Discover SELinux, a security module that provides extra protocols to ensure access control security. It supports mandatory access controls (MAC) and is an integral part of RHEL’s security policy.
Security-Enhanced Linux or SELinux is an advanced access control built into most modern Linux distributions. It was initially developed by the US National Security Agency to protect computer systems from malicious tampering. Over time, SELinux was placed in the public domain and various distributions have incorporated it in their code. To many systems administrators, SELinux is uncharted territory. It can seem quite daunting and at times, even confusing. However, when properly configured, SELinux can greatly reduce a system’s security risks and knowing a bit about it can help you to troubleshoot access related error messages.
Basic SELinux security concepts
Security-Enhanced Linux is an additional layer of system security. The primary goal of SELinux is to protect the users’ data from system services that have been compromised. Most Linux administrators are familiar with the standard user/group/other permissions security model. This is a user and group based model known as discretionary access control. SELinux provides an additional layer of security that is object based and controlled by more sophisticated rules, known as mandatory access control. To allow remote anonymous access to a Web server, firewall ports must be opened. However, this gives malicious users an opportunity to crack the system through a security exploit, if they compromise the Web server process and gain its permissions — the permissions of Apache user and Apache group, which user/group has read write access to things like document root (/var/www/html), as well as the write access to /var, /tmp and any other directories that are world writable.
Under discretionary access control, every process can access any object. But when SELinux enables mandatory access control, then a particular context is given to an object. Every file, process, directory and port has a special security label, called a SELinux context. A context is a name that is used by the SELinux policy to determine whether a process can access a file, directory or port. By default, the policy does not allow any interaction unless an explicit rule grants access. If there is no rule, no access is allowed.
SELinux labels have several contexts—user, role, type and sensitivity. The targeted policy, which is the default policy in Red Hat Enterprise Linux, bases its rules on the third context—the type context. The type context normally ends with _t. The type context for the Web server is httpd_t . The type context for files and directories normally found in
/var/www/html is httpd_sys_content_t, and for files and directories normally found in /tmp and /var/tmp is tmp_t. The type context for Web server ports is httpd_port_t.
There is a policy rule that permits Apache to access files and directories with a context normally found in /var/www/html and other Web server directories. There is no ‘allow’ rule for files found in /var/tmp directory, so access is not permitted. With SELinux, a malicious user cannot access the /tmp directory. SELinux has a rule for remote file systems such as NFS and CIFS, although all files on such file systems are labelled with the same context.
SELinux modes
For troubleshooting purposes, SELinux protection can be temporarily disabled using SELinux modes.
SELinux works in three modes– enforcing mode, permissive mode and disabled mode.
Enforcing mode: In the enforcing mode, SELinux actively denies access to Web servers attempting to read files with the tmp_t type context. In this mode, SELinux both logs the interactions and protects files.
Permissive mode: This mode is often used to troubleshoot issues. In permissive mode, SELinux allows all interactions, even if there is no explicit rule, and it logs the interactions that it would have denied in the enforcing mode. This mode can be used to temporarily allow access to content that SELinux is restricting. No reboot is required to go from enforcing mode to permissive mode.
Disabled mode: This mode completely disables SELinux. A system reboot is required to disable SELinux entirely, or to go from disabled mode to enforcing or permissive mode.
SELinux status
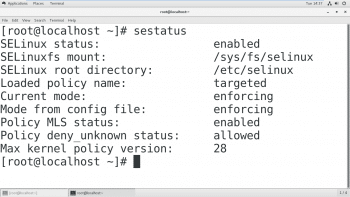
To check the present status of SELinux, run the sestatus command on a terminal. It will tell you the mode of SELinux.
# sestatus
Changing the current SELinux mode
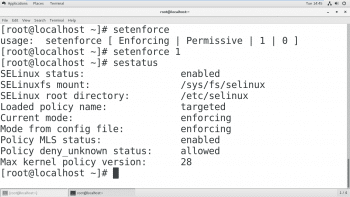
Run the command setenforce with either 0 or 1 as the argument. A value of 1 specifies enforcing mode; 0 would specify permissive mode.
# setenforce
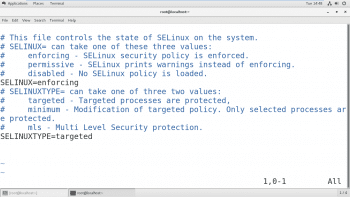
Setting the default SELinux mode
The configuration file that determines what the SELinux mode is at boot time is /etc/selinux/config. Note that it contains some useful comments.
Use /etc/selinux/config to change the default SELinux mode at boot time. In the example shown in Figure 3, it is set to enforcing mode.
Initial SELinux context
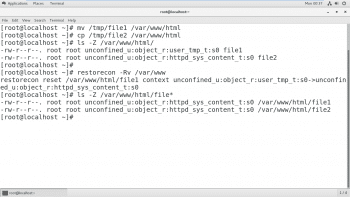
Typically, the SELinux context of a file’s parent directory determines the initial SELinux context. The context of the parent directory is assigned to newly created files. This works for commands like vim, cp and touch. However, if a file is created elsewhere and the permissions are preserved (as with mv cp -a), the original SELinux context will be unchanged.
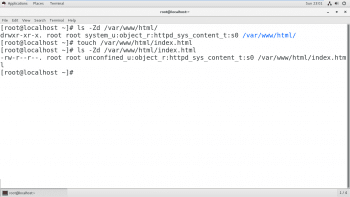
Changing the SELinux context of a file
There are two commands that are used to change the SELinux context of a file—chcon and restorecon. The chcon command changes the context of a file to the context specified as an argument to the command. Often, the -t option is used to specify only the type component of the context.
The restorecon command is the preferred method for changing the SELinux context of a file or directory. Unlike chcon, the context is not explicitly specified when using this command. It uses rules in the SELinux policy to determine what the context of a file should be.
Defining SELinux default file context rules
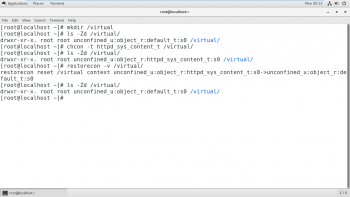
The semanage fcontext command can be used to display or modify the rules that the restorecon command uses to set the default file context. It uses extended regular expressions to specify the path and filenames. The most common extended regular expression used in fcontext rules is (/.*)? which means “optionally match a / followed by any number of characters.” It matches the directory listed before the expression and everything in that directory recursively.
The restore command is part of the policycoreutil package and semanage is part of the policycoreutil-Python package.
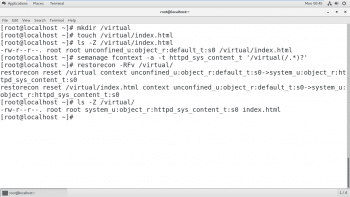
As shown in Figure 6, the permission is preserved by using the mv command while the cp command will not preserve the permission, which will be the same as that of the parent directory. To restore the permission, run restorecon which will give the parent directory permission to access the files.
Figure 7 shows how to use semanage to add a context for a new directory. First, change the context of the parent directory using the semanage command, and then use the restorecon command to restore the parent permission to all files contained in it.
SELinux Booleans
SELinux Booleans are switches that change the behaviour of the SELinux policy. These are rules that can be enabled or disabled, and can be used by security administrators to tune the policy to make selective adjustments.
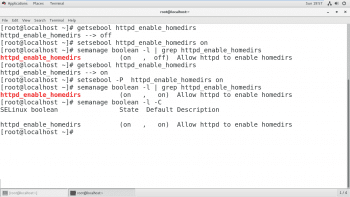
The getsebool command is used to display SELinux Booleans and their current values. The -a option helps this command to list all the Booleans.
The getsebool command is used to display SELinux Booleans and setsebool is used to modify these. setsebool -P modifies the SELinux policy to make the modifications persistent. semanage boolean -1 will show whether or not a Boolean is persistent, along with a short description of it. To list only local modifications to the state of the SELinux Booleans (any setting that differs from the default in the policy), the -C option with semanage Boolean can be used.
In Figure 8, the Boolean was first modified, and then this modification was made persistent; the -C option was used with semanage to list the modifications.
Troubleshooting in SELinux
Sometimes, SELinux prevents access to files on the server. Here are the steps that should be followed when this occurs.
- Before thinking of making any adjustments, consider that SELinux may be doing its job correctly by prohibiting the attempted access. If a Web server tries to access the files in /home, this could signal a compromise of the service if Web content isn’t published by the users. If access has been granted, then additional steps need to be taken to solve the problem.
- The most common SELinux issue is an incorrect file context. This can occur when a file is created in a location with one file context, and moved into a place where a different context is expected. In most cases, running restorecon will correct the issue. Correcting issues in this way has a very narrow impact on the security of the rest of the system.
- Another remedy could be adjustment of the Boolean. For example, the ftpd_anon_write Boolean controls whether anonymous FTP users can upload files. This Boolean may be turned on if you want to allow anonymous FTP users to upload files to a server.
- It is possible that the SELinux policy has a bug that prevents a legitimate access. However, since SELinux has matured, this is a rare occurrence.