 Xeams is a user friendly, free multi-platform mail server supporting SMTP, IMAP and POP3. It incorporates a powerful junk/ spam filtering engine that eliminates almost 99% of the junk mail.
Xeams is a user friendly, free multi-platform mail server supporting SMTP, IMAP and POP3. It incorporates a powerful junk/ spam filtering engine that eliminates almost 99% of the junk mail.
Xeams Spam filter email engine is developed using Java. Other open source software like Apache Tomcat– A web server used for the administrator console and Derby Apache – which provides an embedded JDBC, a relational database that is used for reporting purposes is also used.
Xeams is freely available to use and supports multiple platforms and multiple email servers, in fact all mail servers which have smart-host functionality. Xeams can work in 3 modes: Standalone server, Hybrid mode and Spam firewall. You can download Xeams from
http://www.xeams.com/Download.htm
Supported OS:
The OS supported by Xeams are
Windows – 2000, 2003, 2008, 2012, XP, Vista, or a newer version. Linux – any distribution, UNIX – Solaris, HP-UX, AIX, BSD, Mac OSx
Specs used for this walk through
OS 2008 R2.
RAM: – 2GB memory
Disk Space: -200 GB
No of IP:
Two IPs are used for Spam Firewall mode:
Exchange server 2013 with Multi role i.e. CAS and Mail Box role
Spam firewall:
In this mode Xeams sits in front of another email server, i.e. Microsoft Exchange or any other SMTP server. Every in-coming email filters through Xeams and only good messages are forwarded to the actual Exchange email server. Your users connect to the Exchange email server via email client and webmail to fetch and send email.
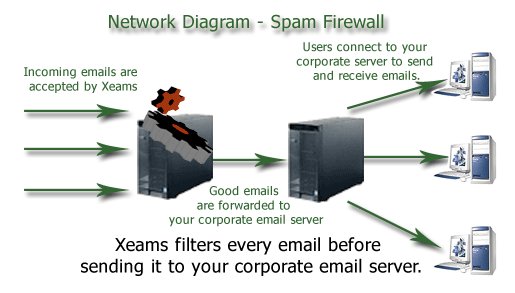
In this walk through we’ll see Xeams in the Spam firewall configuration on a Windows machine and its co-existence with Exchange 2013. Xeams installation is pretty simple, just a two click installation wizard asking installation path and the ‘Finish’ button
NOTE: – This walk though concentrates ONLY on the configuration part that is necessary for Xeams Spam Firewall mode.
After installation, the default browsers opens http://localhost:5272 OR http://SMTP-Server-IP:5272 web administration console and asks the user to set the Xeams admin password.
After login to the web console go to Server Configuration menu, click Server configuration.
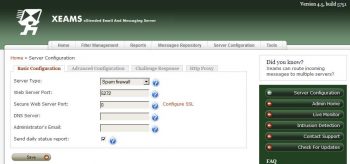
1] Under Basic configuration, for Server Type select Spam firewall. The working mode Xeams will perform. Click Save
2] Under the Server Configuration menu set
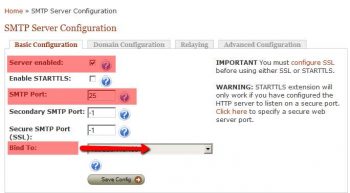
‘SMTP Configuration’ –> ‘Basic Configuration’
Bind To: This is the IP through which outgoing emails will be send. Set ‘A’ and ‘PTR’ record on this IP.
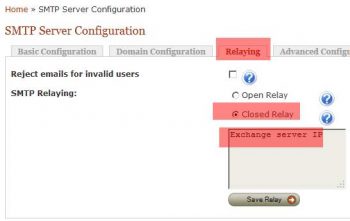
In the Relaying Tab enable ‘Close Relay’ and mention the IP of the Exchange server and click SAVE
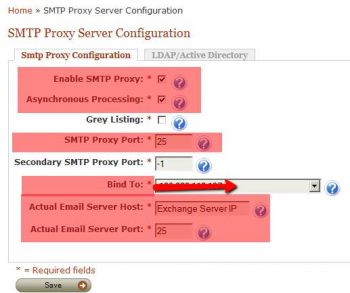
2] Under Server Configuration menu SMTP Proxy Configuration, check Enable SMTP Proxy, this enables to and fro emails passing between Exchange and Xeams.
MX record must be set on this IP
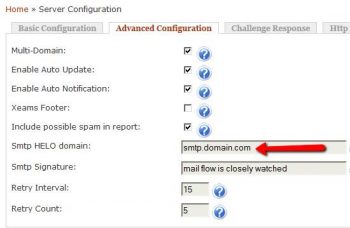
2] Advance Configuration enable Multi-Domain if the Exchange mail server is authorize to receive email for multiple domains i.e. providing email service for multiple domains.
Smtp HELO FQDN must have ‘A’ record configured on SMTP server IP.
Configuring the Exchange server to use Xeams as Spam filter firewall.
Login in to the Exchange server ECP with administrative privileges.
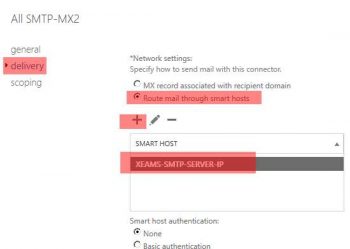
1] Under Mail-Flow configuration click on Send connector. Highlight available Send connector and edit its configuration OR add a new Send connector enabling Route mail through smart host and enter the Xeams SMTP server IP
2] In the same way make changes in ‘receive connector’ to accept emails from Xeams server IP’s (Both IPs)
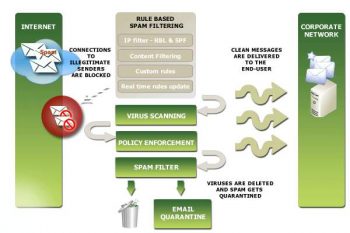
Xeams has multiple functionality that can be used as per requirement, it also gives you granular control over SPAM filter configuration like filtering email subject, attachment filter and email size, IP and domain whitelist/blacklist. All these settings can be fine-tuned using regular expression as well.















































































The last time I used Xeams, it stored all quarantined messages as flat files in one big directory. It didn’t use any kind of database to index them so searching for a message meant Xeams would open and close every single file, and this took an extraordinary amount of time.
This was several years ago, so I’d be curious to know if they’ve worked it out.
Hi Steve,
I can understand the inconvenience you might have faced. However, in latest version they have Message Repository section though which you can filter the mails on various parameters like sender email, receiver email, subject of email and even body text of that particular email in time frame.
It has great indexing system available through which you can restore the emails to respective mail boxes while updating the Bayesian database. It is very important to note here that to verify the filter rules after checking exact cause of filter/quarantine of the message.
Being open source, the pace of development on any suggestions or loopholes is greatly affected. But, it is still giving good control over spam emails. I would suggest you to check it in test environment. Best Luck !!
Hi. Nice post. I would highly appreciate if i could get some insight on how i would go about setting it up in 2 tier exchange 2013 architecture.
2 exch2013 mbx’s— 2 exch2013 CAS— Kemp Load master— Xeams
As of now all my clients are connecting to VIP on Kemp. I have installed xeams and i tried to change the autodiscover and A record DNS entries from VIP to Xeams IP . My outlook clients fail to connect internally.
I want to test this internally before i move it to production through internet aswell.
Note : No new connectors were created and the scoping on the default connectors in to receive email from 0.0.0.0 to 255.255.255.255