Web applications have the potential to reach a wider spectrum of users in comparison to desktop apps, and hence have become a popular platform to render various services. However, the security of these applications needs to be ensured for people to feel confident enough to use them for sensitive tasks such as financial transactions. This article introduces readers to five tools associated with Web application security—Grabber, w3af, Zed Attack Proxy, sqlmap and Wapiti.
Web applications simplify the process of delivering online services to a wide range of users, and do so effectively. In comparison to their desktop counterparts, Web applications have various advantages. Some of them are listed below:
Web applications don’t require any installation on the user’s machine.
- The hardware requirement of the Web applications is also very minimal. As they run inside a browser, Web apps are generally platform-neutral.
- In the case of desktop applications, one of the major problems is updating to the latest version. As Web apps are not locally installed, users do not need to update them.
Due to these advantages, Web applications have emerged as a popular mode of delivering services. However, security is one of the critical aspects to concentrate on in this scenario. Compared to desktop apps, the security for Web applications is more critical as they are vulnerable to all kinds of online attacks.

There are plenty of tools to analyse the security of Web applications. This article provides an introduction to the following open source security tools associated with Web applications:
- Grabber
- w3af
- Zed Attack Proxy
- sqlmap
- Wapiti
Grabber
Grabber is a scanner for Web applications. It is a simple tool that locates vulnerabilities in a Web application. The following is a list of all that Grabber can handle:
- Cross-site scripting
- SQL injection
- File inclusion
- Preliminary AJAX checking
- JavaScript source code analysis
Grabber can be downloaded from http://rgaucher.info/beta/grabber/Grabber.zip.
After the installation process, it can be executed as follows:
$ python grabber.py --spider 1 --sql --xss --url http://127.0.0.1/bank
Otherwise, the parameters can be configured through a configuration file, as shown below:
<grabber version=”0.1”> <site> <url> http://127.0.0.1/bank </url> <spider> 1 </spider> <!-- Depth of the spider --> <scan> <xss /> <sql /> </scan> </site> </grabber>
Grabber is designed to scan websites that have just a few pages (small sites). If you try to use Grabber for larger sites, it will take a long time to complete a scan.
w3af
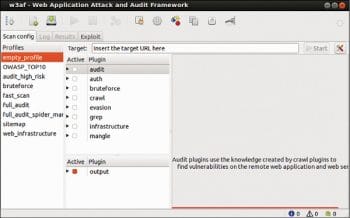
w3af (Web Application Attack and Audit Framework) is popular for auditing attacks on Web applications. This framework deals with the vulnerabilities of Web apps. w3af has been developed using Python. It is relatively simple to use and very extensible. It identifies vulnerabilities in a Web app by sending customised HTTP requests to it. It has been released under the GPLv2.0 licence.
The process with which w3af identifies vulnerabilities is listed below:
- Locates all links, forms and query string parameters
- Sends customised requests to each input and analyses the output
- Generates report with the findings
The simplest way to install w3af in Kali Linux is as follows:
apt-get update apt-get install -y w3af
For detailed installation instructions across various platforms, you can refer to http://docs.w3af.org/en/latest/install.html.
w3af has three main plugins, which are listed below:
- Crawl plugin: To find new URLs and injection points
- Audit plugin: To send specially crafted data to the injection points identified by the crawl plugin
- Attack plugin: To exploit the vulnerabilities identified by the audit plugin
w3af can be executed in two modes — console mode and GUI mode with the following commands:
$ ./w3af_console w3af >>> $ ./w3af_gui
Scanning can be started after configuring all the required plugins, as follows:
w3af>>> target w3af/config:target>>> set target http://localhost/ w3af/config:target>>> back w3af>>> w3af>>> start
As stated earlier, the scanning can be done via the GUI as well. A sample screenshot from the official documentation is shown in Figure 2.
An easy way to get familiar with w3af is to go through the project tour videos provided at the official documentation site (http://w3af.org/take-a-tour). A demo to identify and deal with the SQL injection is provided. Detailed documentation on how to use the various features of w3af is provided at http://docs.w3af.org/en/latest/index.html.
Zed Attack Proxy (ZAP)
Zed Attack Proxy (ZAP) is a popular, free and open source penetration testing tool. It is maintained by the Open Web Application Security Project (OWASP). The primary objective of ZAP is security testing of Web applications.
ZAP sits in between the browser and the Web application. In this way it can intercept and inspect messages sent between the browser and Web app. It can modify the contents if required. These modified contents can then be forwarded. ZAP can be used as a standalone application or as a daemon process.
ZAP can be installed in all the popular operating systems such as Linux, MacOS and Windows. You can select the appropriate installer from the download section of the official site at https://www.zaproxy.org/download/. To run ZAP you require Java version 8+ on your system.
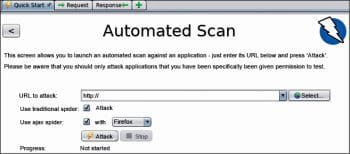
The simplest way to use ZAP is to use the automated scan available under the Quick Start tab, as shown in Figure 3.
ZAP is highly extensible. It has a marketplace where additional add-ons can be downloaded (https://www.zaproxy.org/addons/ ).
Apart from this graphical user interface, ZAP has a very powerful API that enables you to do almost everything that can be done via the GUI. Detailed instructions on using the ZAP API are available at https://www.zaproxy.org/docs/api/#introduction.
sqlmap
sqlmap is a penetration testing tool. It is used for automating the detection of SQL injection. sqlmap supports plenty of databases such as MySQL, Oracle, Microsoft SQL server, etc (the full list is at http://sqlmap.org/ ). sqlmap can handle the following six types of SQL injection techniques:
- Boolean-based blind
- Error-based blind
- UNION query-based
- Time-based blind
- Stacked queries
- Out-of-band
sqlmap can be downloaded from https://github.com/sqlmapproject/sqlmap/tarball/master.
Wapiti
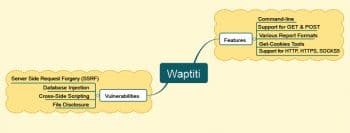
Wapiti (https://wapiti.sourceforge.io/) is an open source tool to audit the security of Web applications and websites. Wapiti carries out black-box scans of Web applications. It crawls the Web pages and then injects payloads to check for vulnerabilities. The current stable version of Wapiti is 3.0.3, which was released on February 20, 2020. Wapiti has the potential to scan many vulnerabilities, a few of which are listed below:
- Database injection
- Cross-site scripting
- File disclosure
- Server side request forgery (SSRF)
- Bypassing weak .htaccess configurations
Wapiti is a command line application. It can be downloaded from https://sourceforge.net/projects/wapiti/files/.
Wapiti has support for both GET and POST methods of HTTP for attacks. It can generate vulnerability reports in various formats such as HTML, JSON, XML, Plaintext, etc. It can be configured to work with different levels of verbosity. Adding payload in Wapiti is very simple.
Wapiti has another interesting feature called getcookie (the wapiti-getcookie tool). This can be used to import cookies. Wapiti can extract URLs from JavaScript and handle HTML 5 tags as well.
Wapiti has support for HTTP, HTTPS and SOCKS5 proxies. It has various options to control the behaviour of crawlers. It also has features to set the maximum time for scanning.
The simplest way to invoke Wapiti to perform a scan is shown below:
wapiti -u http://target/
This article gives a brief on five open source tools associated with the security of Web applications. There are many more tools available for similar tasks but covering all of them would not be viable here. If you are new to the Web application security domain, you can start with any of these tools, and explore further to acquire better insights into how to make Web applications more secure.