Manual onboarding of a large number of Industrial Internet of Things devices into a network is cumbersome and comes with security risks. The FIDO Device Onboard (FDO) standard automates the process, making it simpler and safer.
IoT or the Internet of Things has taken the world by storm. IoT devices may include devices ranging from smart speakers, smart TVs, and even doorbells, to Industrial IoT (IIoT) devices like construction vehicles, supply chain robots, and so on.
The International Data Corporation (IDC) expects the IoT market to surpass the US$ 1 trillion mark in 2022. Industrial IoT is a major component of all IoT devices, and comprises the following.
- Industrial things: This contains devices like robots, PLCs (programmable logic controllers), sensors, actuators, and so on. They are generally connected to microcontrollers and microprocessors for functioning.
- Connectivity: As the name suggests, this is essential for providing internet or network connectivity to industrial things. It may contain switches, access points, routers, VPNs, gateways, and so on. These are responsible for creating and maintaining a network of industrial devices and connecting them to servers. Not all industrial things support Wi-Fi (IEEE 802.11) or internet connectivity. For such devices, other communication protocols like Bluetooth (RL78/G1D), Zigbee (IEEE 802.15), and LoRa WAN (IEEE 1451.0) are used.
- Servers: This is where the main computing, storage, and operations happen, leading to the proper functioning of the cluster or group of industrial things. Depending on the industry, the server may be hosted on a cloud platform like AWS, GCP, or Azure or on on-premises machines. It is also possible that the servers are on an offsite data centre.
- Insights and actions: The administrator dashboards monitor the functioning, state, and condition of the industrial things. This allows them to take action on one or multiple devices from a remote computer or mobile device. This also provides event-based alarms and alerts to the administrator in case of any issues or malfunctions.
So Industrial IoT or IIoT needs an extensive setup and onboarding procedures — connecting through the network, enrolling on the servers, adding them to the analytics dashboard, and so on. The question then is: How long would it take to manually onboard a large number, for example, 10,000 gateways, devices, and sensors? According to a 2017 study by Kaiser Associates Research and Analysis, it would take over two-man years. Yes, it is pretty cumbersome work to onboard everything manually.
Hence, the FIDO Alliance has come up with an automated and secure IoT device onboarding standard, called FIDO Device Onboard, or FDO. It is a specification for automated and secure IoT provisioning.
The FIDO Alliance, which has been working on securing services and accounts in a passwordless way, came up with the FDO specification in 2020. After some minor modifications, the FDO Specification 1.1 was proposed in 2021.
The FDO standard is currently used in various IIoT devices, mainly devices based on Intel Arm. It has proved to be one of the essential standards in the fast, secure, seamless onboarding of IoT devices. It uses cryptographic technologies to verify the ownership of an IoT device and then enrols it in the specified service seamlessly.
The FDO specification involves the use of an FDO software client installed on the IoT device when it is manufactured. A Root of Trust (RoT) key is also generated to uniquely identify each device and is saved within it, preferably within the trusted platform module (TPM) or any other secure element from which it cannot be tampered with. It can also be placed in the file system, though that is not very secure. A corresponding supply chain token is also generated, and it moves as and when the device is transferred from the manufacturer to the wholesaler, retailer, and so on, and finally to the customer. The customer enrols it on the target cloud. When the device is powered on and connected to the internet, it automatically gets provisioned taking all configurations from the target cloud.
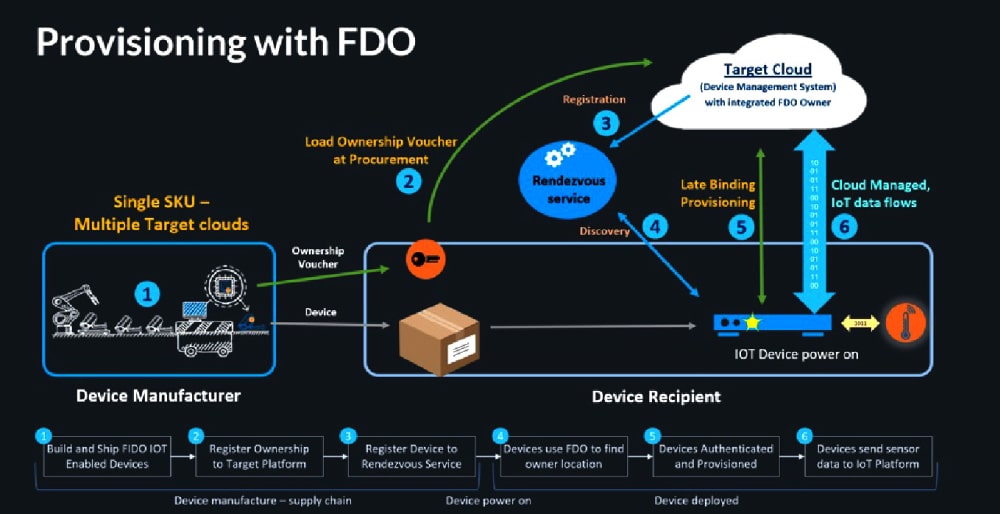
This can be explained with the help of an example. Let us assume there is a security camera manufacturer M. This company produces five security cameras, out of which company A purchases three and company B purchases two. All five security cameras have a unique RoT key stored in their secure element. The three cameras that A purchases are sold to retailer R1 while the two B purchases go to retailer R2. When company A powers on the camera purchased, it is automatically connected to company A’s server, and can be streamed by its administrator without any configuration on the camera. The same goes with the cameras procured by company B.
You may wonder how this is possible so seamlessly without any configuration on the camera. This is what happens behind the scenes. When manufacturer M manufactured the five cameras, each had a unique RoT stored in the secure element. When the devices are sold to the resellers, they use the reseller tool to generate an ‘ownership token’ when selling the product to the end user. Here, company A and company B are the end users. Hence, company A enrols its ‘ownership tokens’ on the server while company B does the same. Now when the camera is powered on, it contacts a rendezvous server, which may be of the camera manufacturer, and authenticates itself with device attestation. The rendezvous server redirects the devices to the servers of company A and company B, from where it can automatically install the configurations. This is a completely automated and seamless process, involving no manual configuration. Now, after the automated configuration is done, the device is ready to stream video feeds to the company servers.
It’s pretty clear now that the FDO standard, when implemented for IoT devices, especially in industrial scenarios, can reduce human effort manifold and also provide a secure way of onboarding devices.
In the case of manual device onboarding, technicians very often get to know the credentials of the company network in order to connect devices to it. This can prove to be a major security risk if the credentials are leaked. FDO, on the other hand, uses the public key cryptosystem to securely onboard the IoT devices without any hassle or security lapses. It is ideal for corporate and industrial devices.