Security is the most important parameter that people consider when selecting IT infrastructure. Read about Zeek – an open source, flexible network traffic analyser that was earlier known as Bro. It is efficient, highly stateful and comes with open interfaces. This article explores the scripting component of Zeek.
Networks render critical services to users so it is mandatory to secure them. With every passing day, the number and nature of attacks made on networks is increasing exponentially.
Zeek, earlier known as Bro, was developed by Vern Paxson and Robin Sommer along with a strong team of researchers at the International Computer Science Institute at Berkeley CA and the National Centre for Supercomputing Applications in Urbana Champaign, Illinois, USA. Zeek is the result of 20 long years of intensive research. The speciality of Zeek is that it has the best of both academia and industrial practitioners backing it.
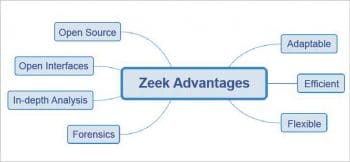
The main advantages of Zeek are shown in Figure 1.
- Adaptable: One of the prominent advantages of Zeek is that it provides a domain-specific scripting language. This makes it possible to establish site-specific security monitoring policies.
- Efficient: Zeek is aimed at providing security solutions for high-performance networks.
- Flexible: It is different from other tools in that it doesn’t depend on a specific detection approach. Another important point is that it is not dependent on traditional signatures.
- Forensics: Zeek’s comprehensive logging enables forensics.
- In-depth analysis: The analysis is provided by a variety of analysers and is hence in-depth.
- Open interfaces: Zeek provides open interfaces for exchanging real-time information.
- Open Source: It is released under the BSD licence. This makes it easier and effective to use Zeek for various scenarios.
History and architecture
The evolution of Zeek is shown in Figure 2 (you can refer to Zeek’s official documentation).
The earliest work on Zeek dates back to 1995. Over 20 years of research has made Zeek very powerful and effective. Excellent contributions by people from both academia and industry have made Zeek a robust security mechanism.
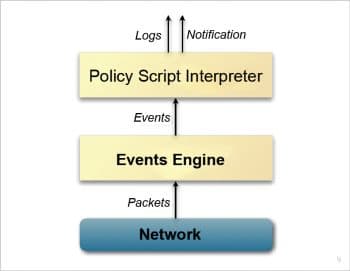
Zeek is designed with a two-layer architecture, as shown in Figure 3 (the source is official documentation).
Event engine: The first layer of Zeek is the event engine that observes the incoming packet stream and converts it into a series of events. Based on the nature of the incoming packet sequence, an event is detected. For example, if an HTTP request is raised, it converts it into an http_request event. The raised http_request incorporates the following data items along with it:
- The IP address
- The port address
- The request URI
- The HTTP version information.
The role of the event engine is to simply convert the incoming sequence into an event. The event engine doesn’t associate any interpretation to the detected event.
Script interpreter: The script interpreter receives the input from the event handler. The role of the script interpreter is to interpret the events detected by the event engine. The script interpreter executes the respective event handlers that are built in Zeek’s scripting language. Hence, the script interpreter is the most important component that enables the generation of real-time alerts.
Installation
To install Zeek in your system, the following dependencies need to be satisfied:
- Lipcap
- Open SSL libraries
- Libz
- BIND8 library
- Python 2.6 or above
Run the following command to install Zeek:
sudo apt-get install cmake make gcc g++ flex bison libpcap-dev libssl-dev python-dev swig zlib1g-dev |
Primarily, Zeek requires a UNIX platform. Support is provided for Linux, FreeBSD and MacOS X. The Linux binaries can be downloaded from the official link: https://www.zeek.org/download/index.html. (The stable release is Zeek 2.6.1, which was released in December 2018.)
In addition to the binaries, Zeek can be compiled from source as well. Detailed instructions and the dependencies list can be collected from https://docs.zeek.org/en/stable/install/install.html.
To start learning Zeek, the easiest way is to use the interactive tutorial available at http://try.zeek.org. A detailed tutorial with an extensive list of examples is available at https://www.zeek.org/documentation/tutorials/index.html.
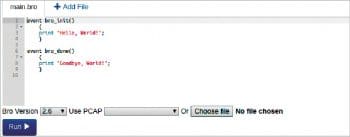
HelloWorld
try.zeek.org makes it very easy to try out Zeek’s functionalities. A screenshot of try.bro.org is shown in Figure 4.
You can simply enter the Zeek script in the code window and click on Run. You can see the output appearing in the output box.
Note that the documentation and code uses the word Bro instead of Zeek. Throughout the documentation and official website, the words Bro and Zeek are used in tandem.
event bro_init(){print “Hello, World!”;}event bro_done(){print “Goodbye, World!”;} |
As stated earlier, Zeek is event-driven. There are two Zeek events that are raised always. They are bro_init() and bro_done(). bro_init() is executed when Zeek is started and bro_done() is called when it terminates.
A code example with the function calling in Zeek script is given below:
# Function implementation.function emphasize(s: string, p: string &default = “*”): string{return p + s + p;}event bro_init(){# Function calls.print emphasize(“yes”);print emphasize(“no”, “_”);} |
A code snippet to use looping with Zeek is also shown below:
event bro_init(){for ( character in “OSFY” ){print character;}}The output of the above code is:OSFY |
A simple logging example with Bro script is as shown below. It makes two logs — one for Mod 5 and another for non-Mod 5.
@load factorialevent bro_init(){Log::create_stream(Factor::LOG, [$columns=Factor::Info, $path=”factor”]);local filter: Log::Filter = [$name=”split-mod5s”, $path_func=Factor::mod5];Log::add_filter(Factor::LOG, filter);Log::remove_filter(Factor::LOG, “default”);}event bro_done(){local numbers: vector of count = vector(1, 2, 3, 4, 5, 6, 7, 8, 9, 10);for ( n in numbers)Log::write( Factor::LOG, [$num=numbers[n],$factorial_num=Factor::factorial(numbers[n])]);} |
A code snippet to raise a notice for specific events is as shown below:
@load factorialevent bro_init(){Log::create_stream(Factor::LOG, [$columns=Factor::Info, $path=”factor”]);local filter: Log::Filter = [$name=”split-mod5s”, $path_func=Factor::mod5];Log::add_filter(Factor::LOG, filter);Log::remove_filter(Factor::LOG, “default”);}event bro_done(){local numbers: vector of count = vector(1, 2, 3, 4, 5, 6, 7, 8, 9, 10);for ( i in numbers){local result = Factor::factorial(numbers[i]);Log::write(Factor::LOG, [$num=numbers[i],$factorial_num=result]);if (result == Factor::interesting_result){NOTICE([$note=Factor::Interesting_Result,$msg = “Something happened!”,$sub = fmt(“result = %d”, result)]);}}} |
The examples illustrate the core scripting features of the Zeek script. Though the functionality coded is simple, the aim was to showcase the abilities of Zeek such as writing logs, scanning and raising notices for interesting events.
Zeek frameworks
Zeek provides many frameworks. These enable us to perform specific tasks easily and effectively. The Zeek frameworks are listed below:
- Configuration framework
- File analysis
- Geo-location
- Input framework
- Logging framework
- NetControl framework
- Notice framework
- Signature framework
- Summary statistics
- Cluster framework
Covering all these frameworks is not possible due to space constraints. The Intel framework that is used along with Zeek can be used to perform interesting tasks. One such example is shown below:
@load frameworks/intel/seenredef Intel::read_files += {fmt(“%s/intel-1.dat”, @DIR)};ntel-1.dat consists of the following:www.reddit.com Intel::DOMAIN my_special_source |
This simple code generates a detailed output. The output includes the following components:
- Capture_loss
- Connection
- Files
- Http
- Intel
- Known_Hosts
- Known_Services
- Software
- Stats
Detailed instructions on the intelligent framework are available at https://docs.zeek.org/en/stable/frameworks/intel.html.
One of the major advantages of Zeek is that it comes with comprehensive documentation. Detailed teaching and training modules are available at https://www.zeek.org/playground/index.html. Zeek videos are available at https://www.youtube.com/zeekurity.
This article is only a sneak peek into the world of Zeek. With the resources listed above, interested readers can easily explore it.












































































