There is a growing need to use technology to mark the attendance of students in the classroom – a process that is both automatic as well as efficient. In recent years, the problem of attendance management has been addressed through the use of standard biometrics like fingerprint or iris scanners. However, most proposed technologies are not too reliable. One solution is the intelligent application of facial recognition techniques iteratively. This article discusses an automated attendance management system that uses facial recognition.
Facial recognition comes under the category of biometric technologies like fingerprint and iris scanning. Facial recognition is capable of identifying a person from an image or from a video source. It is one of the best and simplest biometric technologies as it uses the facial features of the person only for identification. The main advantage of facial recognition compared to other biometric techniques is that it requires no contact as it captures the images of the person from a distance. This technology is being used by a lot of mobile companies, as well, as a secure yet password-less way to lock smartphones. Oneplus 5T and Apple iPhone X are examples of smartphones that use facial recognition technology.
Face recognition can be used for many other purposes too, such as recording the attendance of students in colleges or schools, marking the presence of employees in companies, etc. In this article, we will mainly focus on using facial recognition for an attendance system.
The attendance system is widely used all over the world for various purposes and across diverse domains such as offices, schools, universities, etc. Marking the attendance of students in a classroom not only takes some effort but is also time consuming. Also, proxy attendance is always a possibility in classrooms where the number of students is large, making it difficult for the faculty members to track the students who skip lectures.
Traditional methods of tracking the attendance of students are tedious. Conventionally, the teacher calls out the names of individual students who are supposed to be attending the class, and those present in the room respond; or the teacher passes around an attendance sheet for students to mark their attendance — both manual processes involve pen and paper and are not efficient.
Most educational institutions are concerned about their students’ attendance at courses. Proper participation of students in the classroom leads to effective learning and increases success rates. With the advent of face recognition, numerous techniques have been incorporated in attendance management systems.
The various technologies used to take attendance
Students’ attendance using RFID tags: RFID stands for ‘radio frequency and identification’. RFID methods use radio waves to accomplish this. At a simple level, RFID systems consist of three components — an RFID tag or smart label, an RFID reader and an antenna. The job of the reader is to convert radio waves to some usable form of data. Information that is collected from these tags is transferred through a communications interface to a host computer system, where the data can be stored in a database and analysed later. The RFID device serves the same purpose as a bar code or a magnetic strip on the back of a credit card or ATM card. Just as a barcode needs to be scanned to get the information, similarly, the RFID device must be scanned to retrieve the data. Each student is required to have her/his student RFID card with them when entering the classroom. The back-end data is managed by custom software.
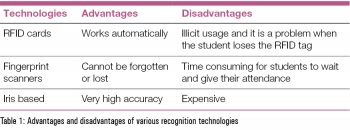 RFID has a lot of advantages – it can store more information as compared to bar codes and it can provide locations to the reader along with the ID. These tags can be both read-only and read/write (so the tags can be reused). RFID’s several disadvantages include that it requires a battery, privacy is always an issue as users can be easily tracked, and its coverage range is limited to only 3 metres.
RFID has a lot of advantages – it can store more information as compared to bar codes and it can provide locations to the reader along with the ID. These tags can be both read-only and read/write (so the tags can be reused). RFID’s several disadvantages include that it requires a battery, privacy is always an issue as users can be easily tracked, and its coverage range is limited to only 3 metres.
Fingerprint attendance management system: The fingerprint system for attendance or for logging people’s movements is widely used across the globe. This type of system has various advantages. Since humans’ finger prints are unique, tracking them based on this is a highly secure and accurate system. But this type of system has many disadvantages too, such as the need for a fingerprint sensor to be placed in a location where there is proper wireless network connectivity. It is also much slower than many other approaches. Distortions caused by the glass layer on the sensor often lead to wrong results, which then require one to place one’s finger repeatedly on the sensor to get proper results. This process is also very time consuming, as each student has to wait for his/her turn.
Iris based attendance system: This system uses technology that captures the image of the iris and checks to see if it matches with the data stored. Iris recognition is one of the most secure methods of recognition that can be used. It is easy, accurate, stable and has great scalability. It also offers the best privacy. But the difficulty occurs in laying transmission lines in places where the topography is challenging. This method also demands expensive hardware, which may not be viable for an attendance system. Since the iris is small, it is difficult to detect it from a certain distance. So the system needs to be set up in a place where people can approach it easily. Besides, the constant use of this scanner might affect one’s eyes as it uses infrared light to detect the iris in the dark. Sometimes, it gets difficult to scan the iris if there is too much reflection.
The different methods that can be used to set up an attendance system
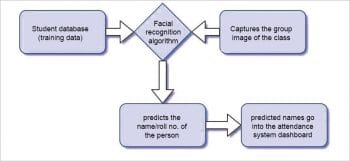
Approach 1: In this approach, the student database, which contains images of students, is used as the training data for the face recognition algorithm.
A series of group images of the whole class is given as the input to the facial recognition algorithm, which outputs an Excel sheet with the names/roll numbers of the students present in the group photo. The drawback of this approach is that it is difficult to capture the group image of a class with a large strength.
Another major drawback is that all the students may not be looking at the camera while the image is captured and there is also a chance that a person sitting in a front row may cover the person sitting in the row behind. So, to overcome these drawbacks, we came up with a new approach.
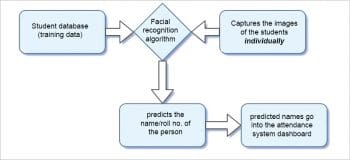
Approach 2: In this approach, we used the student photo ID database as the training data. We captured the images of students individually while they were entering the classroom and stored them in a folder. We gave this folder as input to the facial recognition algorithm, which then responded with the result in the same way as in the previous example.
The major drawback of this approach is the inadequate memory to store the captured individual images of the students. Storing these images on an online database is also not feasible as searching and retrieving the data could be time consuming.
So we proposed another solution — a real-time facial recognition system for the attendance system which addresses the disadvantages mentioned in different ways.

Implementation
Step-by-step process for any facial recognition process: The major steps in any facial recognition process are to:
- find the face of the person in the image;
- analyse the facial features of the person;
- compare the analysed features of the persons with the known faces; and
- predict the name of the person based on the above comparisons.
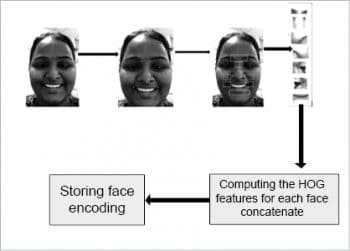
This process uses a Python package named ‘face recognition’, which implements the ‘history of oriented gradient’ (HOG) algorithm. Figure 3 is the diagrammatic representation of the HOG feature extraction and face encodings.
An overview of how the HOG algorithm works is given below.
- To find the faces in the image, the algorithm starts by converting the image into monochrome because colour data is unnecessary for further processing.
- It considers each pixel at a time and checks the pixels that connect directly with (surround) the selected pixel.
- It figures out how dark the selected pixel is compared with pixels immediately surrounding it.
- Based on this, an arrow represents the direction in which the image is darker.
- After repeating this process for every pixel in the image, we end up getting an arrow in every pixel.
- These arrows are called gradients, which represent the flow from light to dark in the whole image.
The image contains a large number of pixels. Saving the gradient for every pixel is way too much detail to process. To get a higher-level basic flow of dark and light, this method breaks the image into small squares of 16×16 pixels each. In each square, the gradients that point in each major direction are counted (how many point upwards, up-right, right, etc). This square in the image is replaced with an arrow in the direction that is found to be strongest.
This encoding is done for all the images in the database (images used for training). So, whenever a face is detected, it is compared with the known encoding, and the system then gives the name or roll number of the person. The given output, i.e., name or roll number, is the file name of the identified person in the known images.
Overall, the system is implemented in the Python language.
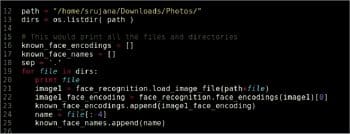
We used the images in the student database as the training data. In the snippet of code in Figure 4, lines 16 and 17 are the variable declarations of two lists for storing the face encoding of all the images of the students and their corresponding names in the database. From lines 21 to 25, each image is loaded and the corresponding encoding is stored in the list known_face_encodings.
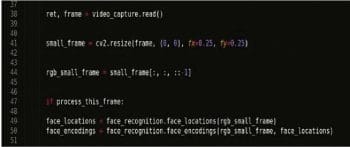
After storing the face encoding of the training data, the code from lines 39 to 44 in Figure 5 triggers the camera for the real-time capture of the faces of the students. The algorithm processes each frame of the video, and starts storing the encoding of each face present within the frame (lines 47 to 50).
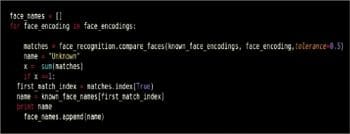
Later, it compares the encoding of each face in the frame with the encoding of the faces stored in the list known_face_encodings. If the encoding of the face in the frame matches with a known encoding, the system outputs the name of the file that matches the encoding (from lines 53 to 62 in Figure 6).
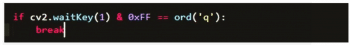
If it doesn’t match with any encoding, then the system outputs the name as ‘unknown’. Real-time capturing of images stops as soon as we press the button ‘q’, as shown in Figure 7.
As real-time capturing stops, the predicted names of the images stored in the list that has been ‘outputted’ are then displayed on the dashboard of the attendance management system.
Results
The images of students in the student database that are used as the training data for the algorithm can be seen in Figure 8.
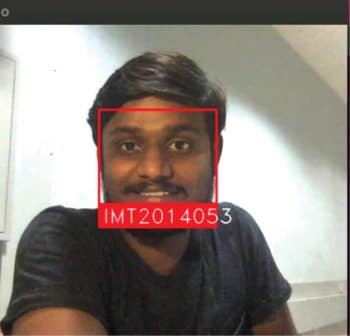
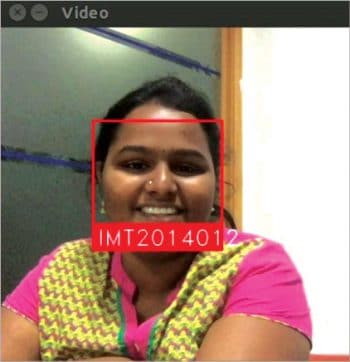
When we run the code, the real-time capturing of the faces of the students starts. Now, when a person comes in front of the camera, the system detects the face and displays the name of the person if the image of the person is in the student database; otherwise, it displays the message, ‘Unknown’.
For real-time capture, we have used the PlayStation eye camera which is capable of capturing standard video with frame rates of 60Hz at a 640×480-pixel resolution, and 120Hz at 320×240 pixel resolution.
We have repeated these results multiple times to check the accuracy and, every time, the application is able to identify the person’s credentials correctly.
To summarise, we have implemented an attendance system using facial recognition, which marks the presence of the students in a class automatically and with no manual effort.
This can be a Web development project, for maintaining training data in an online database. Facial recognition can also be used to identify criminals, if sufficient information is available.