This article covers the basics of Iptables and will add to your understanding of this firewall utility. After going through it, you can try your hand at mixing and matching different sets of rules as per your needs.
Iptables is a firewall utility built for Linux (2.4.x and later) operating systems. Whether youre a Linux techie or a systems administrator, its very likely that Iptables can be of extraordinary use to you in some way or the other.
Iptables is used to set up, maintain and inspect the tables of IPv4 packet filter rules in the Linux kernel. You can define several different tables in the Linux system. Each table contains a number of built-in chains and may also contain user-defined chains. When a connection tries to establish itself on your system, Iptables looks for a rule in its list to match it to. If it doesnt find one, it resorts to the default action.
How Iptables works
When Iptables is able to match a connection that tries to establish itself on your system with a rule in its list, the action that takes place is called a target. A target can be a final policy decision for the packet, such as Accept or Drop. It can also be Move the packet to a different chain for processing.
A firewall rule specifies criteria for a packet and a target. If the packet does not match, the next rule in the chain is examined; and if it does match, then the next rule is specified by the value of the target, which can be the name of a user-defined chain or one of the special values like Accept, Drop, Queue or Return.
Iptables tables and chains
The Linux kernel uses the Netfilter facility to filter packets, allowing some of them to be received by or to pass through the system while stopping others. This facility is built into the Linux kernel, and has five built-in tables or rules lists, as follows.
- Filter: This is the default table for handling network packets.
- NAT: This is used to alter packets that create a new connection and also used for Network Address Translation (NAT).
- Mangle: This is for specific types of packet alterations.
- Raw: This is mainly for configuring exemptions during connection tracking in combination with the NOTRACK target.
- Security: This is used for Mandatory Access Control (MAC) networking rules, such as those enabled by the SECMARK and CONNSECMARK targets.
Each table has a group of built-in chains, which correspond to the actions performed on the packet by Netfilter.
Filter table
This is the default table for Iptables. If you dont define any table, you use the filter table.
The built-in chains for the filter table are as follows.
Input chain: The input chain is applied to network packets that are targeted at the host. It is responsible for handling incoming connections to the firewall. If a user tries to SSH into any server, Iptables will attempt to match the IP address and port it to a rule in the input chain.
Output chain: The output chain is used for outgoing connections, i.e., packets generated locally and going out from the local server.
Forward chain: This is applied to network packets routed through the host.
NAT table
The built-in chains for the NAT table are as follows.
- Pre-routing: Alters network packets when they arrive. This is used in Destination Network Address Translation.
- Output: Alters locally-generated network packets before they are sent out.
- Post-routing: Alters network packets before they are sent out.
Mangle table
The built-in chains for the Mangle table are as follows.
- Input: Alters network packets targeted for the host.
- Output: Alters locally-generated network packets before they are sent out.
- Forward: Alters network packets routed through the host.
- Pre-routing: Alters incoming network packets before they are routed.
- Post-routing: Alters network packets before they are sent out.
Raw table
- Output: Applies to locally-generated network packets before they are sent out.
- Pre-routing: Applies to incoming network packets before they are routed.
Security table
- Input: Applies to network packets targeted for the host.
- Output: Applies to locally-generated network packets before they are sent out.
- Forward: Applies to network packets routed through the host.
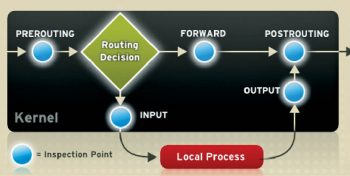
Every network packet received by or sent from a Linux system is subject to at least one table. However, a packet may be subjected to multiple rules within each table before emerging at the end of the chain. The structure and purpose of these rules may vary, but they usually seek to identify a packet coming from or going to a particular IP address, or set of addresses, when using a particular protocol and network service. Figure 1 outlines how the flow of packets is examined by the Iptables sub-system.
Iptables command options
The Iptables command options are as follows.
-A: Appends the rule to the end of the specified chain. Unlike the -I option described below, it does not take an integer argument. It always appends the rule to the end of the specified chain.
-D <integer> | <rule>: Deletes a rule in a particular chain by number (such as 5 for the fifth rule in a chain), or by rule specification. The rule specification must exactly match an existing rule.
Example:
Iptables -D INPUT --dport 80 -j DROP, Iptables -D INPUT 1 |
This command deletes a rule in a chain.
-E: Renames a user-defined chain, which is any chain other than the default, pre-existing ones. (Refer to the -N option, below, for information on creating user-defined chains.) This is a cosmetic change and does not affect the structure of the table.
Example:
Iptables -E allowed disallowed |
In this example, we changed the name of the chain from allowed to disallowed.
-F: Flushes the selected chain, which effectively deletes every rule in the chain. If no chain is specified, this command flushes every rule from every chain.
Example:
Iptables -F INPUT This command flushes all rules from the specified chain. |
-h: Provides a list of command structures, as well as a quick summary of command parameters and options.
-I [<integer>]: Inserts the rule in the specified chain at a point specified by a user-defined integer argument. If no argument is specified, the rule is inserted at the top of the chain.
Example:
Iptables -I INPUT 1 --dport 80 -j ACCEPT |
It inserts a rule somewhere in a chain. The rule is inserted as the actual number that we specify.
-L: Lists all of the rules in the chain specified after the command. To list all rules in all chains in the default filter table, do not specify a chain or table. Otherwise, the following syntax should be used to list the rules in a specific chain in a particular table.
Example:
Iptables -L <chain-name> -t <table-name> |
This command lists all the entries in the specified chain.
Iptables -L INPUT |
-N: Creates a new chain with a user-specified name. The chain name must be unique.
Example:
Iptables -N allowed |
This command tells the kernel to create a new chain of the specified name in the specified table.
-P: Sets the default policy for the specified chain, so that when packets traverse an entire chain without matching a rule, they are sent to the specified target, such as ACCEPT or DROP.
Example:
Iptables -P INPUT DROP |
This command tells the kernel to set a specified default target, or policy, on a chain.
-R: Replaces a rule in the specified chain. The rules number must be specified after the chains name. The first rule in a chain corresponds to rule number one.
Example:
Iptables -R INPUT 1 -s 192.168.0.1 -j DROP |
This command replaces the old entry at the specified line.
-X: Deletes a user-specified chain. You cannot delete a built-in chain.
Example:
Iptables -X allowed |
This command deletes the specified chain from the table.
-Z: Sets the byte and packet counters in all chains for a table to zero.
Example:
Iptables -Z INPUT |
This command tells the program to set all counters to zero in a specific chain, or in all chains.
Iptables parameter options
[!] -p, –protocol protocol: This is the connection protocol used. The specified protocol can be one of tcp, udp, udplite, icmp, esp, ah, sctp or the special keyword all. Or it can be a numeric value, representing one of these protocols or a different one. A protocol name from /etc/protocols is also allowed. A ! argument before the protocol inverts the test.
[!] -s, –source address[/mask][,…]: This is the address[/mask] source specification. Address can be either a network name, a hostname, a network IP address (with /mask), or a plain IP address. A ! argument before the address specification inverts the sense of the address.
[!] -d, –destination address[/mask][,…]: This is the address[/mask] destination specification.
-j, –jump target: This jumps to the specified target when a packet matches a particular rule.
[!] -i, –in-interface name: This is the name of an interface via which a packet has been received (only for packets entering the INPUT, FORWARD and PREROUTING chains). When the ! argument is used before the interface name, the sense is inverted. If the interface name ends in a +, then any interface which begins with this name will match. If this option is omitted, any interface name will match.
[!] -o, –out-interface name: This is the name of an interface via which a packet is going to be sent (for packets entering the FORWARD, OUTPUT and POSTROUTING chains). When the ! argument is used before the interface name, the sense is inverted. If the interface name ends in a +, then any interface which begins with this name will match. If this option is omitted, any interface name will match.
[!] -f, –fragment: This rule applies only to fragmented packets.
You can use the exclamation point character (!) option before this parameter to specify that only unfragmented packets are matched.
-c, –set-counters packets bytes: This enables the administrator to initialise the packet and byte counters of a rule (during the INSERT, APPEND and REPLACE operations).
Writing a simple rule set of Iptables
The Iptables rule with respect to allowing loopback connections is as follows:
sudo Iptables -A INPUT -i lo -j ACCEPTsudo Iptables -A OUTPUT -o lo -j ACCEPT |
The following rule allows established and related incoming connections:
sudo Iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT |
This allows established outgoing connections:
sudo Iptables -A OUTPUT -m conntrack --ctstate ESTABLISHED -j ACCEPT |
The following rule is for moving from local network to external network:
sudo Iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT |
The following rule drops invalid packets:
sudo Iptables -A INPUT -m conntrack --ctstate INVALID -j DROP |
This blocks an IP address:
sudo Iptables -A INPUT -s 192.168.122.1 -j DROP |
This is for Reject:
sudo Iptables -A INPUT -s 192.168.122.1 -j REJECT |
This blocks connections to a network interface:
Iptables -A INPUT -i eth0 -s 15.15.15.51 -j DROP |
This allows all incoming SSH:
sudo Iptables -A OUTPUT -p tcp --dport 22 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPTsudo Iptables -A INPUT -p tcp --sport 22 -m conntrack --ctstate ESTABLISHED -j ACCEPT |
Saving rules
Ubuntu: To save the Iptables rules in Ubuntu, use the Iptables-persistent package. You can install it through apt-get.
sudo apt-get install Iptables-persistent |
After updating your firewall rules, you can save the change by using the command given below:
sudo invoke-rc.d Iptables-persistent save |
CentOS 6 and older: CentOS 6 and older versions of the OS use FirewallD by default. You can use Iptables service script to save the Iptables changes as shown below. Your current Iptables rules will be saved in the /etc/sysconfig/Iptables file.
sudo service Iptables save |
This article has covered the basics of Iptables — what it is, how it works, the different types of Iptables, options to Iptables and a basic set of rules. However, a lot more can be done with Iptables. You can mix and match the different sets of rules as per your need.












































































