or any other utility, thorough testing can be done to rollout product changes.
Any moderate-sized project has 100 or more open source dependencies. Monitoring modifications to open source components is crucial for several reasons. For starters, it might result in the discontinuation of updates, including security fixes, leaving systems open to vulnerabilities. Second, it indicates the end of official support, which may result in compatibility concerns or reliance on old technology. Third, without regular maintenance, projects may become incompatible with changing software environments, impeding development. Furthermore, ageing components may lack community participation, which reduces the availability of resources, documentation, and technical support. Finally, remaining updated about open source components aids in migration or replacement planning, as well as assuring software system life span and security.