If you are interested in security, you have perhaps used Lynis for auditing your machines’ security status. For those of you who don’t know what Lynis is, it is a free, open source and extensible security auditing tool, used by many security auditors across the world. Security specialists, network administrators and penetration testers are all the intended users for this tool. With Lynis, you can add your own custom test. This article shows you how.
As many of you might agree, it would be great to have a tool that audits the entire computing system and in all possible ways to give us a detailed report on it. The developers of Lynis, realising this need, have developed this great tool for us. Lynis already comes with a lot of tests by default but it may not have all the tests that may be specifically required by a user. It is currently capable of doing penetration testing, security auditing, vulnerability detection, system hardening, and compliance testing.
Now let us see how Lynis is better than other tools in the market. First, it is open source. Though there are other tools which audit systems but the main advantage of Lynis is that it is a wholesome tool, that is, it has many other functionalities apart from auditing.
So, now let us discuss how one can add one’s own test to Lynis.
First, install Lynis as follows:
sudo apt-get install lynis |
Performing a basic audit
We can perform a basic audit to check if Lynis is working, by using the following command:
lynis audit system --quick |
With this instruction, Lynis performs all basic tests and gives us details like how many tests are included in this, as well as the hardening index of our operating system (as shown in Figure 1).
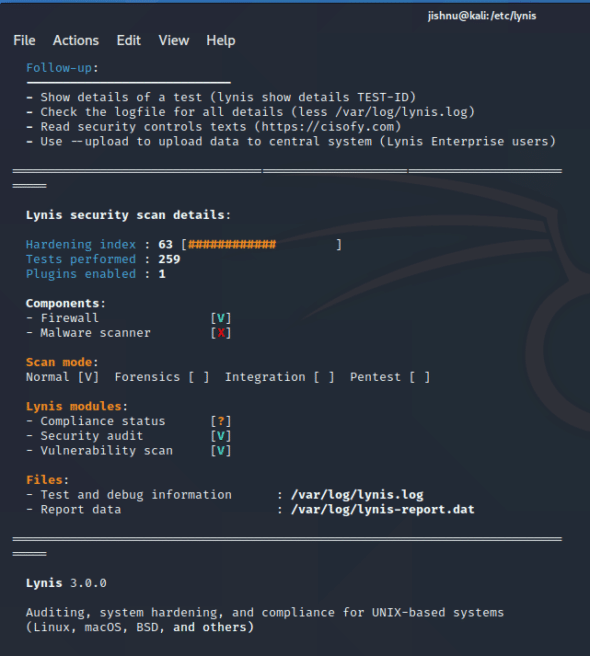
Adding your own script to Lynis
Let us now move on to the main aim of this article, i.e., to create one’s own Lynis script. It indeed is very exciting to add one’s own script to such a famous tool and is an easy procedure too.
First, we have to navigate to /usr/share/lynis/include. Here, you will find a file named tests_custom.template. This is a basic template in which one’s script should be carried. This file is then copied with the same file name without the extensions template. We then move on to the custom tests section (as shown in Figure 2).
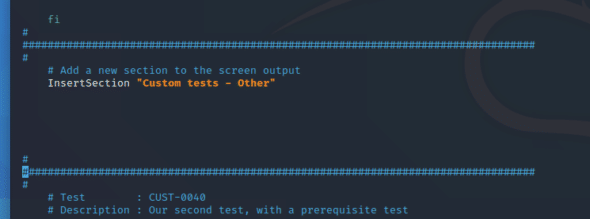
Add the script given here below the ‘Insert section’ line; in this case I have written the script to check if the cron job scheduler is up and running properly or not. The script is given below.
1 2 3 4 5 6 7 8 9 | ## Add a new section to the screen outputInsertSection “Custom tests - Other”Register --test-no CUST-1313 --weight L --network NO --description “test to check if mysql is running”STATUS=”$(systemctl is-active cron.service)”if [ “${STATUS}” = “active” ]; thenecho “The cron job scheduler service is running properly.”elseecho “The cron job scheduler service is not running.”fi |
We then run the Lynis audit again using the command that we have already seen, lynis audit system –quick and get the output of the newly written test in the custom tests section (see Figure 3).
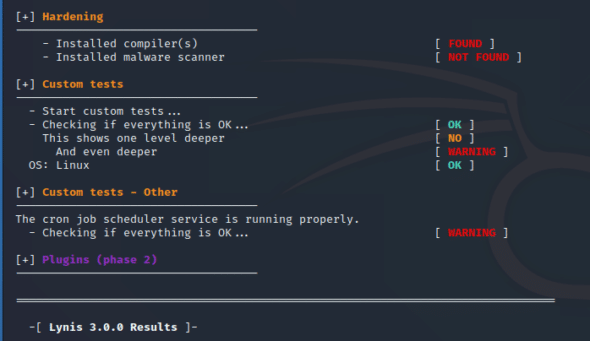
So, from this output we can infer that the cron job scheduler service is working properly.
Do give it a try.
If you want to learn more about the security of your system, check out the official documentation of Lynis. You can have great fun learning about the vulnerabilities and the security of a system. The deeper we dig in, the more fun it is. The main aim of this article is to show you how easy and exciting information and cyber security auditing can be.















































































