With humongous amounts of data available on IoT devices in real-time, the connected world has become both exciting and challenging. Systems that prevent access to this data by unauthorised persons have become crucial. A few security principles have been spelt out to ensure a smart home that runs on connected devices is not invaded. Also, some very interesting trends are shaping the future of IoT solutions.
The Internet of Things (IoT) is dominating multi-disciplinary solutions in sectors like retail, manufacturing and healthcare. IoT services share data in real-time which is analysed and used for business processing. But for smarter solutions that span different industrial sectors, this may not be enough and unconventional solutions like Internet of Digital (IoD) and Internet of Humans (IoH) are needed.
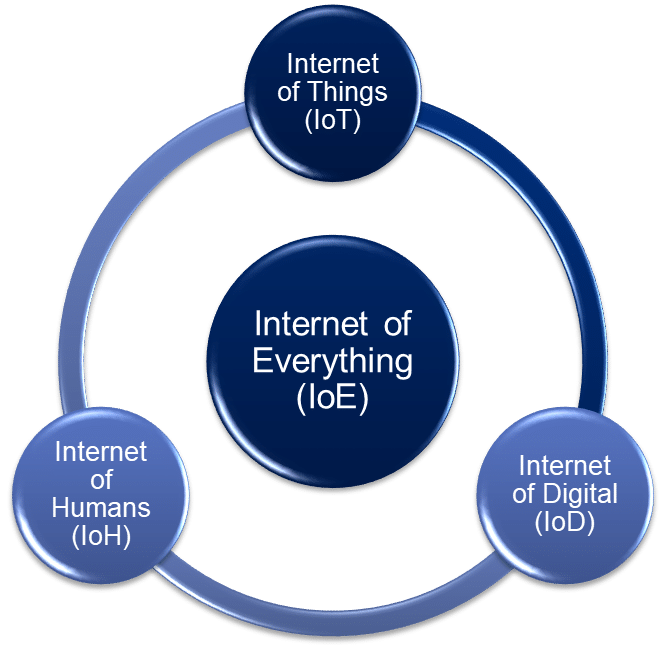
Internet of Everything (IoE) is the amalgamation of IoT, IoD and IoH. It helps to create a connection between people, smart devices and organisations, and is driven by four principles – people, data, things and process. New age architecture for interdisciplinary application design needs a ‘boundaryless’ approach. For example, an end-to-end solution for retail stores requires financial services, retail store monitoring services, order processing to manufacturing units, and inventory management.
Internet of Digital is the group of data service applications that handle social networks, media services, data analytics, and cloud platforms, simply termed as SMAC (social, mobile, analytics and cloud). Internet of Humans deals with the smart devices that interact with humans like smart wristbands and connected medical devices to monitor and collect various datasets. These can be used for remote patient monitoring using cloud-based platforms or remote health advisory solutions through contact centre AI services.
Internet of Everything (IoE) is an emerging technology and requires costly infrastructure. However, smart ready-to-use IoE services are the future.
Some popular real-time use cases of Internet of Everything (IoE)
Here are the top 10 popular use cases of Internet of Everything (IoE).
Smart cities
- Real-time traffic management: IoE sensors monitor traffic flow, optimise traffic lights, and reroute vehicles to avoid congestion, reducing travel times and emissions.
- Environmental monitoring: Air quality sensors track pollutants in real-time, allowing for immediate adjustments and promoting public health.
- Smart waste management: Connected trash bins indicate fill levels, enabling efficient waste collection and reducing unnecessary truck trips.
Industrial automation
- Predictive maintenance: Sensors on industrial equipment monitor performance and predict potential failures in real-time. This allows for preventive maintenance, avoiding costly downtime and ensuring smooth operations.
- Remote monitoring and control: Industrial processes can be monitored and controlled remotely via IoE, improving safety and allowing for adjustments based on real-time data.
- Real-time inventory tracking: IoE tracks inventory levels, optimising stock management and preventing stock outs or overstocking.
Energy management
- Smart grids: IoE enables two-way communication between power grids and consumers. Real-time data on energy usage allows for dynamic pricing, optimised distribution, and integration of renewable energy sources.
- Demand response management: Consumers can adjust energy usage based on real-time grid demands, promoting efficient energy consumption and grid stability.
- Smart homes and buildings: IoE thermostats and appliances adjust energy consumption based on real-time occupancy and weather data, reducing energy waste and lowering utility bills.
Healthcare
- Remote patient monitoring: Wearable devices and sensors track vital signs like heart rate, blood pressure, and blood sugar in real-time, enabling remote patient monitoring and timely intervention during emergencies.
- Connected medical devices: IoE allows medical devices to share data in real-time, improving diagnosis, treatment, and patient outcomes.
- Hospital resource management: IoE can track location and usage of medical equipment and supplies, optimising resource allocation and improving hospital efficiency.
Retail and supply chain management
- Real-time asset tracking: IoE tracks the location and condition of goods throughout the supply chain, improving transparency, reducing loss, and optimising delivery routes.
- Personalised marketing: IoE can gather real-time customer data in stores, enabling targeted promotions and enhancing the overall shopping experience.
- Inventory management: Real-time tracking of inventory levels allows retailers to optimise stock levels and prevent stockouts, leading to improved customer satisfaction.
Agriculture
- Precision agriculture: Sensors monitor soil moisture, nutrients, and weather conditions in real-time, allowing farmers to optimise irrigation, fertilisation, and other practices, increasing yield and reducing waste.
- Livestock monitoring: IoE sensors can track the health and location of livestock, enabling early detection of disease and improving animal welfare.
- Real-time crop monitoring: IoE allows farmers to monitor crop health and growth remotely, assisting in making informed decisions about harvesting and resource allocation.
Environmental monitoring
- Forest fire detection: IoE sensors can detect fires in real-time, enabling faster response and minimising damage.
- Water quality monitoring: Sensors in water bodies can monitor water quality in real-time, allowing for timely intervention in case of pollution.
- Flood prediction and monitoring: IoE can collect and analyse data from various sources to predict and monitor floods, enabling early warnings and evacuation efforts.
Connected cars
- Real-time traffic updates: Connected cars share traffic data, enabling navigation systems to provide real-time updates and suggest alternative routes.
- Remote diagnostics and maintenance: IoE allows manufacturers to remotely diagnose vehicle issues and schedule maintenance, improving safety and convenience.
- Autonomous vehicles: IoE plays a crucial role in enabling autonomous vehicles to perceive their surroundings, communicate with other vehicles, and navigate safely.
Personal safety and security
- Smart homes and buildings: IoE can equip homes and buildings with real-time security systems, including intrusion detection, access control, and fire alarms.
- Wearable safety devices: Devices like smartwatches with fall detection can send alerts to emergency services in real-time, potentially saving lives.
- Personal tracking devices: Real-time tracking of individuals, particularly children or elderly individuals prone to wandering, can ensure their safety and well-being.
Entertainment and gaming
- Smart TVs and streaming devices: IoE allows for personalised recommendations and real-time content updates.
- Interactive gaming: It enables immersive gaming experiences where players interact with the environment in real-time.
- Connected fitness devices: IoE fitness trackers and equipment can provide real-time feedback.
| Amazon Timestream for IoT use cases |
| For IoT use cases, where there are millions of events to be processed in real-time and data feeds come from multiple IoT enabled devices and other sources, it is challenging for an architect to choose a database that can handle the throughput at par. RDBMS or NoSQL databases are difficult to manage in such cases, as they may not perform well or be too costly.
To address this, AWS has developed Timestream, which is a fast, scalable, serverless time series database that performs 1000 times faster than an RDBMS and costs one-tenth of the traditional database platforms. Timestream can store and analyse millions and trillions of events in real-time from IoT sources and can be integrated with SageMaker or QuickSight for analytics, visualisation or processing time series data. Timestream is serverless and scalable, with an auto-scaling facility to ensure high availability with low cost and optimal resource usage. It can help manage the entire data life cycle. Timestream has a memory store for faster processing of the latest data and magnetic store for low-called historical data. Timestream provides encryption at rest and at motion, and allows key management service (KMS) based customer managed key (CMK) to encrypt historical data (in magnetic stores). A built-in time series function enables quick analysis of time series data using SQL queries or to interpolate, aggregate and derive metrics in real-time. The data in memory operation is backed up automatically in s3 bucket for safety. |
IoT security principles
We now look at the top 8 IoT security principles that have been laid down keeping modern security threats and vulnerabilities in mind.
No universal passwords
Concept: Moving away from a single password for all devices. Each device should have a unique and strong password or use alternative authentication methods like biometrics (fingerprint scan) or multi-factor authentication (MFA).
Real-time example: Imagine a home with multiple smart devices, where each device, like the smart lock, thermostat, and camera, has its own unique password or requires fingerprint verification for access. This prevents a single compromised password from granting access to all devices.
Secured interfaces
Concept: Securing communication channels between devices, gateways, and the cloud using strong encryption protocols like TLS/SSL. This protects data from eavesdropping and tampering during transmission.
Real-time example: A fitness tracker transmits workout data to a smartphone app. Data encryption ensures only authorised devices can access the data, safeguarding sensitive health information.
Proven cryptography
Concept: Implementing established and well-tested cryptographic algorithms for encryption and decryption of data. This ensures the confidentiality, integrity, and authenticity of data throughout its life cycle.
Real-time example: A smart home hub uses AES-256 encryption to secure communication between connected devices and the hub. This industry-standard algorithm makes it incredibly difficult for attackers to decipher the data.
Security by default
Concept: Devices should be shipped with security features enabled by default, requiring no manual configuration by users. This simplifies security for non-technical users and ensures a baseline level of protection.
Real-time example: A new smart speaker comes pre-configured with strong password requirements and automatic software update functionality. This eliminates the risk of users leaving the device vulnerable with weak passwords or outdated software.
Signed software updates
Concept: Updates should be digitally signed by the manufacturer to verify their authenticity and prevent installing malicious firmware disguised as updates.
Real-time example: A notification appears on a smart TV prompting for a software update. The update is digitally signed by the manufacturer, assuring users it’s legitimate and not a tampered version.
Software updates applied automatically
Concept: Devices should automatically download and install security patches whenever they become available. This ensures devices are always protected against the latest vulnerabilities.
Real-time example: A smart thermostat automatically downloads and instals a security patch that addresses a recently discovered vulnerability in its software. This eliminates the need for manual intervention and ensures timely protection.
Vulnerability reporting scheme
Concept: Establishing a clear and accessible channel for users and researchers to report discovered vulnerabilities to manufacturers. This allows for prompt identification, investigation, and patching of vulnerabilities.
Real-time example: Security researchers discover a vulnerability in a popular smart home camera brand. They report the vulnerability through the manufacturer’s dedicated vulnerability reporting portal. The manufacturer promptly investigates, develops a patch, and releases it to all users.
Security expiration date
Concept: Assigning a life span to the security capabilities of a device. Manufacturers should clearly communicate when a device will no longer receive security updates or support, allowing users to make informed decisions about continued use or replacement.
Real-time example: A manufacturer announces that a specific model of smart sensors will no longer receive security updates after a certain date. Users are advised to upgrade to newer models with ongoing security support to maintain protection against evolving threats.
By adhering to these principles, manufacturers and users can work together to create a more secure IoT ecosystem, mitigating the risks associated with connected devices and protecting sensitive data in today’s ever-evolving threat landscape.
Securing home architecture with IoT
A secure smart home is a living space that leverages the convenience and security benefits of interconnected devices while prioritising data protection and minimising vulnerabilities. In a smart home, security is a top priority. Here’s what it entails:
Network router and firewall: This acts as the central control point for your network traffic. A good firewall filters incoming and outgoing data, blocking unauthorised access attempts.
Smart hub (optional): This centralises communication between various IoT devices and serves as a control centre for your smart home ecosystem. Choose one with robust security features.
IoT devices: Smart lights, thermostats, locks, cameras, and more – these are the gadgets that bring intelligence to your home. Ensure each one has strong security capabilities.
Intrusion detection/prevention system (optional): These systems actively monitor your network for suspicious activity and can take steps to prevent cyberattacks.
Mobile app: This application allows you to control your smart home devices remotely. It should be secured with strong passwords and multi-factor authentication.
A few principles must be adopted to ensure the security of your smart home.
- Network segmentation: Don’t let your smart fridge share the same network as your computer. Segment your network. Create a separate network (often called a ‘guest network’) specifically for your IoT devices. This isolates them from your personal devices, minimising damage if an IoT device is compromised.
- Strong authentication: Move beyond basic passwords! Implement strong and unique credentials for all your IoT devices. Consider password managers for secure storage. Additionally, enable multi-factor authentication (MFA) whenever available for an extra layer of security.
- Secure boot and execution environment: This ensures only authorised software runs on your devices. Imagine a bouncer at a club, verifying software before it enters the device.
- Patch management: Just like patching a hole in your clothes, software patches fix vulnerabilities in your devices. Set your devices to automatically download and install updates to stay protected.
- Physical security: Don’t leave your smart gadgets vulnerable! Implement physical security measures like tamper-evident seals (e.g., smart meters) and secure enclosures for hubs or gateways.
- User awareness: Educate yourself and your family about potential threats and best practices. This includes recognising phishing attempts, avoiding suspicious links, and reporting anomalies to device manufacturers.
Here are two examples of how this is put into practice.
Scenario A: You purchase a smart lock.
Secure architecture: The lock connects to your secure home network with a unique password and MFA enabled for access.
Explanation: This prevents unauthorised access attempts, even if someone discovers the password.
Scenario B: You have a smart camera system.
Secure architecture: The cameras connect to your secure network, and the video feed is encrypted during transmission. The cameras receive automatic security updates and have tamper-evident seals.
Explanation: Encryption protects your video data from prying eyes. Updates keep the cameras patched against vulnerabilities. Tamper-evident seals alert you if someone tries to physically tamper with the cameras.
As technology evolves, exciting trends are shaping the future of IoT solutions, paving the way for a more connected and intelligent world. Here’s a breakdown of these trends with the latest real-time examples.
Integration of AI and ML
Trend: Artificial intelligence (AI) and machine learning (ML) are becoming embedded within devices, enabling them to analyse data, identify patterns, and make intelligent decisions in real-time.
Real-time example: Predictive maintenance in buildings: Sensors on HVAC systems collect data on temperature, pressure, and vibration. AI algorithms analyse this data to predict potential equipment failures before they occur, preventing costly downtime and ensuring efficient building operations.
Rise of edge and fog computing
Trend: Shifting data processing closer to the source of data collection, at the ‘edge’ or ‘fog’ of the network. This reduces latency (delay) and improves efficiency for real-time applications.
Real-time example: Smart Retail: Cameras and sensors in stores track customer behaviour and product interactions. Edge computing allows for real-time analysis of this data to optimise store layouts, personalised product recommendations, and improve customer experience.
Blockchain for enhanced security and transparency
Trend: Blockchain technology, known for its secure and decentralised ledger system, is finding application in IoT to ensure data privacy, tamper-proof records, and secure transactions.
Real-time example: Food traceability: Sensors on food packaging monitor temperature and location throughout the supply chain. Blockchain stores this data securely, providing consumers with transparent information about the origin and journey of their food, improving food safety and reducing fraud.
Increased focus on interoperability and standardisation
Trend: The need for seamless communication and data exchange amongst devices from different manufacturers is driving efforts towards standardised protocols and interoperable platforms.
Real-time example: Connected cars: Different brands of cars are now incorporating standardised protocols like V2X (vehicle-to-everything) communication, allowing vehicles to communicate with each other and roadside infrastructure, improving traffic safety and facilitating autonomous driving capabilities.
Low-power wide area networks (LPWAN) for broader reach
Trend: LPWAN technologies like LoRaWAN and NB-IoT enable long-range communication with low power consumption, allowing for deployment of IoT devices in remote locations or battery-powered applications.
Real-time example: Environmental monitoring: Sensors in remote areas can monitor air quality, water levels, and other environmental factors using LPWAN networks. This enables real-time data collection and facilitates informed decision-making for environmental protection and resource management.
Emphasis on security and privacy
Trend: As the number of connected devices explodes, security and privacy concerns are paramount. Manufacturers are focusing on robust security protocols, data encryption, and user control over data collection and usage.
Real-time example: Smart wearables for healthcare: Fitness trackers and smart watches that monitor health data incorporate strong encryption to protect sensitive health information and provide users with control over who can access their data, ensuring privacy and reducing security risks.