While Sandboxed API is currently implemented for software libraries written in the C programming language, the company plans to add support for more programming runtimes in the future.
 Google has open-sourced a project, called Sandboxed API, that can help programmers sandbox their C and C++ libraries running on Linux systems and protect them from malicious user input and exploits.
Google has open-sourced a project, called Sandboxed API, that can help programmers sandbox their C and C++ libraries running on Linux systems and protect them from malicious user input and exploits.
Google has been using this tool internally for its data centers for years. The Sandboxed API is now available on GitHub.
Developers frequently employ software isolation methods, a process commonly referred to as sandboxing, in order to protect software libraries from security vulnerabilities.
“By using sandboxing methods, developers make sure that only resources (files, networking connections and other operating system resources) which are deemed necessary are accessible to the code involved in parsing user-generated content,” Google said in a blog post.
Sandboxed API allows developers to create security policies for individual software libraries.
Google is also making publicly available its core sandboxing project, Sandbox2. “Sandbox2 is now part of Sandboxed API and provides the underlying sandboxing primitives. It can be also used standalone to isolate arbitrary Linux processes, but is considered a lower-level API,” the tech said.
While Sandboxed API is currently implemented for software libraries written in the C programming language (or providing C bindings), the company plans to add support for more programming runtimes in the future.
How Sandboxed API works?
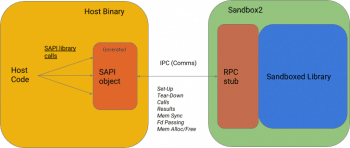
Google explains –Sandboxed API separates the library to be sandboxed and its callers into two separate OS processes: the host binary and the sandboxee. Actual library calls are then marshalled by an API object on the host side and send via interprocess communication to the sandboxee where an RPC stub unmarshals and forwards calls to the original library.
Both the API object (SAPI object) and the RPC stub are provided by the project, with the former being auto-generated by an interface generator. Users just need to provide a sandbox policy, a set of system calls that the underlying library is allowed to make, as well as the resources it is allowed to access and use. Once ready, a library based on sandboxed API can easily be reused in other projects.
Google is looking at improving Sandboxed API and Sandbox2 as well as adding more features for supporting more programming runtimes, different operating systems or alternative containment technologies.











































































