CIOs have wanted to enable remote working and bring your own device (BYOD) policies since long, but never took the tasks up as a top priority. Covid-19 changed that and compelled every enterprise to explore both. Network and security teams, which used to raise objections earlier, have realised that remote working and BYOD are inevitable, and are redesigning enterprise ecosystems to enable them. In this article, we will explore virtual desktop infrastructure (VDI) as a solution for securing enterprises that have implemented remote working and BYOD policies.
the pandemic has enhanced the demand for work from remote environments. As a result, OEMs, infra and cloud providers, application vendors, researchers, analysts, and service integrators have all come together to explore solutions and develop the products to meet this demand.
Lockdowns imposed due to the pandemic made enterprises quickly explore various options to enable employees to contribute to enterprise productivity while working from home.
Some companies purchased a large number of new laptops and couriered these to the homes of their employees. They installed VPN agents and set up VPN systems on a war footing. Though these offered a quick fix solution, they had serious limitations. With VPNs, the enterprise ecosystem is exposed to the outside world. Compromised end user devices and networks created many vulnerabilities, and opened the doors for hackers. Laptop procurement, too, had supply chain issues. Employees not satisfied with the laptops provided by the company requested that they be allowed enterprise application access from their personal device. CIO teams have long been mulling over the bring your own device (BYOD) policy for their organisations, too.
VDI as a solution
Remote work and BYOD require a redesign of the end-to-end enterprise ecosystem. Virtual desktop infrastructure (VDI) is meant for just this. VDI technology has a long history, and has matured enough to meet any enterprise remote working needs. It is built from scratch with a focus on security, the user experience and agile operations.
Work from anywhere, any time, using any device requires an elevated security posture and can’t depend on existing castle models. The zero trust security concept that has lately become popular in the security community rightly reflects and fits well into the remote work and BYOD scenarios.
Security vulnerabilities with remote work and BYOD
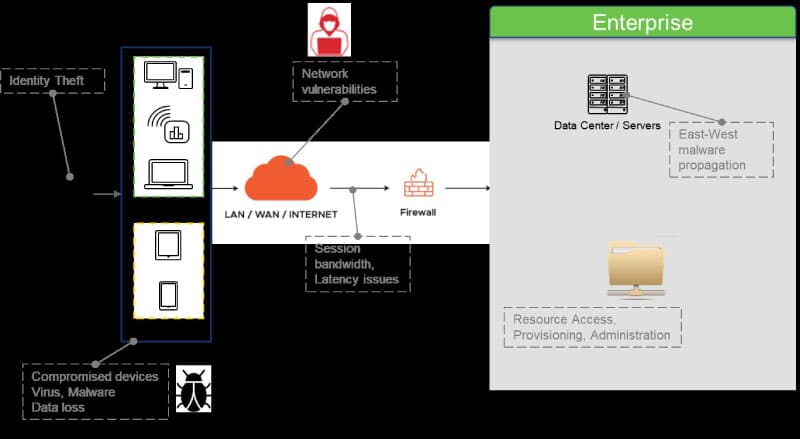
Figure 1 shows the threat landscape in remote work and BYOD scenarios. End user devices are susceptible to viruses and malware. Unless the user diligently takes care to keep the OS and applications updated with the latest security patches and leverages industry standard anti-virus software, devices are vulnerable and can easily get compromised. When these compromised devices are used to access enterprise resources, there is every chance the malware finds its way into the enterprise network. Once it gets there, it propagates laterally in an east west direction to take control over more resources. Data gets transferred to the end point and can get into the wrong hands. User sessions over the network are prone to hacking.
How VDI handles security vulnerabilities
VDI is built from the ground up to address the various threats mentioned just now. Figure 2 summarises the controls imposed at each stage by VDI.
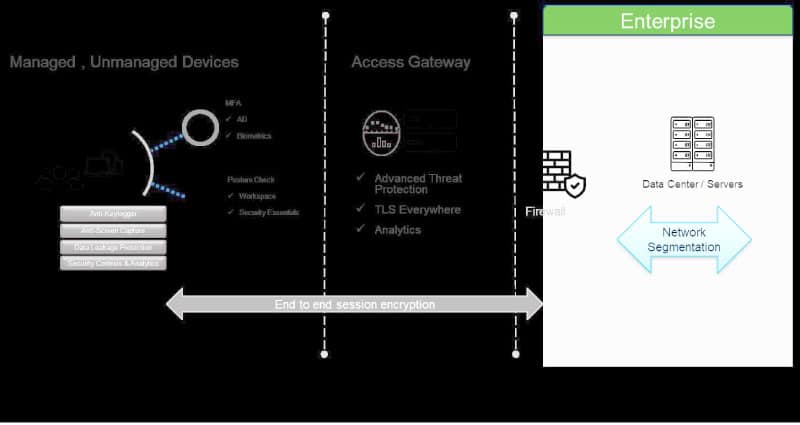
VDI leverages proprietary protocols for session streaming to the end point. Popular protocols in use are ICA from Citrix, and PCoIP and Blast from VMware. User sessions are encrypted end-to-end so that hackers cannot tamper with them during transmission.
Multiple levels of authentication are enforced for better security and to protect identity hijacks. Tokens, biometrics, and certificates over another communication channel are leveraged as second factor authentication to ensure only the right user gets access.
No data gets transferred to or from the end user device. Posture checks and conditional access allow deployment of security policies. VDI vendors have amplified security controls with anti-keyloggers and screen capture disablers to protect enterprise data and applications.
Even though network segmentation is not an integral part of VDI, it complements the VDI security posture in data centres to control east west traffic. This is important, as the adversary who somehow manages to pass through enterprise doors tries to move laterally to gain control over more and more devices and services in the enterprise. Network segmentation imposes security checks at each component, which stops unwanted east west traffic.
Conditional access
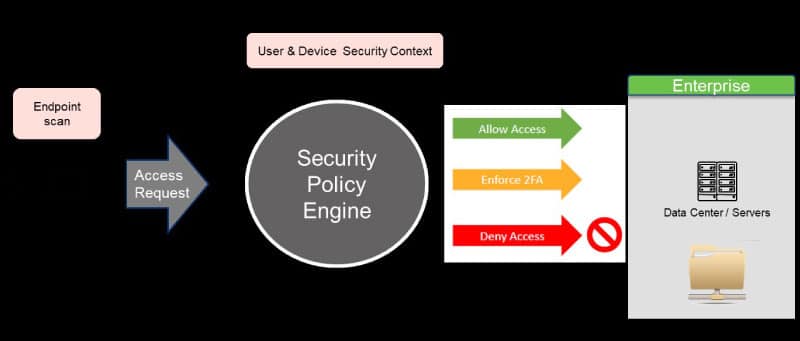
Conditional access is a very important element in the VDI security posture. It includes a contextual policy engine that runs posture checks on end points and collects details to decide access conditions. Based on enterprise policies, user access is either allowed, denied or additional authentication checks are enforced.
In addition to the above security controls, VDI also supports forensic analysis with watermarks, audit reports and analytics to provide a better security posture.
| Threats and risks | Levers |
| Data leakage |
Policies to control client drive mapping, restrict downloads, disable clipboard mapping and enable watermarks |
| Threats from malware | Enable anti-keylogger and anti-screen capture features of App Protect |
| Social engineering and identity theft | Multi-factor authentication using a combination of biometric checks and active directory credentials; support for SAML (security assertion markup language) based identity providers. Posture checks and App Protect provide added security |
| Attack surface | Single URL endpoint, TLS (transport layer security) everywhere, and advanced threat protection against attacks such as network and app DDoS |
| Lateral propagation | Network segmentation enables security policies, isolation and traffic control |
Table 1
Table 1 summarises the various levers built into VDI to seal security vulnerabilities.
Even though VDI is built with tight security levers, it is still not 100 per cent fool-proof. Human mistakes coupled with hacker intelligence can still put VDI security at risk. However, VDI does raise the security bar to a very high level, which makes it very hard to compromise it.
Disclaimer
The views expressed in this article are that of the authors and Wipro does not subscribe to their substance, veracity or truthfulness.