Contiki is a widely used IoT enabled operating system that is free and open source. Cooja is the Contiki network simulator and is also used to program sensor devices. Read on to learn how IPv6 protocols can be programmed with Contiki and Cooja.
Currently, technology has developed to the extent that various devices and gadgets are able to interact with each other, without human interference. This communication technology is today known as the Internet of Things (IoT). IoT based communication is used in a number of applications, including defence equipment, smart cities, smart offices, highway patrolling, smart toll collection, business communications, satellite televisions, and traffic systems or interconnected Web cams for security. IoT is also known and associated with other terms, including ubiquitous computing (UbiComp), pervasive computing or ambient computing, using which a number of devices and objects are virtually connected for remote monitoring and decision making.
The security aspects of the Internet of Things (IoT)
As so many devices and so much equipment are interconnected via a virtual environment, there are serious issues related to security, privacy and the overall performance of IoT networks. These networks are becoming increasingly vulnerable to attacks from assorted sources.
Different types of attacks are used to control and damage the IoT environment at different layers. The attackers can damage and control the IoT network by sending malicious packets and signals, and infrastructure can be virtually destroyed. Such attacks are the most worrisome, as they affect the entire network.
Denial of Service (DoS) attacks: In a DoS attack, network availability is jammed by the attacker node or malicious packets, by capturing the bandwidth or communication channel. Here, authentic and legitimate users are not able to access the network services. This is a notorious attack that works on the network layer of an IoT based scenario, and gets more dangerous when it becomes a Distributed Denial of Service (DDoS) attack, whereby the attacker or malicious node attacks a network from multiple and different locations.
The Sybil attack: This affects the network layer of a vehicular network a lot. In this attack, the identity of the nodes is manipulated. The malicious node attempts to fabricate its identity by pretending to be a registered or original source node. In a Sybil attack, the attacker node creates assorted vehicles or nodes of the same identity by replication, and forces other nodes to leave or move off the network faster. These attacks can be detected with resource testing, based on the assumption that vehicles have limited resources. Sybil attacks can be addressed using public key cryptography, where public keys are used to authenticate vehicles.
A node imitation attack: In this type of attack, messages can be transmitted by a malicious node that has imitated another authentic one, by mimicking the latter’s identity. In this way, the imitating attacker can send out malicious messages to any node by changing its own identity. The IoT node that has disguised its identity in this attack can capture authentic and secured packets, which can be disastrous for the entire network.
An application level attack: This type of attack in the IoT environment tampers with the messages and retransmits them to an untrusted non-secure destination. For example, in Internet of Vehicles (IoV) based implementations, the high-traffic lane could get maliciously broadcast as a ‘congestion-free lane’, leading to chaos during rush hour.
The importance of IPv6 in IoT
Security and integrity are the main issues in an IoT based network environment where interception-free secured communication is required. To enforce and integrate higher degrees of security, there is a need to implement IPv6 for IoT scenarios, with dynamic hybrid cryptography in key-generation and authentication. The IPv6 based approach can be enabled with fully secured algorithms, which are not vulnerable to interception. With the increasing implementation of IoT in diverse domains, it becomes necessary to work out the security aspects of IoT, by ensuring the secured routing of packets to prevent intrusions and ensure all transmissions can be fully secured.
RPL (Routing Protocol for Low-power and Lossy networks)
RPL is the IPv6 based protocol for IoT. It is primarily integrated for IPv6 over low-power wireless personal area networks (6LowPAN). It works with the dynamic creation of Destination-Oriented Directed Acyclic Graph (DODAG), and has unidirectional as well as bidirectional communication. It has multiple instances with localised behaviour for higher optimisation. RPL enables each node in the framework to choose whether packets are to be sent upwards to their root or downwards to their child nodes.
Programming RPL with IPv6 in Cooja
Contiki is one of the widely used IoT enabled operating systems under free and open source distribution. Contiki is equipped with the Cooja simulator, which is used for simulation as well as the programming of sensor devices. It offers enormous options to program the IoT nodes for real life implementations. The Cooja simulator enables the programmer to import and program enormous types of IoT motes, and to get the results from different algorithms. To program, control and monitor the remote IoT devices, the backend C programs and related header files can be customised and recompiled to get the desired results. Contiki works on IPv4 as well as IPv6 networking with the integration of lightweight protocols, so that low power chips and radio frequency chips can be connected without performance issues.
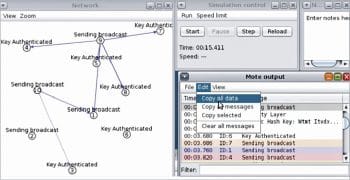
Figure 1 depicts the simulation of multiple IoT motes in the Cooja simulator with the integration of dynamic cryptography. The simulation results can be analysed from the Mote Output in which there is an option to fetch the execution logs. All the data communication and signals are logged in Mote Output which can be further investigated using different types of graphs.
Once the simulation is complete, the network log files are analysed. This includes the source and destination motes, the time and the overall activities performed during simulation. In the Mote Output window, the log data can be copied and further analysed using data mining and machine learning tools for predictive analytics.
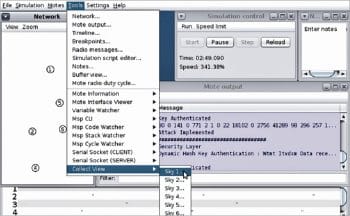
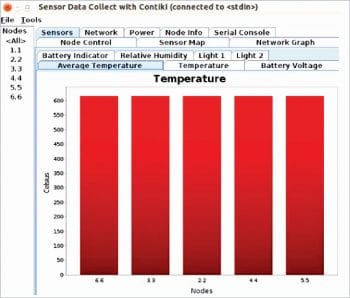
Figure 2 represents the Collect View in the Cooja simulator. It analyses the individual IoT mote. The IoT mote analytics can be viewed from the Tools menu of Cooja. From Collect View, any of the IoT motes can be analysed on multiple parameters including latency, temperature, time and other important parameters, which contributes to better performance evaluation.
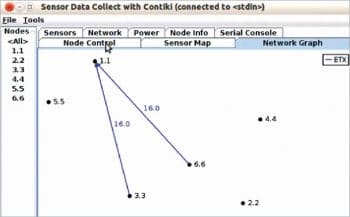
Figure 3 depicts the different options by which IoT simulation can be analysed and predictions on various parameters can be made. The network graph tab in the Collect View of Cooja enables the researcher to view the dynamic topology and connections of sensor nodes, as shown in Figure 4.
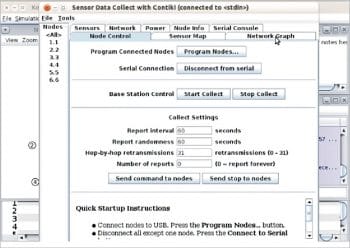
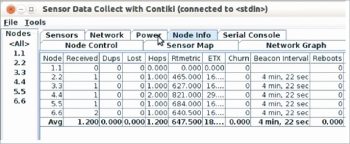
Figure 5 shows the results and parameter based analysis of different nodes in tabular format. It enables the IoT programmer to inspect individual nodes as well as many or all of them in groups, to analyse multiple factors.
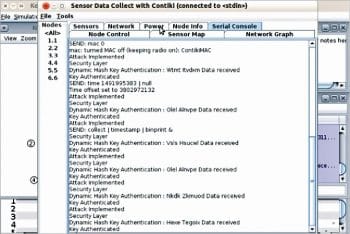
The Serial Console tab seen in Figure 6 shows the data transmission log, along with the results related to authentication. In Figure 6, the implementation of the attack and authentication process is depicted, which assists the developer in examining the effect of customised code on real-time sensors.
Plotting results in the form of graphs
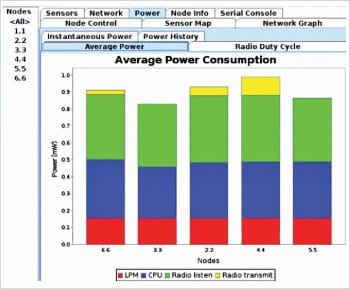
As depicted in Figure 7, there are a vast number of parameters, including LPM, CPU, Radio Listen and Radio Transmit, which need to be looked at during the IoT simulation. The results in the above cited graph are consistent and low-power mode is in the integrity mode. In addition, the Radio Listen parameter is also consistent.
Network analysis using Foren6
Foren6 is a powerful tool with a free and open source library. It is used for the analysis of 6LoWPAN networks. It is integrated with the sniffing modules, besides being able to plot the results in assorted formats including text or graphs. Foren6 makes use of integrated sniffers for capturing and analysing the traffic associated with 6LoWPAN in a graphical user interface (GUI). It is powerful enough to record and plot the RPL information with the deep analytics of packets in network transmission.
Installation of Foren6 with Contiki
To configure the dependencies, type:
$ sudo apt-get install -y qt4-qmake libqt4-dev make libexpat1-dev cmake libpcap0.8-dev libc6-dev tshark gcc g++
To get the source code with GIT, type:
$ git clone https://github.com/cetic/foren6.git
Use the following commands to install Foren6:
$ cd foren6 $ make $ sudo make install
Configuration of Sniffer to activate real-time capturing
To access and work on USB serial devices, the Linux Group ‘dialout’ is used. Initially, Foren6 is launched as the root user. If any other user account is used, then the user should be assigned the Linux Group ‘dialout’ to use USB.
$ sudo adduser <username> dialout Sniffer Programming $ git clone https://github.com/cetic/contiki $ cd contiki $ git checkout sniffer $ make TARGET=sky savetarget sniffer.upload
Scope of IoT based research simulations using Cooja
The Internet of Things is an emerging domain of research at various academic as well as corporate establishments. Because of the increasing number of devices currently connected under the IoT, there are vast areas for research in this domain.
The following are some of the approaches with which novel and effectual algorithms can be devised and implemented using Cooja:
- Interoperability and cross-protocol compatibility
- Development of energy-aware IoT scenarios
- Power aware scheduling and routing
- Prediction and avoidance of energy consumption attacks
- Lifetime analytics for robust IoT environments
- Reproducible and multi-interface implementations

















































































can you guide me with my final year project of detecting and analyzing DIO (DODAG information object) inconsistency attacks on RPL using cooja ?
Could you please guide me in developing a new Objective Function in contiki?