If you are interested in security, you may have already used Snort for checking your machine’s security status. Snort is a free and open source intrusion detection and prevention tool, used by many safety analysts, network administrators and penetration testers across the globe. This article will tell you how to add your own rules to Snort in order to detect specific security attacks.
As many of you will agree, it would be great to have a tool that checks the entire system in all possible ways and tells us if there is a security attack taking place. The developers of Snort felt the same and have developed this great tool for us. Snort comes with a lot of rules to help check and detect attacks by default, but it may not have all the rules that may be specifically required by a particular user. So, let us see how we can add our own rules to Snort and check for attacks.
Install Snort
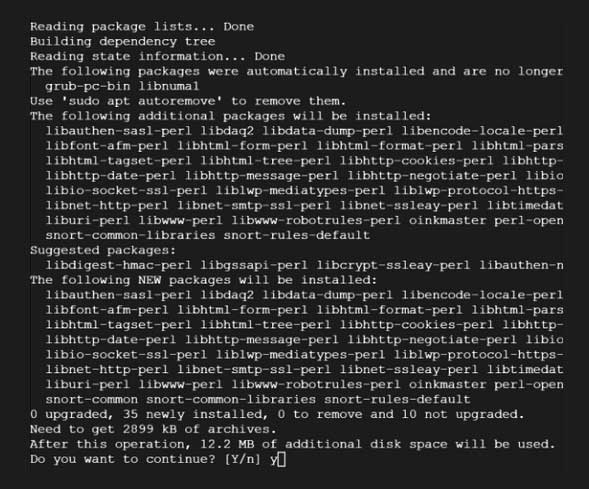
For installing Snort, just open a terminal and enter the following command:
1 | sudo apt-get install snort |
It will then ask you for an interface. It will give you eth0 by default; just remove it and leave it blank, and press Enter. For all the other details it asks, leave them as default and press Enter. Snort is now installed.
Perform a basic Snort test
Enter the following command to perform a basic Snort test with the rules that are given by default:
snort -c /etc/snort/snort.conf -l /var/log/snort/ |
You will be able to see all the rules that are applied and all the tests it has performed.
Add your own rules to Snort
Let us now move on to the real aim of this article, i.e., to create your own Snort rules. It sounds really exciting to add your own rules to such a famous tool right? Yes, it indeed is very exciting and also very easy.
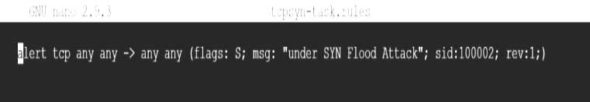
First, navigate to /etc/snort. Then, create a rule file with the extension .rules, and add your rule to the file with all the features you need to test for the attack you want to check for. Save the file. As an example, here is a rule to check a TCP SYN attack (Figure 3), which is named tcpsyn-task.rules. The flag is set to S as the intention is to detect SYN packets from an outside network to any port on your home network. If it does detect a packet, it gives a message in the Alerts file that the system is ‘under SYN flood attack’.
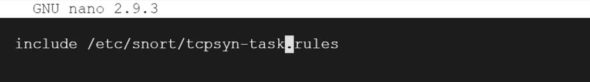
Now you have to include this rule in the Snort configuration file.
So, in the same location of your rules file, find a file named snort.conf. Open it using any editor, add the following line, and save it.
include /etc/snort/tcpsyn-task.rules |
Once you are done with this, your rule has been added to Snort. You then run the snort command along with your newly added rule. For this, you run the following command:
sudo snort -v--c /etc/snort/snort-test.conf |
Check your alert message in the log information
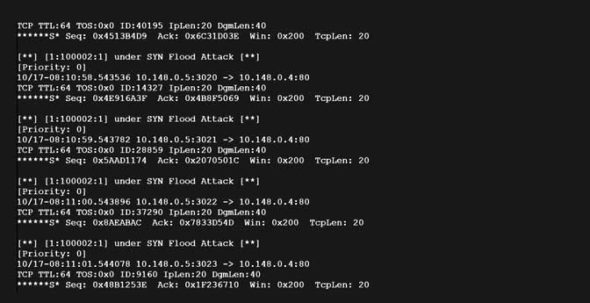
Just run the following command to check the output:
tail -f /var/log/snort/alert |
If the alert message that you have given comes up, it means the attack has taken place; otherwise, it hasn’t. To show the output, I have generated the attack from another machine of mine. From this output we can infer that a TCP SYN attack has taken place.
Do give it a try!
If you want to learn more about the security of your system, do check out the official documentation of Snort. Learning about the security of your system can be a lot of fun. The deeper you go, the more interesting it gets. The main aim of this article is to give you an idea of how easy and how much fun cyber security can be.




