The first two articles in the series on Wireshark, which appeared in the July and August 2014 issues of OSFY, covered a few simple protocols and various methods to capture traffic in a switched environment. This article describes an attack called ARP spoofing and explains how you could use Wireshark to capture it.
Imagine an old Hindi movie where the villain and his subordinate are conversing over the telephone, and the hero intercepts this call to listen in on their conversation a perfect man in the middle (MITM) scenario. Now extend this to the network, where an attacker intercepts communication between two computers.
Here are two possibilities with respect to what an attacker can do to intercepted traffic:
1. Passive attacks (also called eavesdropping or only listening to the traffic): These can reveal sensitive information such as clear text (unencrypted) login IDs and passwords.
2. Active attacks: These modify the traffic and can be used for various types of attacks such as replay, spoofing, etc.
An MITM attack can be launched against cryptographic systems, networks, etc. In this article, we will limit our discussions to MITM attacks that use ARP spoofing.
ARP spoofing
Joseph Goebbels, Nazi Germanys minister for propaganda, famously said, If you tell a lie big enough and keep repeating it, people will eventually come to believe it. The lie can be maintained only for such time as the state can shield the people from the political, economic and/or military consequences of the lie. It thus becomes vitally important for the state to use all of its powers to repress dissent, for the truth is the mortal enemy of the lie, and thus by extension, the truth is the greatest enemy of the state.
So let us interpret this quote by a leader of the infamous Nazi regime from the perspective of the ARP protocol: If you repeatedly tell a device who a particular MAC address belongs to, the device will eventually believe you, even if this is not true. Further, the device will remember this MAC address only as long as you keep telling the device about it. Thus, not securing an ARP cache is dangerous to network security.
Note: From the network security professionals view, it becomes absolutely necessary to monitor ARP traffic continuously and limit it to below a threshold. Many managed switches and routers can be configured to monitor and control ARP traffic below a threshold.
An MITM attack is easy to understand using this context. Attackers trying to listen to traffic between any two devices, say a victims computer system and a router, will launch an ARP spoofing attack by sending unsolicited (what this means is an ARP reply packet sent out without receiving an ARP request) ARP reply packets with the following source addresses:
- Towards the victim’s computer system: Router IP address and attacker’s PC MAC address;
- Towards the router: Victim’s computer IP address and attackers PC MAC address.
After receiving such packets continuously, due to ARP protocol characteristics, the ARP cache of the router and the victims PC will be poisoned as follows:
- Router: The MAC address of the attackers PC registered against the IP address of the victim;
- Victims PC: The MAC address of the attackers PC registered against the IP address of the router.
The Ettercap tool
ARP spoofing is the most common type of MITM attack, and can be launched using the Ettercap tool available under Linux (http://ettercap.github.io/ettercap/downloads.html). A few sites claim to have Windows executables. I have never tested these, though. You may install the tool on any Linux distro, or use distros such as Kali Linux, which has it bundled.
The tool has command line options, but its GUI is easier and can be started by using:
ettercap -G
Launch the MITM ARP spoofing attack by using Ettercap menus (Figure 1) in the following sequence (words in italics indicate Ettercap menus):

- Sniff is unified sniffing and selects the interface to be sniffed (for example, eth0 for a wired network).
- Hosts scans for hosts. It scans for all active IP addresses in the eth0 network.
- The hosts list displays the list of scanned hosts.
- The required hosts are added to Target1 and Target2. An ARP spoofing attack will be performed so as to read traffic between all hosts selected under Target1 and Target2.
- Targets gives the current targets. It verifies selection of the correct targets.
- MITM ARP poisoning: Sniff remote connections will start the attack.
The success of the attack can be confirmed as follows: - In the router, check ARP cache (for a CISCO router, the command is show ip arp).
- In the victim PC, use the ARP -a command. Figure 2 gives the output of the command before and after a successful ARP spoofing attack.
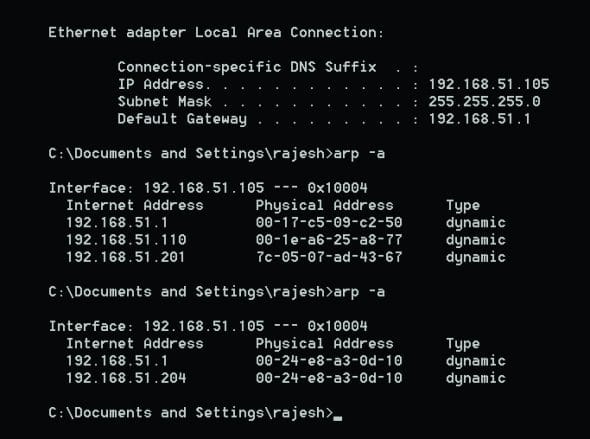
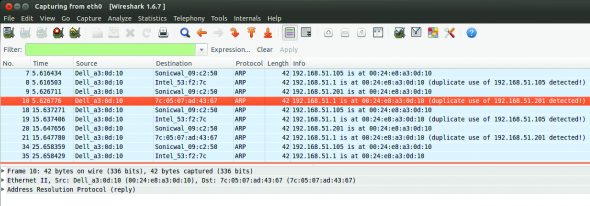
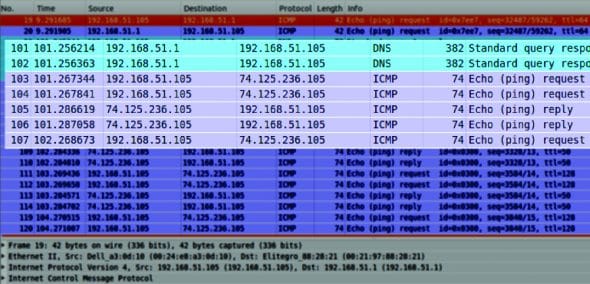
The attacker PC captures traffic using Wireshark to check unsolicited ARP replies. Once the attack is successful, the traffic between two targets will also be captured. Be carefulif traffic from the victim’s PC contains clear-text authentication packets, the credentials could be revealed.
Note that Wireshark gives information such as Duplicate use of IP is detected under the Info column once the attack is successful.
Here is how the actual packet travels and is captured after a successful ARP poisoning attack:
- When the packet from the victim PC starts for the router, at Layer 2, the poisoned MAC address of the attacker (instead of the original router MAC) is inserted as the target MAC; thus the packet reaches the attacker’s PC.
- The attacker sees this packet and forwards the same to the router with the correct MAC address.
- The reply from the router is logically sent towards the spoofed destination MAC address of the attackers’ system (rather than the victim’s PC). It is captured and forwarded by the attacker to the victims PC.
- In between, the sniffer software, Wireshark, which is running on the attackers PC, reads this traffic.
Here are various ways to prevent ARP spoof attacks: - Monitor arpwatch logs on Linux
- Use static ARP commands on Windows and Ubuntu as follows:
- Windows: arp-s DeviceIP DeviceMAC
- Ubuntu: arp -i eth0 -s DeviceIP DeviceMAC
- Control ARP packets on managed switches
Can MITM ARP spoofing be put to fruitful use?
Definitely! Consider capturing packets from a system suspected of malware (virus) infection in a switched environment. There are two ways to do thisuse a wiretap or MITM ARP spoofing. Sometimes, you may not have a wiretap handy or may not want the system to go offline even for the time required to connect the wiretap. Here, MITM ARP spoofing will definitely serve the purpose.
Note: This attack is specifically targeted towards OSI Layer 2a data link layer; thus, it can be executed only from within your network. Be assured, this attack cannot be used sitting outside the local network to sniff packets between your computer and your banks Web server the attacker must be within the local network.
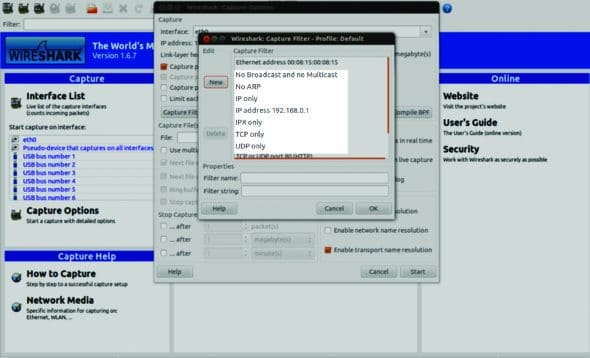
Before we conclude, let us understand an important Wireshark feature called capture filters.
We did go through the basics of display filters in the previous article. But, in a busy network, capturing all traffic and using display filters to see only the desired traffic may require a lot of effort. Wiresharks capture filters provide a way out.
 In the beginning, before selecting the interface, you can click on Capture Options and use capture filters to capture only the desired traffic. Click on the Capture filter button to see various filters, such as ARP, No ARP, TCP only, UDP only, traffic from specific IP addresses, and so on. Select the desired filter and Wireshark will capture only the defined traffic.
In the beginning, before selecting the interface, you can click on Capture Options and use capture filters to capture only the desired traffic. Click on the Capture filter button to see various filters, such as ARP, No ARP, TCP only, UDP only, traffic from specific IP addresses, and so on. Select the desired filter and Wireshark will capture only the defined traffic.
For example, MITM ARP spoofing can be captured using the ARP filter from Capture filters instead of Display filtering the entire captured traffic.
Keep a watch on this column for exciting Wireshark features!















































































