The versatility of Python is often used to create applications that do useful work. PytheM is an open source tool that uses Python as the backend and performs Web and penetration testing to discover network vulnerabilities.
With the increasing traffic in network-based applications, security is becoming a challenge and the network environment has to be made safe from different types of attacks. The probability of vulnerabilities in network or Web-based applications increases if vulnerability testing is not done properly. In traditional implementations, network administrators use their own sets of tools to test their network environment, but such tools can be restricted to specific types of attacks. It is always desirable that administrators use different types of penetration and vulnerability testing tools which are meant to resolve assorted attacks. This is done to check the overall deployment during different types of attacks, thus ensuring that the network or Web-based environment is secured from multiple attacks without any compromise on safety.
Penetration testing and open source tools
A number of frameworks and software tools are available that provide the features to evaluate the network or Web-based applications on different aspects and parameters. In a security audit of Web applications or network devices, the loopholes or vulnerabilities are checked from different aspects so that the attackers or sniffers cannot destroy the environment. Traditionally, penetration tools are used by the network administrators and application developers to analyse the weak points or vulnerabilities. In penetration testing, the applications or devices are put through pre-programmed attacks so that the actual behaviour of hardware or software can be checked. If the applications or hardware devices react in abnormal ways during penetration testing, troubleshooting is done and suitable remedial measures are taken to cope with the attacks. Penetration testing can be implemented on any type of deployment including on networks, devices, websites, servers or software installations.
There are many penetration testing and security audit tools available that are free and open source, and can be used for security audits or bug tracking in the deployments. These tools provide the functions to analyse the applications or devices under different attacks and identify the weak points so that the vulnerabilities can be removed before actual deployment.
Python, a high performance programming language for multiple applications
Python is one of the powerful and cross-platform programming languages used for most of the high performance environments including cloud computing, Big Data processing, network programming, socket analytics, data science, statistical analysis and many others. It offers a large set of tools that have been developed specifically for penetration testing and security audits.
There are many penetration testing and security audit tools developed with Python, and these are used widely by corporates as well as individuals. These tools are used for digital forensics and vulnerability analysis on different types of hardware and software. The tools can be categorised under network analysis, reverse engineering and debugging, Web-based analytics, forensics applications, malware analysis and packets investigation. A few of the tools under each category are described below.
Network analysis: The tools for network analysis are Dirtbags py-pcap, dpkt, flowgrep, Habu, Impacket, etc.
Reverse engineering and debugging: Androguard, CHIPSEC, Capstone, Frida, IDAPython, etc, may be used for reverse engineering and debugging.
Web-based analytics: Some of the Web-based analytics tools are FunkLoad, Ghost.py, HTTPie, ProxMon, Requests, etc.
Forensics applications: Aft, LibForensics, Rekall, Volatility, TrIDLib, etc, can be used for forensics applications.
Malware analysis and packets investigation: For malware analysis and packets investigation, CapTipper, Exefilter, jsunpack-n, phoneyc, PyClamAV, etc, may be used.
The PytheM penetration testing framework
A large set of software tools and libraries written in Python is available for simulation of different types of attacks. Python is rich in the additional plugins and modules that can be attached for high performance forensics applications and cyber security. PytheM is one of the powerful tools which uses Python at the back-end. It provides functions to test the network and Web applications for different types of attacks before actual deployment.
PytheM is a free and open source penetration testing framework with multi-functional features to analyse the network and Web deployment to prevent multiple attacks. It assists security professionals and administrators in evaluating and performing security audits of their infrastructure. You can find more on PytheM at https://github.com/m4n3dw0lf/pythem.
Downloading and installation instructions
PytheM can be installed without any complexity on Linux/GNU platforms. It can be installed and executed on Docker containers.
Given below is the code to install PytheM on Ubuntu systems:
$ sudo apt-get update $ sudo apt-get install -y build-essential python-dev python-pip tcpdump python-capstone libnetfilter-queue-dev libffi-dev libssl-dev
To install PytheM using Pip, use the following command:
$ sudo pip install pythem
The code for installing PytheM using the Git repository is:
$ git clone https://github.com/m4n3dw0lf/pythem $ cd pythem $ sudo python setup.py install
To install PytheM by integrating the source and Pip, use the following code:
$ git clone https://github.com/m4n3dw0lf/pythem $ cd pythem $ sudo python setup.py sdist $ sudo pip install dist/*
To execute and run PytheM with root privileges, type:
$ sudo pythem
To install PytheM on Docker, give the following command:
docker run -it --net=host --rm --name pythem m4n3dw0lf/pythem
Analysis of different attacks using PytheM
There are many types of attacks in the network environment, which can be avoided if tested by network administrators. It is the responsibility of network and Web administrators to evaluate their environment for different cracking attempts so that a secured mechanism can be launched.
PytheM provides the features to implement different types of attacks for penetration testing of the network deployment. Using these assaults, security professionals can predict the vulnerabilities in their network.
The following are a few of the attacks that can be simulated using PytheM:
- Man-in-the-middle attacks
- ARP spoofing
- DHCP spoofing
- Brute force attacks
- ACK injection
- PCAP analysis
- URL busters
- Overthrow DNS
- Redirections, and many others

Implementation of ARP spoofing
In an ARP spoofing attack, the malicious attack source sends fake or manipulated ARP (Address Resolution Protocol) messages to the network. This process disguises the router and servers, which allows the attacker to steal information even from a privacy-aware network environment.
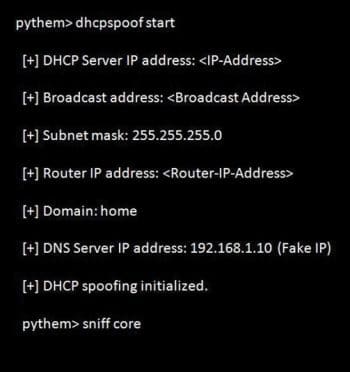
DHCP spoofing attacks or ACK injection
In a DHCP spoofing and starvation attack, the hacker or malicious source can gain access to the DHCP server. By this attack, the attacker can overload the server or important information can be fetched out.
It is always desirable to test the application or network infrastructure before deployment so that there is minimum scope for any cracking or hacking. If the applications or devices are tested using penetration testing and security audit tools like PytheM or any similar library, the overall network environment can be secured from multiple attacks.