Security of data is of paramount concern to those in government and industry. This article takes readers through the typical security concerns in the traditional environment, before going on to the cloud environment.
Before we discuss security concerns in the cloud, let us take a small detour to look at the security situation in traditional environments. In todays competitive market, a typical IT environment has fewer capabilities to handle dynamic requirements due to budget constraints and a large user base. To survive in the current state and to plan for long-term benefits, organisations need to reduce costs, increase storage capacity, as well as automate the monitoring of IT environments and the management of resources for disaster recovery and availability, so as to achieve a flexible IT environment.
The following are the challenges in the traditional environment:
- Security systems utilise excessive amounts of resources
- Vulnerability scanning or monitoring tools may not detect vulnerability threats due to the fast growing volume of data
- Accurate and timely information about threats is not widely shared; information about the vulnerabilities remains with a smaller group and not all the stakeholders
- Audit systems are not built to operate on the dynamic nature of data centres
- Frequent failovers occur due to limitations on scalability
- Aggressive cost-cutting plans are degrading security programs at a time when threats are escalating
- Security access privileges and roles are not as per standards
Complexities of the underlying infrastructure in on-premise environments have attracted organisations to the cloud environment to achieve agility, high availability and reliability. Thus, an organisations security and compliance requirements also need to be aligned and automated in an agile cloud environment to realise the desired benefits of moving to the cloud.
Security in the cloud
Cloud computing provides the next generation of Internet-based, scalable and distributed computing systems in which resources are offered as a service. Todays IT organisations are under increasing pressure to securely deploy applications in public, private or hybrid clouds. Security in the cloud environment is a major concern. Despite the likely gains achieved from cloud computing, the security model is still not entirely fool-proof and hence it impacts cloud adoption. Traditional security controls and policies are not the best fit for the virtual world. Multi-tenancy, virtualisation and geographical differences have made the boundaries of the security model more dynamic than before. Cloud security is no longer the elephant in the room since various organisations and standards bodies have raised their concerns about it. It is the general public as well as the providers and consumers of cloud services who seem to continue in a state of ignorant bliss. Cloud consumers and service providers must realise that a stitch in time will save nine.
Infrastructure abstraction and lack of visibility in cloud resources can create a number of security and compliance issues. In addition to the usual challenges of developing secure IT systems, cloud computing presents an added level of risk because:
- Services are outsourced to a third party
- It requires moving an application into hostile territory
- Multi-tenancy
- Loss of governance
- Legal and contractual risks
Cloud security is basically about three goals or objectives:
- Confidentiality (C)
- Integrity (I)
- Availability (A)
Cloud security and its compliance are the key components that are needed to protect cloud infrastructure against ever evolving new threats. It helps if organisations rationalise compliance requirements, controls, standards and best practices into centralised security policies administered consistently across virtual and physical infrastructures.
There are certain key areas where security levels are likely to be questionable and addressing them in an efficient manner is a critical task for easy and swift adoption of the cloud environment. Lets look at these areas more closely.
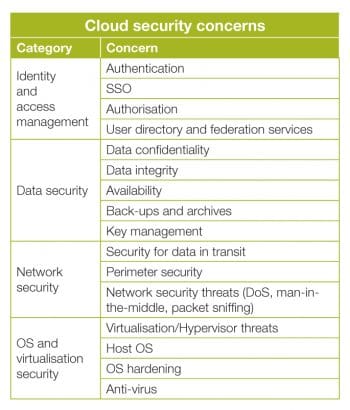
Identity and access management (IAM)
Unauthorised access to information resources in the cloud is a primary concern. In the current state of IAM technology, standards supported by cloud services providers offering various cloud service models (such as SaaS, PaaS and IaaS) are not consistent across providers. Google, Microsoft and Salesforce.com seem to demonstrate basic IAM capabilities. IAM should include the following: identity provisioning and de-provisioning, information privacy, linking, mapping, federation, attributes federation, authentication, SSO and authorisation.
Data security
Confidentiality, integrity and availability (CIA) form the golden trio of data security. Data security becomes more important while using cloud computing for all service models: IaaS, PaaS, and SaaS. Cloud environments are shared with multiple tenants and cloud service providers have privileged access to the data in those environments. Sensitive data stored in a cloud environment must be secured using a combination of strong encryption, access control, contractual liability, etc.
Network security
At the network level of infrastructure security, it is critical to distinguish between public clouds and private clouds. With private clouds, there may not be new attacks, vulnerabilities or changes in risk that information security personnel need to consider. In public clouds, changing security requirements will warrant more attention considering that it is the cloud service provider that is in control of resources.
Virtualisation security
Virtualisation technologies enable multi-tenancy in cloud business models by providing a scalable and shared resource platform for all tenants. The threat of an unauthorised virtual machine (VM) is far higher because it is pretty easy to create and deploy virtual machines. Organisations need to enforce strict policies on the use of such virtual machine environments. VM images can be copied, along with the data and applications that they hold. These images can be brought back online to an unsecured network. It becomes easier for an attacker to access the contents managed within the copied image. Deployment of virtualisation in any organisation should be a controlled and policy-driven roll-out like any other computer platform, software or application.
Physical security
Cloud resources such as servers, routers, storage devices and power supplies that support cloud operations should be physically secure. Safeguards include the adequate control and monitoring of physical access using biometric access control measures and closed circuit television (CCTV) monitoring. Cloud service providers need to clearly explain how they manage physical access to the servers that host client workloads and support client data.
Use cases
Application firewall to protect apps in the private cloud
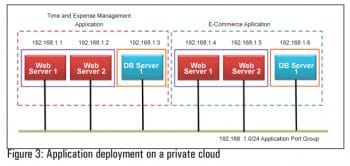
Lets look at a hypothetical case. The XYZ Market is a new shopping channel led by two seasoned industrialists. They have a private cloud for their organisation. XYZ Markets HR and business departments have applications named Time and Expense management and E-commerce respectively, which they want to deploy on a private cloud environment to gain agility, high availability and fault tolerance. Each application has two tiers Web and the data base. The main concern of both departments is how to keep both applications secure in a private cloud environment.
The departments need to enforce the following separation between the applications and tiers of each application using the networking and security firewall provided by specific private cloud products.
- Ensure complete isolation between Application 1 and Application 2
- Isolate one Web server from another in each application
- Allow HTTP (80)/HTTPS (443) traffic to Web servers
- Allow Web server to database server communication on a specific DB port
- Block all other traffic
- Security policies to be completely transparent to IP address changes and network renumbering
- Dynamic rules to be applied to new virtual machines automatically
- Default Deny All policy in case of firewall rules
The solution
This solution gives organisations deep visibility into network communications between virtual machines, and eliminates the hardware and policy sprawl associated with using traditional appliances to secure virtualised applications. In addition to that, it optimises hardware resource utilisation while maintaining strong levels of security.
Security offerings from proprietary and open source initiatives enable a hypervisor-based application-aware firewall to dynamically define and enforce policies for virtual machines that are supporting business critical applications. Customers can define a security group, for instance, to protect a group of virtual machines that might hold credit card data that needs to be PCI compliant, or another group of virtual machines that hold patient health records and needs to be HIPAA compliant.
Firewall rules to accomplish the requirements of this use case must be defined. When a new virtual machine joins the container or security group, the rules set-up will be applied automatically and there will be no need to define new rules.
Advantages
- Eliminates the complexity and cost of using security groups to segregate traffic. An application firewall with deep visibility helps to filter traffic between virtual machines.
- Monitors flows of traffic, independent from firewall rules.
- Reports are based on applications, sessions, bytes and other details, allowing administrators to define and refine their policies based on actual traffic patterns.
Identity management
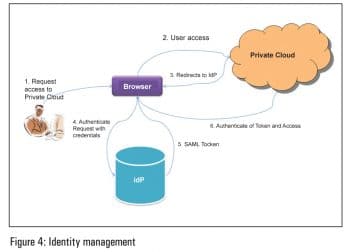
In an organisation, multiple business units deploy their applications in the private cloud. In addition to that, customers also use private cloud resources. The challenge is to provide secure access to all consumers of a private cloud. The security and identity infrastructure in the private cloud is an important management platform component. Private clouds can be based on VMware or OpenStack products.
The solution
Multiple directory services are used in organisations such as OpenLDAP, which is a free, open source implementation of the Lightweight Directory Access Protocol (LDAP), developed by the OpenLDAP Project. Active Directory (or AD) is a directory service created by Microsoft for Windows domain networks and is included in most Windows Server operating systems.
Administrators can set up a separate identity provider (IdP) using either OpenAM, ADFS or any other open source IAM product. The use of the cloud manager component provided by private cloud products helps XYZ Market set the OpenAM IdP as the identity provider for it. Thereafter, when users from XYZ log in to their organisations private cloud, they will be redirected to OpenAM, where they can be authenticated and be directed back to the cloud portal.
Advantages
- Secure access to private cloud infrastructure
- No need for XYZ to create its own user identities in order to participate in the management process, which would increase the administrative overhead
Resources
[1] http://www.cloudsecurityalliance.org/cm.html
[2] http://www.computing.co.uk/computing/comment/2270462/securing-public-private-clouds
[3] http://blog.securityarchitecture.com/2010/08/major-cloud-computing-privacy-legal.html
[4] http://www.opensecurityarchitecture.org/cms/library/patternlandscape/251-pattern-cloud-computing
[5] http://csrc.nist.gov/publications/nistpubs/800-27A/SP800-27-RevA.pdf
[6] http://searchcloudsecurity.techtarget.com/tip/Cloud-security-services-WAFs-and-DdoS-attack-prevention
[7] http://basho.com/tag/ecommerce/
[8] http://www.3dcart.com/pci-compliance.html