Disk encryption is a technology that converts any data into unreadable code and stores it on a device like a hard disk. The unreadable code is decrypted using a key that converts it back to readable data. This process of encrypting and decrypting data on a storage device helps to protect sensitive data from unauthorised access. There are many disk encryption software available online, a number of which are free and open source. Cryptomator is one of them.
Cryptomator (https://cryptomator.org/) is disk encryption software that allows users to encrypt any data for protection, but it is different from other such software. This software can encrypt data and store it on various cloud storage networks like Dropbox and Google Drive. Cryptomator was created by a company called Skymatic GmbH (Germany) in 2016, and is licensed under GPLv3 as FOSS.
Minimum system requirements
The Cryptomator client can run on any desktop PC, laptop or smartphone. In order to use the latest version of the client software on a desktop PC or laptop, you must have one of the supported operating systems, which include Windows 7, 8 and10; MacOS 10.11, 10.12, 10.13, 10.14 and 10.15, as well as TODO Linux. Cryptomator supports Android 4.3 and iOS 10.0 on smartphones, and is also compatible with iPad and iPod Touch. It requires Java 9 or a newer version to run on any system properly.
Features
Listed below are some of the key features of this software.
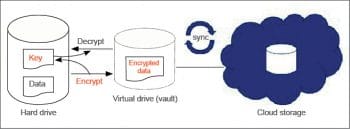
Transparent encryption: With this type of encryption, you will not notice any difference when working with your files. Cryptomator creates a virtual hard drive, which gets synchronised with the encrypted data on cloud storage, and that data can easily be accessed using the virtual drive. You can work on this drive just as you would on a USB Flash drive, though the data will be encrypted and stored somewhere on the cloud – for example, on Google Drive.
Individual file encryption: With Cryptomator, everything you put on the virtual hard drive is encrypted individually in the vault. Compared to other disk encryption utilities, Cryptomator encrypts each file individually, and if you make any change to a file in your vault then that file is only encrypted after being changed. In this way, the synchronisation client of your cloud storage provider knows exactly what needs to be uploaded and what doesn’t.
Ease of use and reliability: The simplicity and ease of use is the key feature of Cryptomator. With it, you don’t have to deal with accounts, key management, cloud access grants or cipher configurations. Just with a password, one can use the vault and store data on any cloud. Users are not required to specify which cloud network to use. Cryptomator uses transparent data encryption and makes it very easy to store data on any cloud. It encrypts files and doesn’t care where you store them. This makes it a lightweight application that is easy to run on any computer or smartphone, reliably. Cryptomator also has a feature called Sanitizer, with which it is possible to scan for any corrupted files in the vault. This feature helps troubleshoot any error and makes Cryptomator more reliable in terms of data protection.
Functionality
Cryptomator creates a virtual drive (vault) to add, edit, and remove files, as is the case with just about any disk drive. Files are encrypted using a method called Transparent Data Encryption (TDE). The encrypted data is converted to unreadable code before storing it on the cloud, and no unencrypted copies are stored on the hard drive. For every encryption, a master key is created and stored separately. The encrypted files are decrypted and converted back to readable format using the master key. Every time your files are accessed inside the virtual drive, Cryptomator will encrypt/decrypt them on-the-fly.
Currently, Dokany (on Windows) and FUSE (on MacOS and Linux) are the frontends of choice. If they are not available on your system, Cryptomator will fall back on WebDAV, as it is supported on every major operating system. WebDAV is an HTTP based protocol, and Cryptomator will act as a WebDAV server accepting so-called loopback connections on your computer.
Whenever your file manager accesses files through this virtual drive, Cryptomator will process this request via the following six layers of encryption and storage methods.
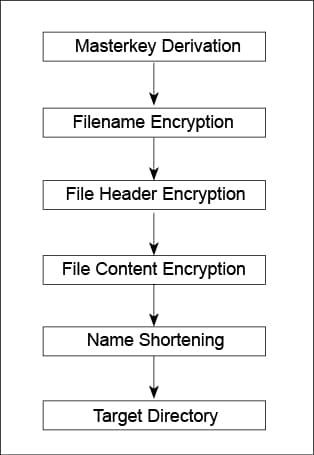
Master key derivation: This is the first layer of encryption and here, the master key is created for the file that is being stored in the vault. Every vault has its own 256-bit encryption key, and both the keys are encrypted using RFC 3394 key wrapping with a KEK derived from the user’s password, using Scrypt. The encrypted keys are stored as integers or Base64 strings in a JSON file named masterkey.cryptomator, which is located in the root directory of the vault. When unlocking a vault, the KEK is used to unwrap (i.e., decrypt) the stored master keys.
File name encryption: In this layer, the file and directory names are first encrypted before storing. Initially, each folder gets a unique identifier called the directory ID. The directory ID for the root folder is special and always empty. For all other folders a UUID is created. Cryptomator uses AES-SIV to encrypt files as well as directory names and associates according to the ID.
File header encryption: In this layer, the file header stores certain metadata, which is needed for file content encryption. It consists of 88 bytes:
- 16 byte nonce used during header payload encryption
- 40 byte AES-CTR encrypted payload that includes 8 bytes filled with one for future use (formerly used for the file size) and 32 byte file content key
- 32 byte header MAC of the previous 56 bytes
File content encryption: This is where the actual file contents get encrypted. The cleartext is broken down into multiple chunks, each up to 32KB + 48 bytes consisting of:
- Up to 32KB encrypted payload using AES-CTR with the file content key
- 16 byte nonce
- 32 byte MAC of file header nonce (to bind this chunk to the file header)
- Chunk number as 8 byte big endian integer (to prevent undetected reordering)
- Nonce
- Encrypted payload
Afterwards, the encrypted chunks are joined, preserving the order of the cleartext chunks. The payload of the last chunk may be smaller than 32KB.
Name shortening: This layer doesn’t modify any file contents but it limits the path length to ensure compatibility with certain Microsoft products that do not support long paths. Even with the flattened directory structure achieved during file name encryption, the file path might be longer than 255 characters. If a ciphertext file name exceeds the threshold of 129 characters, it is replaced by its much shorter SHA-1 hash and gets a .lng file extension. Additionally, a similarly named metadata file is created in the ‘m’ directory containing a reverse-mapping back to the original name. This layer doesn’t provide any additional security but the main purpose is to maximise compatibility.
Target directory: This is the final layer. After the files have been processed by all the above layers, they are finally stored into the chosen directory. This is where Cryptomator’s final job is done, and lastly, the files are synchronised with the cloud storage.
| Pros | Cons |
| Free to use | No sharing functionality |
| Open source and can be modified | No contact options |
| Easy to use | |
| Can be used on smartphones also | |
| Community support available | |
| Online documentation |
Effectiveness
Cryptomator is a very useful disk encryption FOSS and it can be easily installed on many types of operating systems, running on a desktop PC or laptop, for free. It can also be used on a smartphone using an Android/iOS app and one can also back up data stored on the smartphone to the cloud. However, the Cryptomator apps for smartphones are not free to download.
Cryptomator uses transparent encryption to store data on the cloud and this makes it more secure. It also becomes easy to store data online, because it’s compatible with most online cloud storage services like Google Drive and Dropbox.
The password used for the Cryptomator vault is not shared online and remains a local password. This makes it more reliable and prevents the chances of online hacking. The encryption used by Cryptomator is also well secured, and it not only encrypts the data but also the encryption keys, for security. Cryptomator does the encryption and decryption of data, on the fly; that’s why it is very effective in terms of security and performance. Moreover, as it is FOSS, it is free of any backdoor or malware issues and can be trusted as reliable software. It uses the Advanced Encryption Standard (AES) method to encrypt the data and the passphrase is protected against brute-force attacks using Scrypt – a password-based key derivation function.
Ease of use
Cryptomator is surprisingly very easy to use, unlike many open source software that are difficult to use. It can be easily downloaded from the site https://cryptomator.org/downloads/#winDownload and can be installed on a desktop PC or laptop for free. However, Cryptomator has the option for donation on its site, and its smartphone apps can be downloaded from the app store by paying online. Cryptomator supports many operating systems like Windows, MacOS, Linux, Android and iOS. That’s why it’s very convenient to run Cryptomator on any computer or smartphone.
The user interface (UI) of Cryptomator is properly designed, with its components well organised, making it very easy to use both on a computer and a smartphone. Cryptomator also has an online support system for troubleshooting, so anyone can get help regarding any problem related to this software. The documentation on the terms of use can be found at https://docs.cryptomator.org/en/latest/.
Even though Cryptomator has a few drawbacks, it still beats many other disk encryption FOSS, in terms of functionality and security. Most disk encryption software store encrypted data locally on a hard drive, but Cryptomator makes it possible to store encrypted data on the cloud, easily and reliably. With the help of this disk encryption FOSS, we can store sensitive data on any cloud storage service like Google Drive and Dropbox, without any difficulty.