Given the ever present threat of malware and intrusion attacks, the safety of systems depends on having reliable firewalls to protect them. This article offers an instant guide to Firewall Builder, which is regarded as a significant firewall configuration and management tool.
For network security, systems and network administrators have umpteen choices with regard to firewall and network intrusion detection systems – both open source and commercial options. They can make use of utilities like iptables/Netfilter on Linux; ipfilter/ opfw on OpenBSD and even Cisco PIX and other commercial options via Sophos. All these firewalls provide strong security solutions to filter all sorts of threats and exploits coming from the outside world. Managing security policies becomes quite challenging as configuration options are complex and have many sub-features, which puts a lot of stress on systems administrators.
With experience, network administrators become experts in what they’ve chosen, but to achieve 100 per cent security, they need to understand the internal path of a packet inside Linux and its interaction with different parts of packet filtering systems. Things become even more complicated and challenging when administrators switch the security systems from one software or hardware to another, and this could even lead to misconfiguration, errors or security mishaps. So, to overcome this problem, systems administrators require to build self-customised firewalls, easy enough to configure security options and flexible enough to change with the passage of time, depending on the security requirements.
An introduction to Firewall Builder
Firewall Builder, also known as fwbuilder, is a universal GUI based firewall configuration and management tool that supports iptables (Netfilter), ipfilter, pf, ipfw, Cisco PIX and CISCO routers’ extended access lists, allowing network and sysadmins managing bigger networks or hobbyists managing home based networks to simplify management tasks. Firewall Builder runs on many popular operating systems including Red Hat, Mandrake, SUSE, FreeBSD, MacOS X and even Windows.
Firewall Builder provides a high level of abstraction and hides the internal structure of the target firewall platform. For example, it can decide which iptables chain is right for each generated iptables rule, automatically, without your input. It can pick the right iptables target for both policy and NAT (Network Address Translation) rules as well as properly use most popular iptables modules, all automatically. Firewall Builder generates correct PIX translation rules, choosing between ‘nat’, ‘global’ and ‘static’ commands as appropriate, using the same definition of the NAT rules as it uses for iptables and PF. It enforces best practices in policy design and assists sysadmins in deploying and activating the generated policy on the firewall.
Policy and NAT rules built in Firewall Builder will look very familiar to anyone who ever worked with Firewall-1, PIX, iptables, PF and so on. This is because these rules are just generalisations of the ideas and features found in all of those firewalls. The program helps you create and manage rule sets and then translates them into the configuration language of the chosen target firewall platform.
Firewall Builder is more complex than many basic firewall configuration GUIs such as Firestarter, but on the other hand, one can build very complex policies with it and fully use the flexibility and power of iptables and other supported firewalls. Firewall Builder works well both as a configuration tool for the local firewall protecting machine where fwbuilder is running and as a firewall configuration UI that manages configuration on several remote dedicated firewalls and routers.
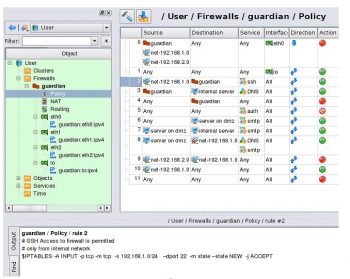
Fwbuilder allows for the simultaneous management of multiple firewalls on many servers. Programming components called policy compilers facilitate fine tuning of firewall policy rules without the need for the administrator to remember all of the details for each firewall or server. The policy compilers also ensure that firewalls are ‘sane’— that there are no contradictions or errors that will interfere with the intended and legitimate use of the network by its subscribers.
How Firewall Builder works
Firewall Builder GUI provides a simple and easy interface to build a customised firewall. The systems administrator can create and manage collections of objects that define network addresses, hosts, firewalls, services and design policies as well as NAT rules using these objects.
The process involves the following five steps.
1. Creating the firewall: Firewall Builder lets the user define all sorts of settings like the type of platform, software version and interfaces. When a user clicks on the ‘Create New Firewall’ button, a wizard based interface follows to let the user configure the following:
- The firewall’s name
- Software on which the firewall is based (like Cisco Pix or iptables)
- Operating system on which the firewall will execute
- Select from pre-configured firewall templates
- Select Ethernet interfaces, etc.
2. Defining objects: Firewall Builder enables admins to create objects for network elements, for use in firewall rules. It comes preconfigured with hundreds of commonly used objects.
Firewall Builder stores objects in what are known as libraries. By default, it includes the following two libraries.
- Standard: The predefined objects that can be dragged and dropped into firewalls. These objects cannot be edited.
- User: An empty pre-categorised library to which users can add their own objects and then drag and drop them into firewalls.
The following are the types of objects in Firewall Builder.
- Address ranges: A range of addresses can be configured into a single object.
- Address tables: This is an address-based object that can be created when a range of addresses is needed, but the actual addresses are not known when the firewall or policy is being written. The address tables object has an added feature that allows for the object to be loaded at either compile time (during firewall compilation) or during run time (when Firewall Builder runs the firewall script).
- Address: A single address that can be used for an interface, source or destination (such as a host).
- DNS names: This object represents a DNS ‘A’ or ‘AAAA’ name, and resolves to an IP address during either compile or run time.
- Groups: A group is a container that holds references to multiple objects of the same or similar type (addresses, address ranges, network objects, etc).
- Hosts: A host object represents hosts on a network — desktops, workstations and any other network node that has a network address.
- Networks: This object describes an IP network or an entire subnet.
To create a new object, the following steps are required:
- Right-click the Hosts entry in the left navigation menu (under objects).
- Select ‘New Host’.
- Give the new host a name and click Next.
- Select Configure interfaces manually and click Next.
- Enter the information for the host to be configured (name, label, static IP, IP address) and click Finish.
This allows admins to create an unlimited number of hosts. The hosts are added to the object tree, and it is possible to drag and drop them into the firewall.
3. Configure policy: Firewall Builder makes use of objects defined to specify the rules of the firewall. To create a new policy on the host, expand the navigation tree for Hosts, find the desired host to be added, and drag and drop the host into the firewall.
To create a new rule, follow the steps shown below:
- Select where the new rule is to be placed in the chain.
- Right-click the rule in the chain where the new rule is to be located.
- Select either Insert New Rule or Add New Rule Below (depending upon where the new rule needs to live in the chain).
The new rule will be placed within the chain – it will be fairly generic and will deny all traffic. Obviously, this new rule must be edited.
4. Compile rules: You can convert rules into a configuration file for the firewall. After you have created a firewall object and updated the rules in its Policy object, the next step is to compile and install these rules on your firewall.
The process is very simple. After you finish building the firewall, perform the following steps:
1. Save the firewall by clicking the Save button.
2. Compile the firewall by clicking the Compile button and walking through the easy-to-use Compile Wizard.
3. Install the firewall by clicking the Install button.
As soon as the installation is complete, the firewall will run. This installation will also ensure the firewall runs upon rebooting the machine. If changes are made in the currently running firewall, it is necessary to re-compile and re-install the firewall.
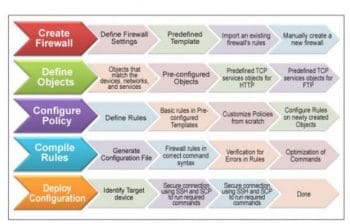
5. Deploy configuration: Install the configuration file on the firewall. Deployment is done in two steps.
- Compile. Compiling the rules converts the rules from Firewall Builder’s syntax to a file containing the command syntax used by the firewall device type and saves the output in a file. For example, compiling the rules for a firewall with the type set to iptables will generate a file that includes the rules in iptables format. After the firewall rules are compiled you can view the resulting command file generated by Firewall Builder.
- Install. Installing the firewall rules involves transmitting the file with the rules to the target device and then running that file to install the rules. The secure protocols SSH and SCP are used for this, so you will need to provide valid user credentials with the appropriate permissions on the target device.
Features
The following are the features of Firewall Builder:
- Over 100 predefined objects for the most popular and widely used protocols and services, and the capability to create custom objects describing IP, ICMP, TCP, UDP or custom services. Firewall Builder can also create objects to describe hosts, networks and address ranges.
- Powerful wizards and other tools to help you jumpstart your firewall policy, and do it right from the first try. Wizards implement standard policies for typical network layouts, which can later be extended and edited by hand.
- The network discovery tool which automates the creation of multiple objects.
- An object-oriented approach to policy management: Any change made to an object gets immediately reflected in all the policy rules of all firewalls using that object. The configuration for multiple firewalls shares the same object database.
- Generates scripts that set up interfaces, IP addresses, snmp, ntp and logging parameters and other aspects of configuring the firewall machine.
- Convenient GUI that supports standard copy/paste operations for both text strings and network objects, and allows for policy editing using the drag-and-drop feature.
- Configuring versioning control using RCS.
- Designed to manage both dedicated remote firewalls and local firewall configurations for servers, workstations and laptops.
- Supports several firewall platforms, including Cisco PIX and open source firewalls like iptables, ipfilter and pf. It has the ability to print a single object, a firewall policy, the whole hierarchy, or export it to the text file in either plain text or HTML format.
Firewall Builder hides a lot of complexity but it also hides a part of iptables’ power within itself. It is an incredibly powerful and flexible security tool that any Linux administrator should get to know. This tool is far better at creating firewalls as compared to GUI tools like Gufw and other CUI based tools like iptables.