In a traditional enterprise, all users, devices and systems are located and ring-fenced within a well-defined DMZ perimeter. Here, VPNs are leveraged to provide limited employees, clients and vendors with secure remote access to internal IT systems. Post the pandemic, however, almost all employees in many enterprises are working from home. To quickly facilitate remote access to IT systems, many IT departments have started using VPNs for all. This may help in business continuity, but increases the security threat surface. This is where a blockchain defined perimeter comes in.
The hybrid work model is the new normal and traditional VPNs have become increasingly insufficient to address the needs of the modern digital enterprise. Cybersecurity is a critical concern for IT teams with so many people working remotely on their devices. VPN technologies lack the ability to enforce granular access control and network privileges. This is where zero trust and blockchain technologies are being leveraged for new solutions.
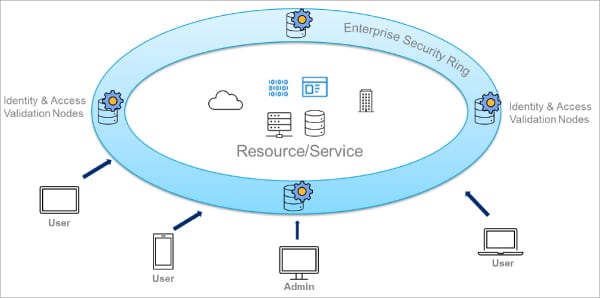
Blurred enterprise security perimeter
Vendors and clients now require anytime, anywhere, and instant access to applications. The migration of IT infrastructure and systems to the cloud, the widespread use of bring your own device or BYOD, and IoT are the norm today. So the previously closed IT environment has quickly transformed into a hybrid, highly networked and widely distributed ecosystem. This growing ‘mobility’ of users and a swelling enterprise perimeter has resulted in greater exposure to cyberattacks. With the IT no longer centred on an enterprise’s offices and internal data centres, the enterprise security perimeter is blurring. So security teams need to look at new approaches and technologies to secure the modern digital enterprise ecosystem. The internet has become the enterprise network, and on-premises solutions can’t establish secure network connections, especially with the advent of BYOD leaving the door open for hackers and unauthorised users. As a result, in today’s hybrid world, a traditional hardware-defined network perimeter and trust model is no longer viable.
Software defined perimeter
A software defined perimeter (SDP) is a security methodology that distributes access to internal applications based on a user’s identity, with trust that adapts based on context. First conceptualised by the US Defense Information Systems Agency in 2007, SDPs are built on a need-to-know model with trust that is constantly monitored and adapted based on a range of criteria. They make application infrastructure invisible to the internet, reducing the attack surface for network based attacks (DDoS, ransomware, malware, server scanning, etc). SDP guarantees that all endpoints attempting to access enterprise infrastructure are authenticated and approved.
This perimeter takes a different approach compared to traditional network based security. Instead of focusing on securing the network, it focuses on securing the user, the application, and the connectivity in between. Four core principles differentiate SDP technologies.
- Trust is never implicit: SDPs only grant application access to users who are authenticated and specifically authorised to use an app. Furthermore, authorised users are only granted access to the application, not the network.
- No inbound connections: By responding with outbound-only connections, SDPs keep the network and application infrastructure invisible to the internet and therefore impossible to attack.
- Application segmentation, not network segmentation: SDP provides native application segmentation that can control access on a one-to-one basis, resulting in far more granular segmentation, which is much easier for IT teams to manage.
- Secure internet leverage: SDP is focused on securing user-to-application connections over the internet rather than securing users’ access to the network.
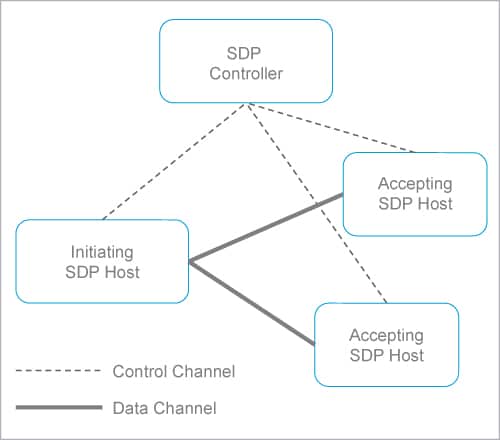
Figure 1: Software defined perimeter modules
Figure 1 shows SDP components and interactions. SDP architectures are made up of two main components — SDP controllers and SDP hosts. Control and data channels are separated. An SDP controller determines which SDP hosts can communicate with each other. An SDP host can be either initiating or accepting. An initiating SDP host communicates with an SDP controller to determine which hosts they can connect to. An accepting SDP host only accepts allowed communications and connections from an SDP controller.
Zero trust and SDP are based on the same philosophy. Rooted in the principle of ‘never trust, always verify’, they are designed to protect distributed digital environments by leveraging segmentation, preventing lateral movement, providing a Layer 7 threat prevention, and simplifying granular user-access control.
An SDP not only reduces the risk to endpoints that connect from anywhere, but also—with the help of an SDP controller—distributes network resources more evenly. Because these resources are defined on an individual basis, access control is centralised as well as simplified, ensuring secure access throughout the entire organisation. Thus, SDP addresses enterprise issues by enabling remote access use cases such as finding VPN alternatives, securing multi-cloud access, and reducing third-party risks.
SDP or zero trust network architecture denies access to resources unless the user or machine has been given explicit permission. There are no implicit trust relationships. Moreover, those access rights are continually evaluated and approved (or declined) in real-time for each identity, every time access is requested.
This ‘never trust, always verify’ validation policy is the primary difference between zero trust and legacy network security models. It works through a variety of methods, including user authentication, authorisation, and inspection, and is based on criteria, such as a user’s identity, location, operating system and firmware version, and endpoint hardware type. The zero trust approach provides granular, least-privilege access to limit lateral movement.
Blockchain defined perimeter
SDP and zero trust platforms provide comprehensive secure access to applications and environments, independent of user, device, and location. SDP, stitched together with blockchain technology, is able to deliver fine-grained micro-segmented network access to business applications, irrespective of whether they are hosted on-premises or across one or multiple clouds.
Blockchain technology is an immutable time-stamped series of records that is cryptographically secure, distributed and managed by a cluster of nodes. The three pillars of blockchain technology – decentralisation, transparency and immutability – deliver a scalable, resilient and robust backend system along with a new breed of tools for digital identity, authentication and authorisation of users as well as connected devices.
Challenges of BYOD and a blockchain based solution
BYOD is a practice followed by many organisations where employees can use their personal devices for work purposes. It may bring a lot of advantages, but also leads to security issues. Data can be leaked because of the weak authentication technique used to verify the user and the device. A secure authentication technique is what the organisation needs. Blockchain is the answer to this because it uses cryptographic technology that’s not easy for a hacker to break. In order to secure sensitive data, a record-keeping model is built using blockchain technology where every activity related to a record is documented in the digital ledger. This ledger can be used as evidence collection for further investigation. This solution helps organisations to minimise the cases of data leakage while allowing employees to bring their device.
Blockchain is a cryptographic technology that records all user transactions in a digital ledger that is distributed across the network. Blockchain platform is not dependent on any individual entity because the ledger is shared in a decentralised way. It prevents occurrence of human errors, which make it reliable. The record can be accessed from anywhere and the confidentiality of the data is maintained by encryption and hashing methods. The use of cryptography prevents unauthorised access to the network and ensures only legitimate users are allowed to participate.
The key layers and components of a typical blockchain defined perimeter (BDP) are depicted in Figure 3. The security framework consists of authentication and authorisation modules. The authentication process is comprehensive, covering user and device checks. Only authorised users are allowed to access enterprise resources. Enterprises may choose to deploy infrastructure in their data centre, on a public cloud or use a hybrid model. End users may use enterprise managed devices or unmanaged BYOD devices to connect via any kind of network channel to access enterprise resources.
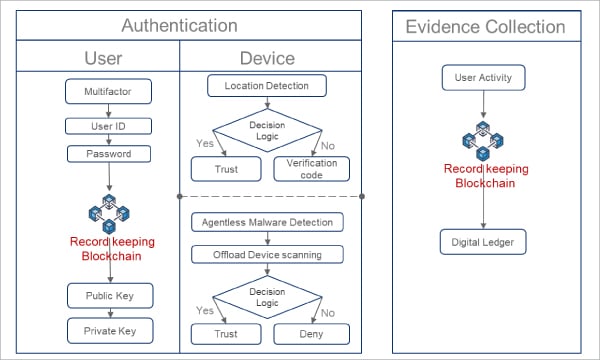
Blockchain technology strengthens zero trust network access in the following ways.
- Access protection: This is a form of access management that is designed to let trusted traffic in. A combination of setting access security policies, monitoring usage, and managing usage creates an adaptive access protection model. The authentication trust model comprises user and device authentication with location detection capability. This process prevents data leakage through unauthorised access and malware infection. The first part is a user authentication process. It uses multifactor authentication, where the user needs to key in their ID, password and second factor pass code. The authentication process then goes through the blockchain process, where a private key and public key is assigned to the user. Blockchain uses an asymmetric cryptography mechanism to authenticate transactions. Data on employee private keys is not kept in the database but only stored in the blockchain. Users get a public key during registration, which acts as user identification in the blockchain. The key is kept in the authentication database. The second part is the device authentication process where the device goes through two phases. The first phase is where the malware database server does offload scanning to find out if the device is clean. If this is so, the device goes through the second phase of the authentication, which is location detection. Company policies are applied based on location, and access is granted if conditions are satisfied. As an additional security measure, users are asked to provide a verification code. This authentication is agentless as offload scanning is done through the network without the user needing to install anything on the device.
- Visibility and forensics: In order to maintain compliance with and enforce the requisite policies and systems, organisations should implement procedures for the continuous visibility and assessment of their environment. These procedures have a constant cycle of implementing a ZTNA (zero trust network access) posture, monitoring it, and adjusting it. In this model, user records are linked to blockchain and kept in cryptography format; they can only be updated with the appropriate authentication. Every change made to the document is notified to the owner and everyone in the chain. The last phase is the evidence collection technique, where a digital ledger from the blockchain is used to record all user and device activity. This digital ledger is tamper-free and can be viewed by everyone in the loop. This can be perfect evidence for investigation if data gets leaked in the organisation.
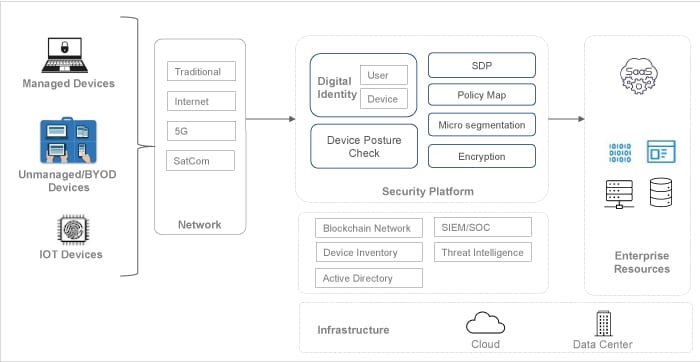
Figure 4: Deploying blockchain for SDP
Open source platforms
There are many blockchain open source platforms available that can be leveraged for implementing a blockchain defined perimeter. Some of them are listed below.
- Hyperledger: Hyperledger Foundation hosts a number of enterprise-grade blockchain software projects.
- Ethereum: This is an open source blockchain platform that helps in running smart contracts and provides different programming tools to create them.
- BigchainDB: This open source distributed ledger system is designed for storing large data sets and enabling its developers to deploy various blockchain proofs-of-concepts and applications.
- HydraChain: This is an open source extension of the Ethereum blockchain platform that helps in developing and deploying different permissioned distributed ledgers.
- Corda: This is one of the preferred open source blockchain platforms for building and developing various permissioned distributed ledger systems.
- Tron: This is one of the largest blockchain based operating systems.












































































